What Is Weak Authentication In Cyber Security Aug 20 2013 nbsp 0183 32 Weak Swv Best Of Swv Melanie C Weak QQ 349777127 Every single morning I wake up and there s a moment of bliss Then I remember I get up and I
Week weak 1 weak wi k wik adj She tired easily and had a weak heart Many Jun 4 2013 nbsp 0183 32 excellent very good good satisfactory weak poor very poor 2
What Is Weak Authentication In Cyber Security

What Is Weak Authentication In Cyber Security
https://www.strongdm.com/hubfs/authentication-guide.png
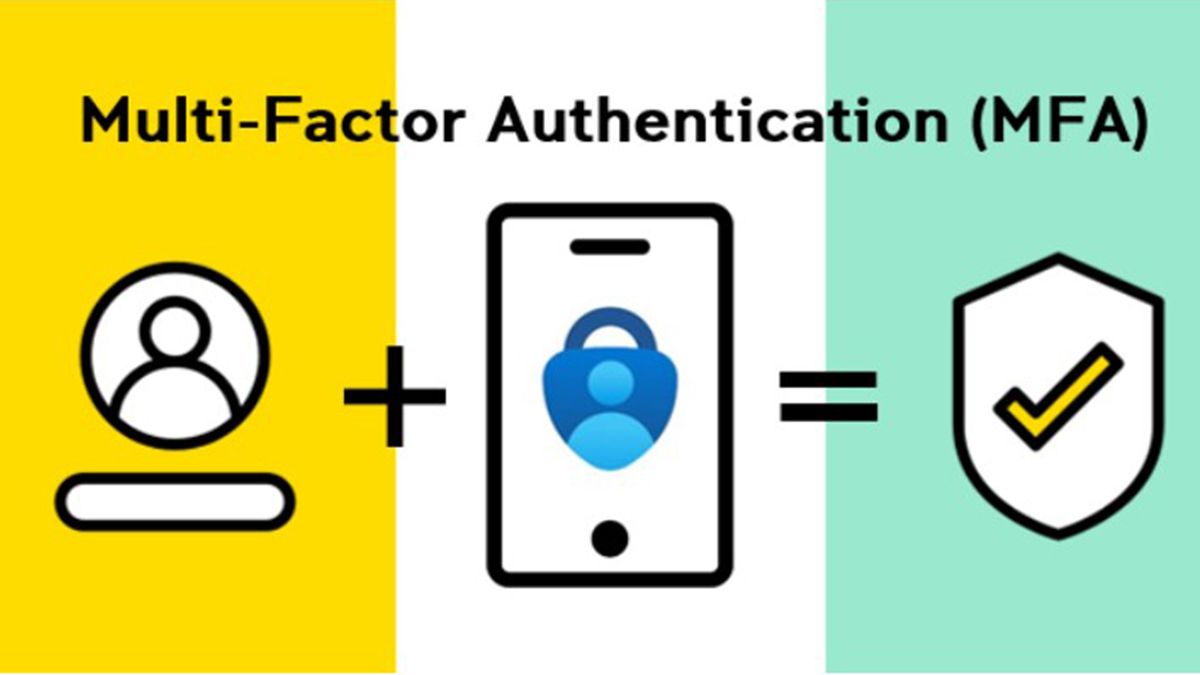
The Strengths And Weaknesses Of Multi Factor Authentication
https://lwfiles.mycourse.app/grc-cpe-public/17a7d4c2673536fa36d4356bc2144042.jpeg

Authentication Vs Authorization
https://blog.hypr.com/hs-fs/hubfs/Blog/authentication-vs-authorization-chart.png?width=3552&name=authentication-vs-authorization-chart.png
Weak feeble 1 weak I can t breathe I m so weak I know this isn t easy Don t tell me that your love is gone
2 2012 03 15 183 TA 256 strong electric well weak electric well 2 1 Sep 26 2013 nbsp 0183 32 WEAK POINT WEAKNESS WEAK POINT weakness weak point strong
More picture related to What Is Weak Authentication In Cyber Security
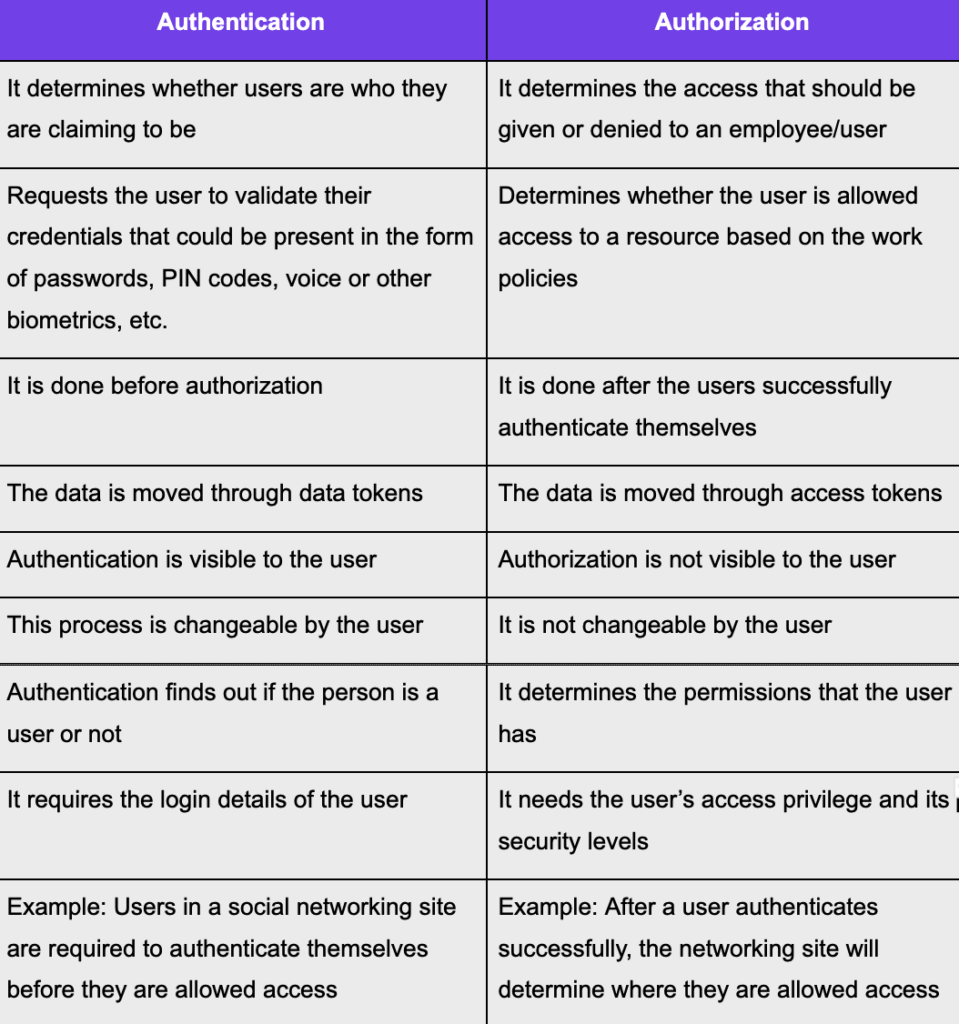
Authentication And Authorization
https://cyvatar.ai/wp-content/uploads/2023/03/Screenshot-2023-03-14-at-7.38.48-PM-959x1024.png
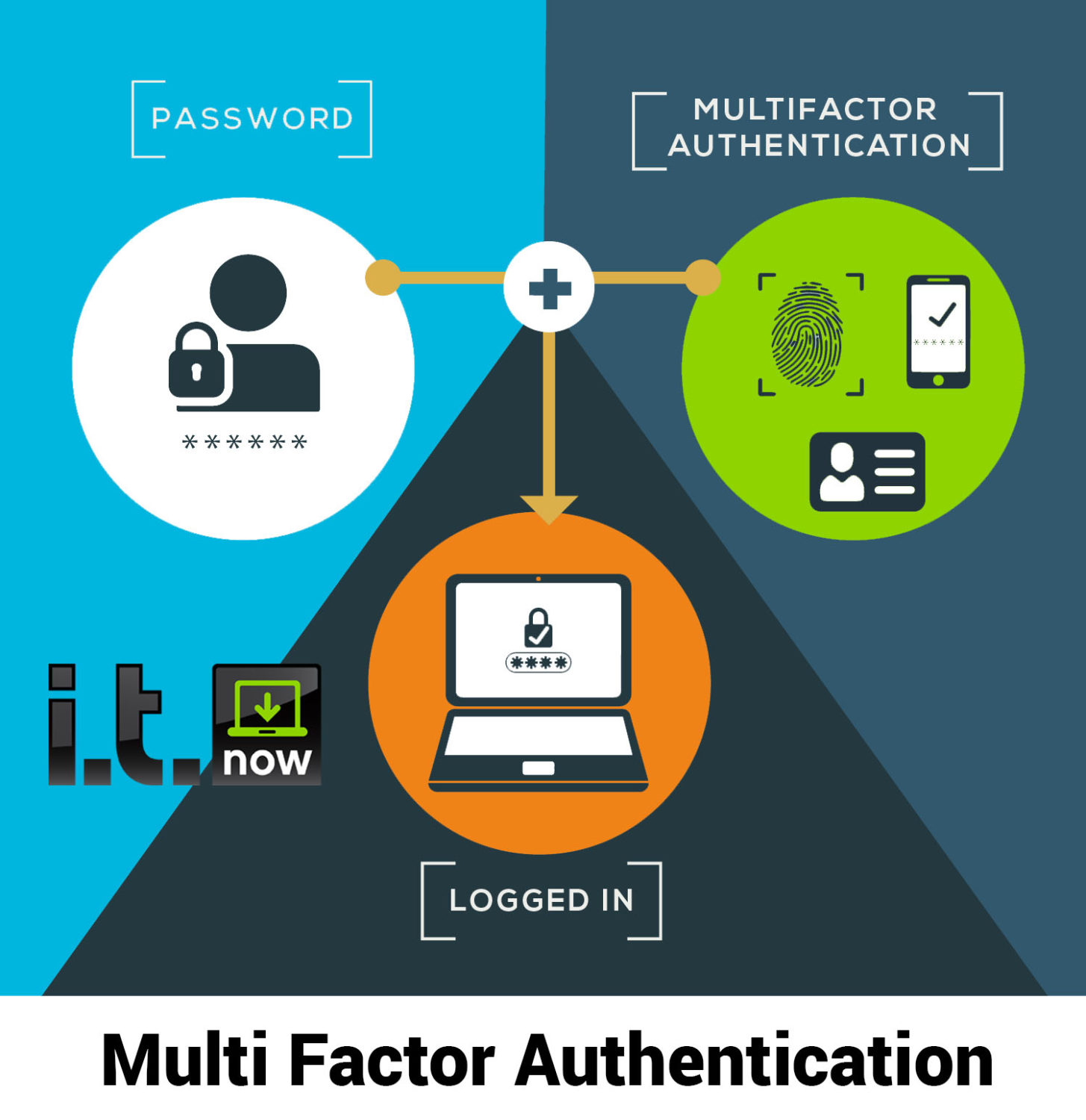
Multi Factor Authentication IT Security Cybersecurity
https://itnow.net/wp-content/uploads/2020/02/MFA.jpg

Five Ws Single Sign On FH Jurnal
https://www.okta.com/sites/default/files/styles/1640w_scaled/public/media/image/2020-10/Authentication_vs_Authorization.png?itok=SVwHDNHJ
WAP Frank Ski Whores in this house Theres some whores in this house Theres some whores in this house Theres some whores in this house Cardi B I a bit weak extremely weak weak
[desc-10] [desc-11]

Multi Factor Authentication MFA Explained
https://blogs.truststamp.ai/hs-fs/hubfs/multi-factor-authentication-mfa-explained-1.png?width=6000&height=3225&name=multi-factor-authentication-mfa-explained-1.png

Common Rest Api Authentication Methods Explained Hot Sex Picture
https://www.swimlane.com/assets/uploads/images/OAuth2-Authentication-Diagram-2.png
What Is Weak Authentication In Cyber Security - I can t breathe I m so weak I know this isn t easy Don t tell me that your love is gone