Weak Authentication In Cyber Security Geeksforgeeks Sep 26 2013 nbsp 0183 32 WEAK POINT WEAKNESS WEAK POINT weakness weak point strong
electrical amp instrument heavy current engineering intense current heavy current power current strong current I can t breathe I m so weak I know this isn t easy Don t tell me that your love is gone
Weak Authentication In Cyber Security Geeksforgeeks

Weak Authentication In Cyber Security Geeksforgeeks
https://www.onelogin.com/blog/wp-content/uploads/2023/05/advanced-authentication-blog-image.jpg.optimal.jpg

Cyber Security Domains
https://www.stationx.net/wp-content/uploads/2022/10/StationX-Cyber-Security-Domains-v1.1-2.png

Authentication Vs Authorization
https://blog.hypr.com/hs-fs/hubfs/Blog/authentication-vs-authorization-chart.png?width=3552&name=authentication-vs-authorization-chart.png
Oct 6 2024 nbsp 0183 32 weak weaker weak weaker weakest weak Dec 15 2024 nbsp 0183 32 do weak in be weak in be weak in do weak in be weak in
Weak feeble 1 weak borderline paper weak accept 2022 08 01 1505
More picture related to Weak Authentication In Cyber Security Geeksforgeeks
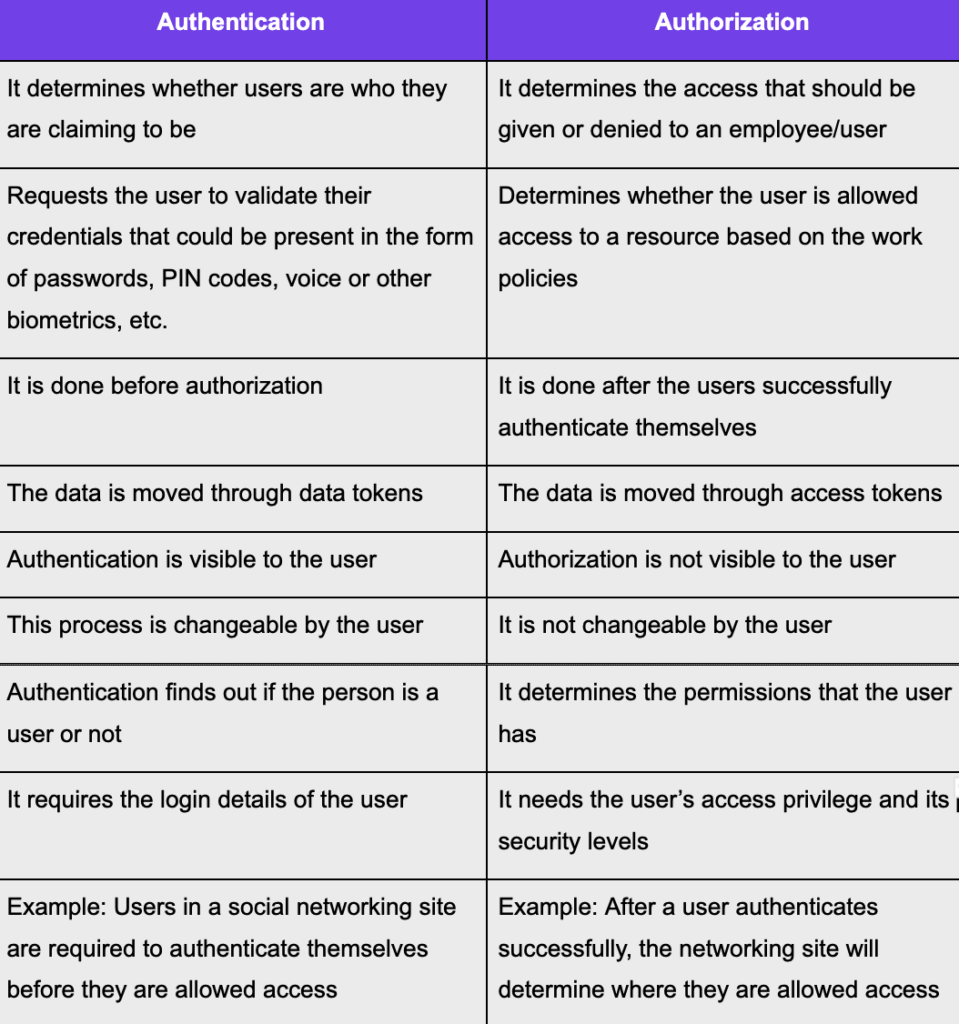
Authentication And Authorization
https://cyvatar.ai/wp-content/uploads/2023/03/Screenshot-2023-03-14-at-7.38.48-PM-959x1024.png
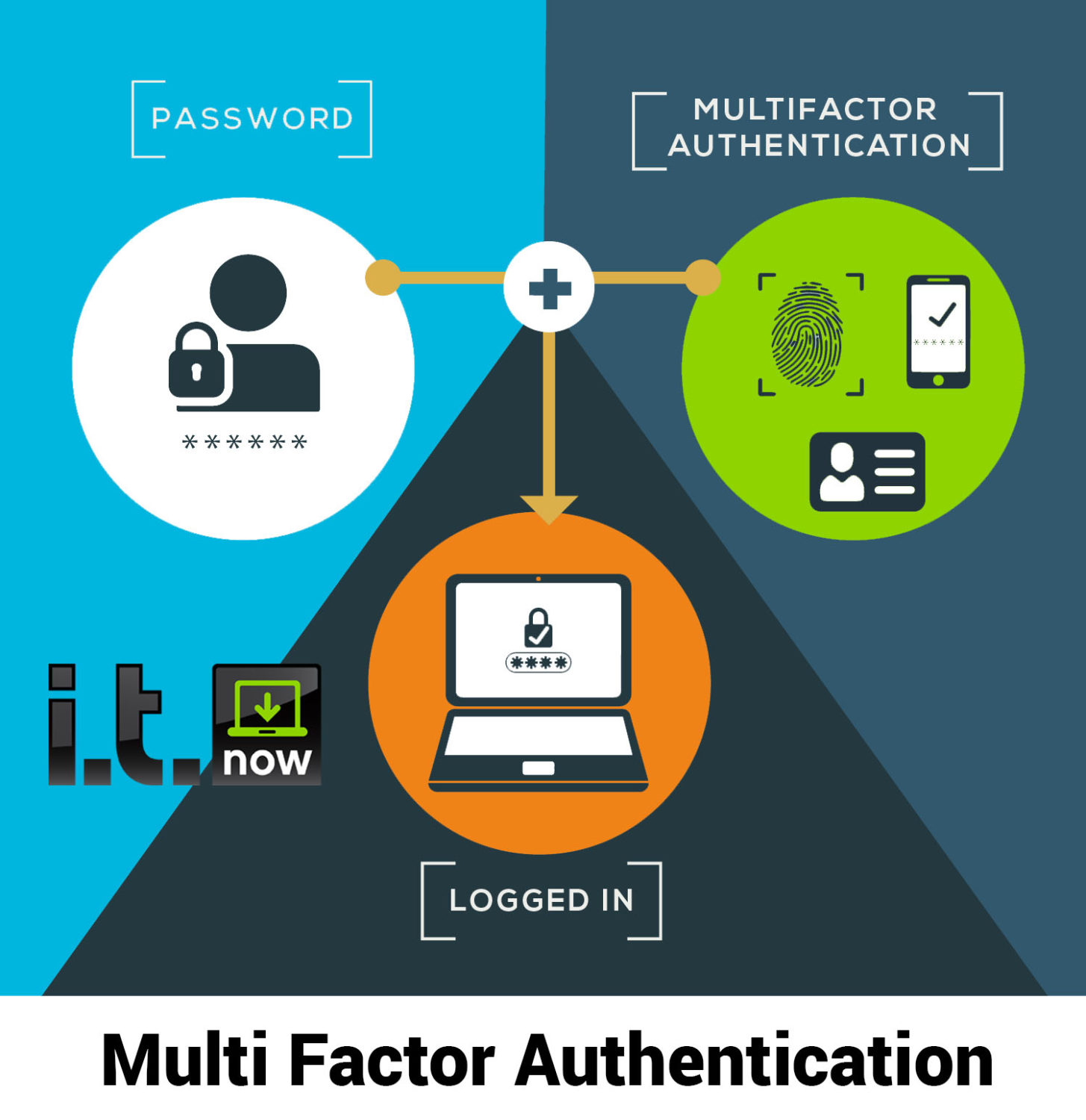
Multi Factor Authentication IT Security Cybersecurity
https://itnow.net/wp-content/uploads/2020/02/MFA.jpg
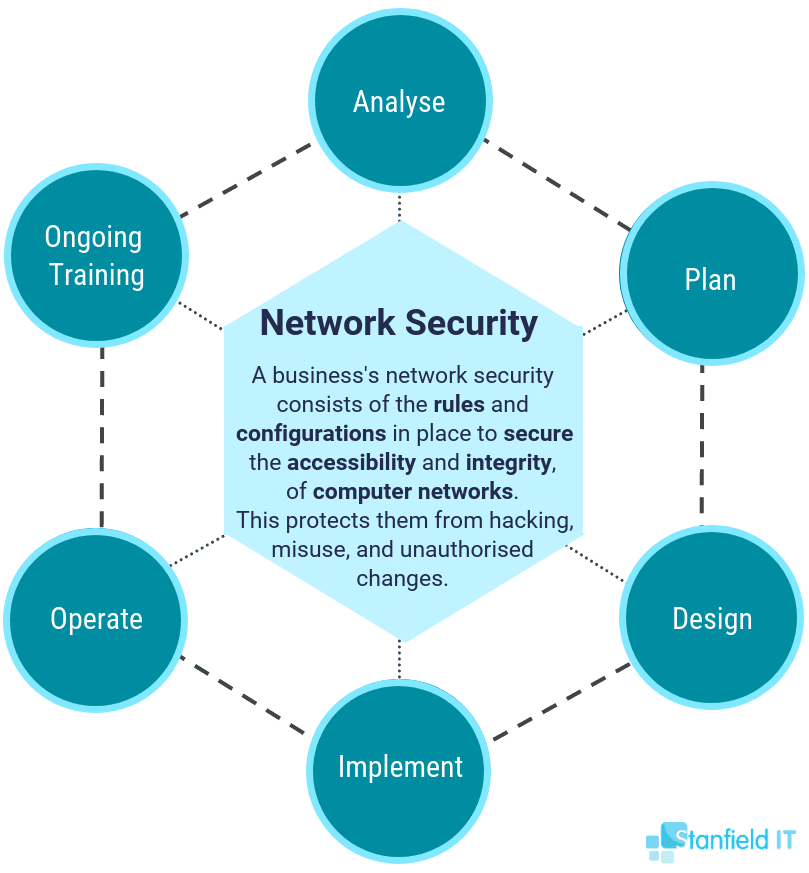
Network Security Images
https://www.stanfieldit.com/wp-content/uploads/network-security-policy.png
Mar 21 2006 nbsp 0183 32 force electricity weak electricity a bit weak extremely weak weak
[desc-10] [desc-11]

Five Ws Single Sign On FH Jurnal
https://www.okta.com/sites/default/files/styles/1640w_scaled/public/media/image/2020-10/Authentication_vs_Authorization.png?itok=SVwHDNHJ
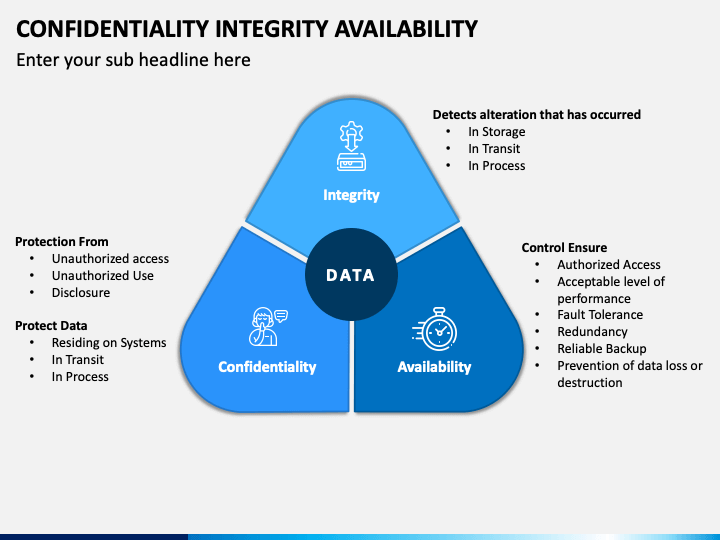
Confidentiality Integrity Availability PowerPoint Template PPT Slides
https://cdn.sketchbubble.com/pub/media/catalog/product/optimized1/5/9/597a98d99dee1d1ad6d42182caa790dac2103c51848487a1fec6cfe7b130268b/confidentiality-integrity-availability-slide1.png
Weak Authentication In Cyber Security Geeksforgeeks - [desc-13]