What Are The Defensive Skills In Basketball Facebook
Log into Facebook to start sharing and connecting with your friends family and people you know Feb 3 2025 nbsp 0183 32
What Are The Defensive Skills In Basketball

What Are The Defensive Skills In Basketball
https://i.ytimg.com/vi/44VTFRxSrM8/maxresdefault.jpg

Defensive Blocks In Football Their Special Elements YouTube
https://i.ytimg.com/vi/hdWvarnuxRc/maxresdefault.jpg

What Are The Differences With The Upcoming Sims Games
https://static1.thegamerimages.com/wordpress/wp-content/uploads/2024/05/characters-from-the-sims-4-paralives-life-by-you-and-inzoi.jpg
Feb 3 2025 nbsp 0183 32 https www facebook Enter Find out what to do if you re having trouble logging in or learn how to log out of Facebook Was this helpful
Sign up for Facebook and find your friends Create an account to start sharing photos and updates with people you know It s easy to register Log into Facebook to start sharing and connecting with your friends family and people you know
More picture related to What Are The Defensive Skills In Basketball

How To Overcome Defensiveness
https://www.choosingtherapy.com/wp-content/uploads/2022/09/2-10.png
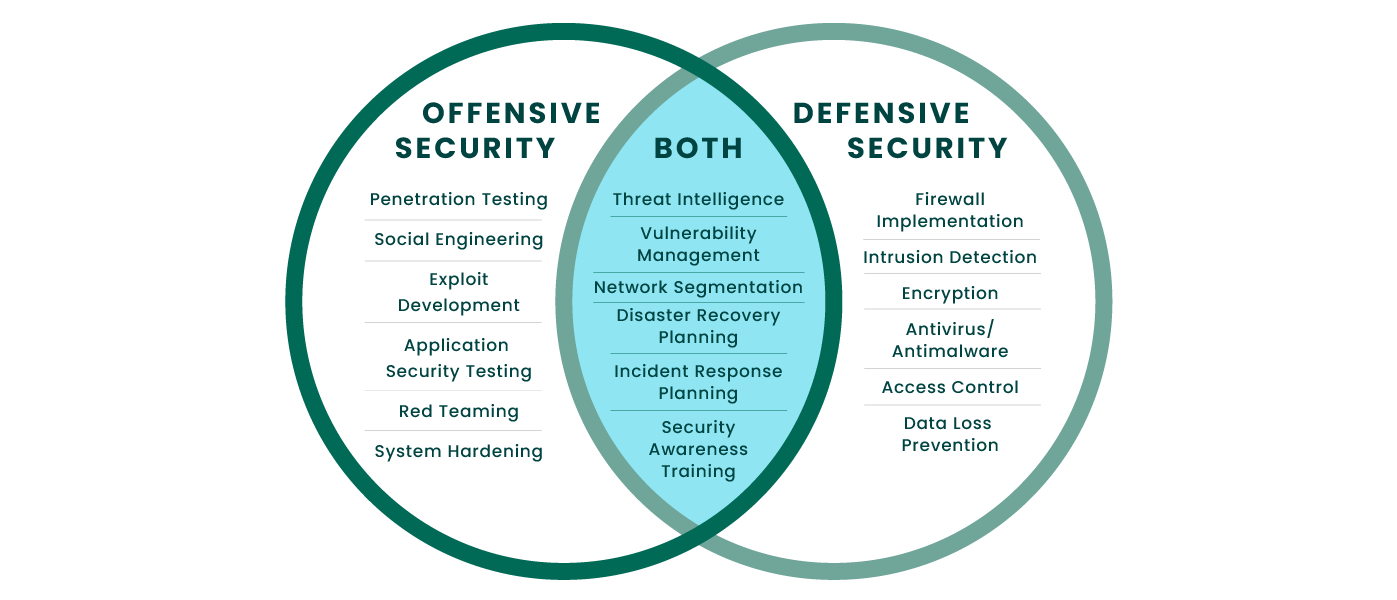
Offensive Cybersecurity Core Security
https://www.coresecurity.com/sites/default/files/2023-02/offensive-vs-defensive-cybersecurity-img.png

What Are The HIPAA Shredding Requirements Compliancy Group
https://compliancy-group.com/wp-content/uploads/2024/07/The-Guard-Features.gif
When this happens it s usually because the owner only shared it with a small group of people changed who can see it or it s been deleted Dec 17 2023 nbsp 0183 32 Facebook
[desc-10] [desc-11]

Understanding Defensive Front Alignments Football Toolbox Alignment
https://i.pinimg.com/originals/c4/ce/86/c4ce864c94946897e072d16f933d475d.jpg

How To Overcome Defensiveness
https://www.choosingtherapy.com/wp-content/uploads/2022/09/4-9-1024x1024.png
What Are The Defensive Skills In Basketball - Find out what to do if you re having trouble logging in or learn how to log out of Facebook Was this helpful