Different Authentication Methods Feb 7 2025 nbsp 0183 32 Authentication methods including challenge handshake authentication protocol CHAP extensible authentication protocol EAP and HTTP basic authentication are crucial for verifying the identity of users or
Jun 11 2024 nbsp 0183 32 Let s look at the various types of authentication methods available 1 Single Factor Authentication A single credential such as a password or PIN is used in single factor There are lots of authentication methods out there but they all generally fall under the following 5 types Username and password Requires a username and password Multi factor authentication Requires multiple authentication layers
Different Authentication Methods
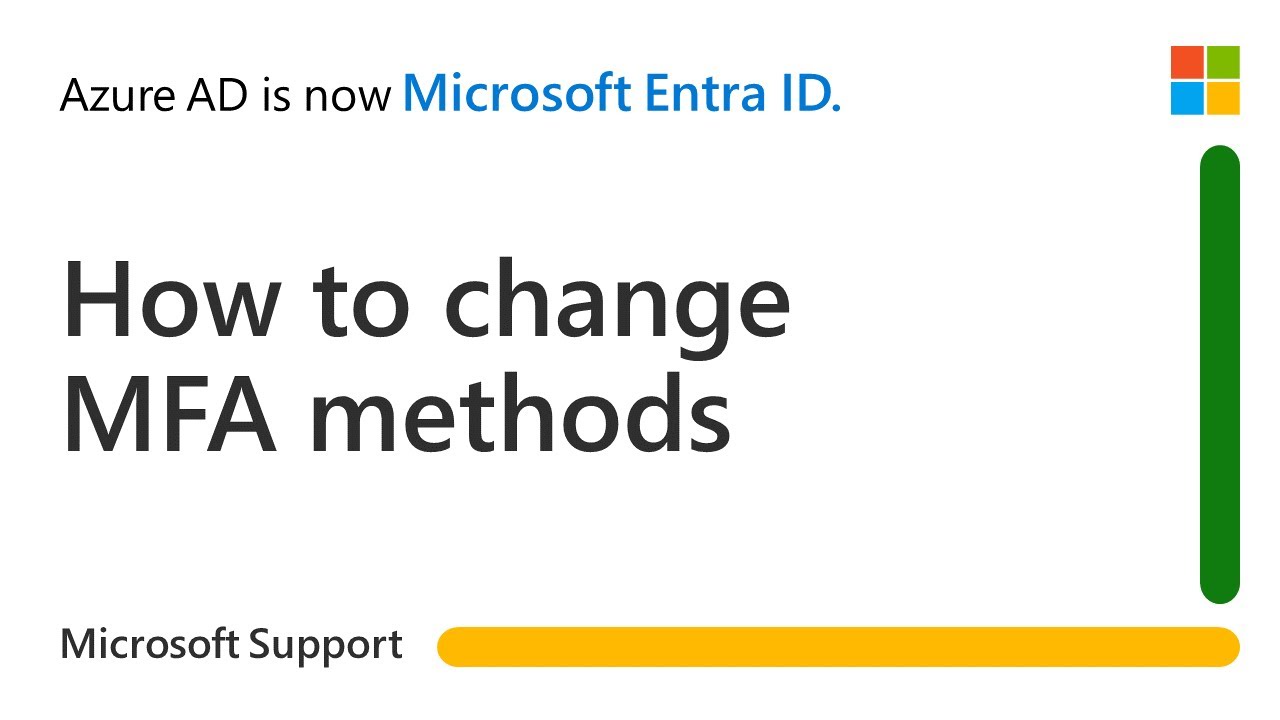
Different Authentication Methods
https://i.ytimg.com/vi/vzKugABBxsk/maxresdefault.jpg

Authenticate
https://www.iproov.com/wp-content/uploads/2021/09/best-authentication-methods-v3-ai-1.png
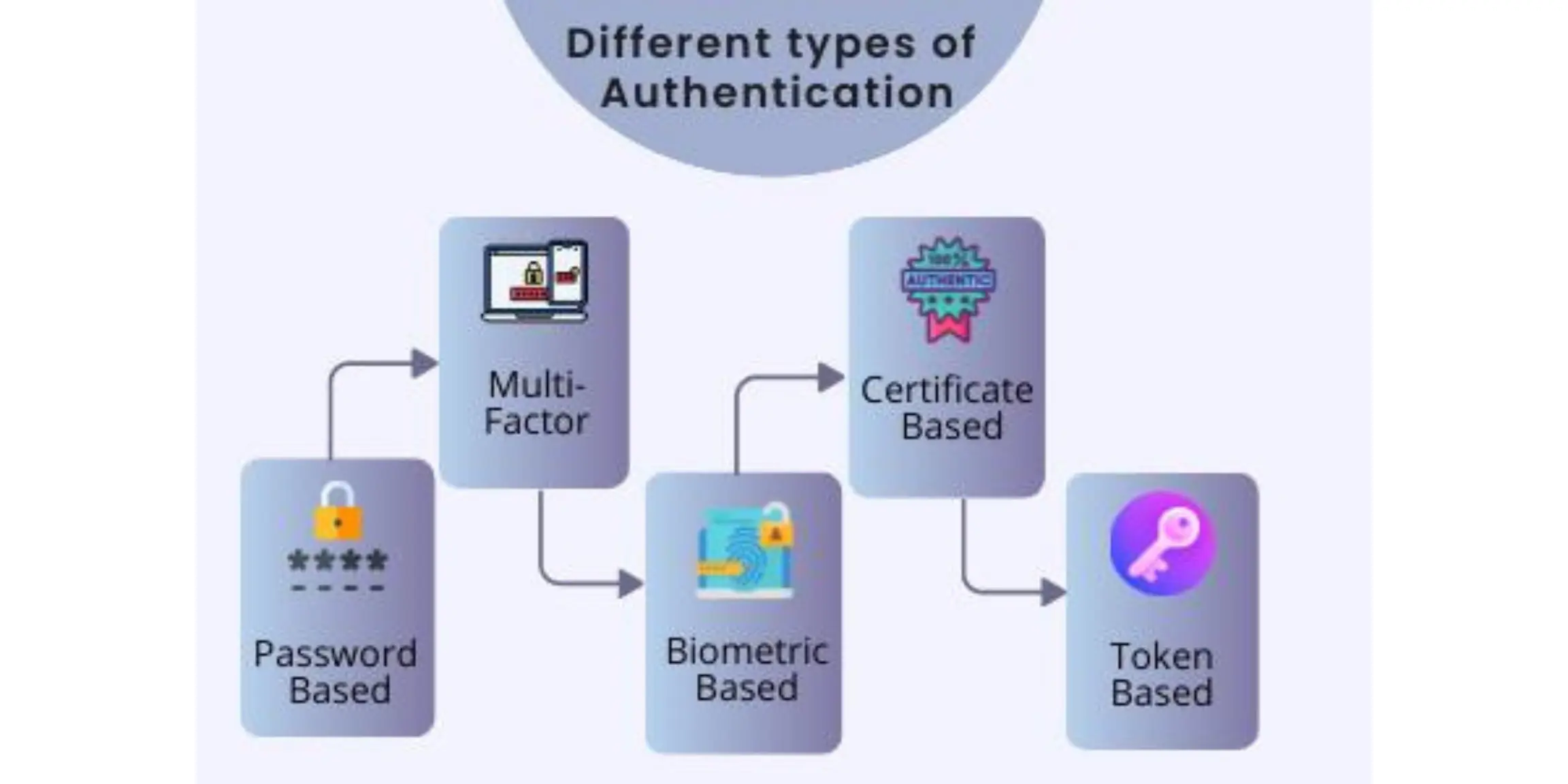
Authentification
https://www.miniorange.com/blog/assets/2023/different-types-of-authentication.webp
Oct 28 2024 nbsp 0183 32 Dive into the evolution of authentication methods from biometric and passwordless solutions to multi factor authentication Learn how Arya AI APIs fortify cybersecurity for seamless onboarding and risk mitigation Jul 11 2022 nbsp 0183 32 In this blog we will explore the most common authentication protocols and will try to explore their merits and demerits 1 Kerberos Kerberos is a protocol that aids in network authentication This is used for validating
Let s understand different authentication methods strengths weaknesses as well as guidelines to adoption of the same for the purpose of security in the digital realm The mechanism of Jun 24 2024 nbsp 0183 32 However it can be difficult to choose from so many different authentication methods So to help you make the right decision for your app and organizations we ll explore the most prevalent types of authentication from
More picture related to Different Authentication Methods

Authentication Images
https://optimalidm.com/wp-content/uploads/2020/06/Common-Authentication-Methods-REV01.png
Authentication Acompanhe O EC S o Bernardo
https://www.infosectrain.com/wp-content/uploads/2023/12/Types-of-Authentication.jpg
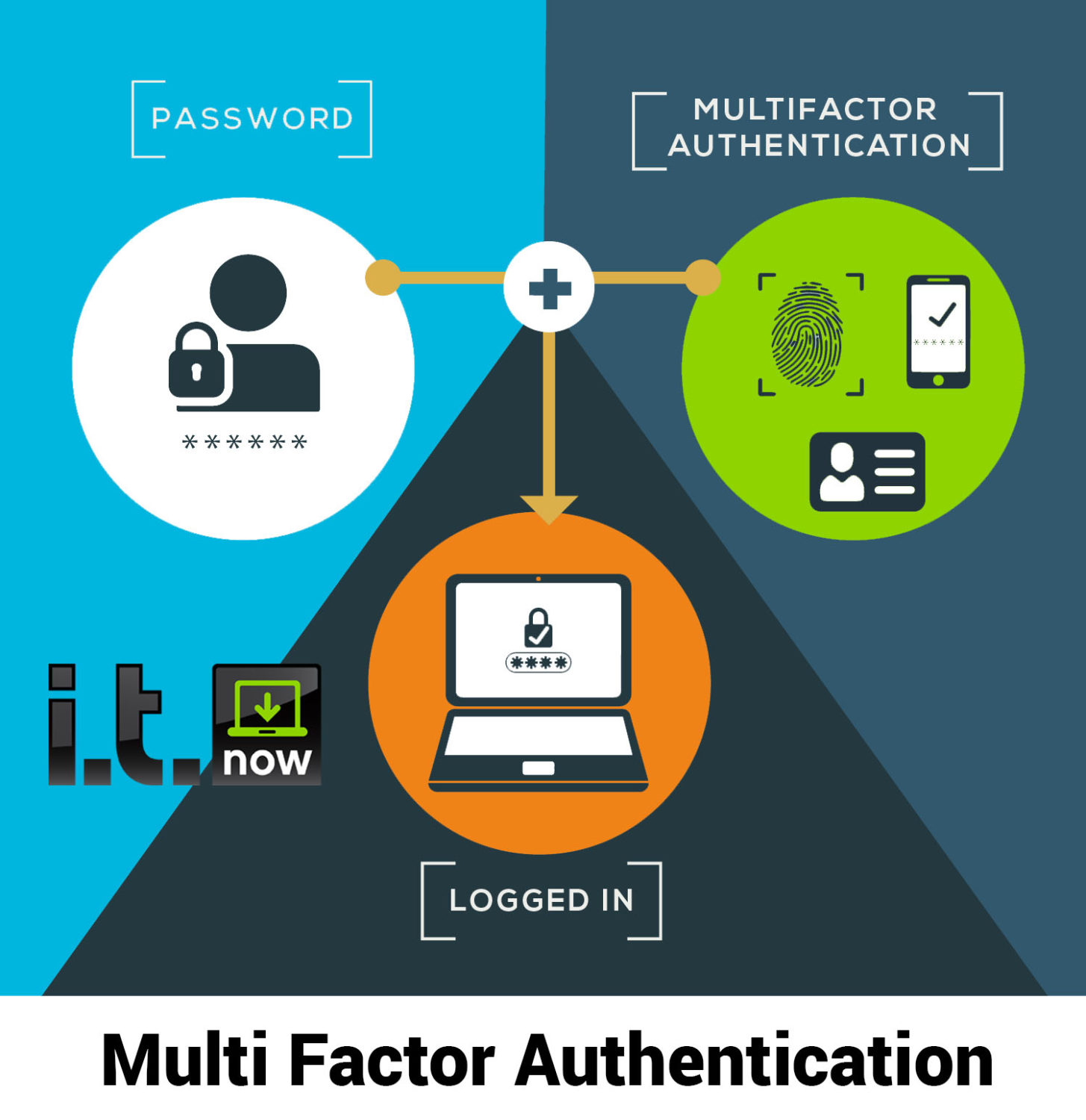
Multi Factor Authentication IT Security Cybersecurity
https://itnow.net/wp-content/uploads/2020/02/MFA.jpg
Oct 31 2023 nbsp 0183 32 Learn about Authentication Different types of Authentication methods and how to implement them in your company to ensure your users always have proper access considering cybersecurity Mar 18 2024 nbsp 0183 32 Web app authentication involves several methods including cookies JWT OAuth API Token SAML and OpenID Depending on the use case and the security requirements they have various advantages and
Jan 2 2025 nbsp 0183 32 Effective user authentication methods protect sensitive information and prevent unauthorized access Verifying user identity also helps prevent identity theft and 6 days ago nbsp 0183 32 Discover various MFA methods including passkeys hardware token authentication and biometrics Learn how multi factor authentication strengthens cybersecurity Definition
![]()
Premium Vector Infographic Authentication Template Icons In Different
https://img.freepik.com/premium-vector/infographic-authentication-template-icons-different_676904-5119.jpg?w=2000

Multi Factor Authentication MFA Explained
https://blogs.truststamp.ai/hs-fs/hubfs/multi-factor-authentication-mfa-explained-1.png?width=6000&height=3225&name=multi-factor-authentication-mfa-explained-1.png
Different Authentication Methods - Let s understand different authentication methods strengths weaknesses as well as guidelines to adoption of the same for the purpose of security in the digital realm The mechanism of