Three Authentication Methods Jan 23 2024 nbsp 0183 32 Pocket 3
Apr 11 2019 nbsp 0183 32 I love three things in this world Sun Moon and You sun for morning Moon for night and you forever 2011 1
Three Authentication Methods

Three Authentication Methods
https://metadata-static.plex.tv/c/gracenote/c193a8b596a5f9b36a2d172fd8d5d267.jpg

Multifactor Authentication
https://www.nist.gov/sites/default/files/images/2019/09/25/multifactor-authentificaton.png

Smith County Busted List
https://darkhorsepressnow.com/wp-content/uploads/2022/09/smithcountypossession-1267x1536.jpg
4321 four three two one four thousand three hundred and twenty one In the above example income level could be split into three levels low middle and high income Gender could be split into three levels male female and transgender
Three js 2009 4 JavaScript ActionScript WebGL three js WebGL 224 193 31
More picture related to Three Authentication Methods

Authentication
https://optimalidm.com/wp-content/uploads/2020/06/04-what-is-the-most-secure-type-of-authentication-method.jpg
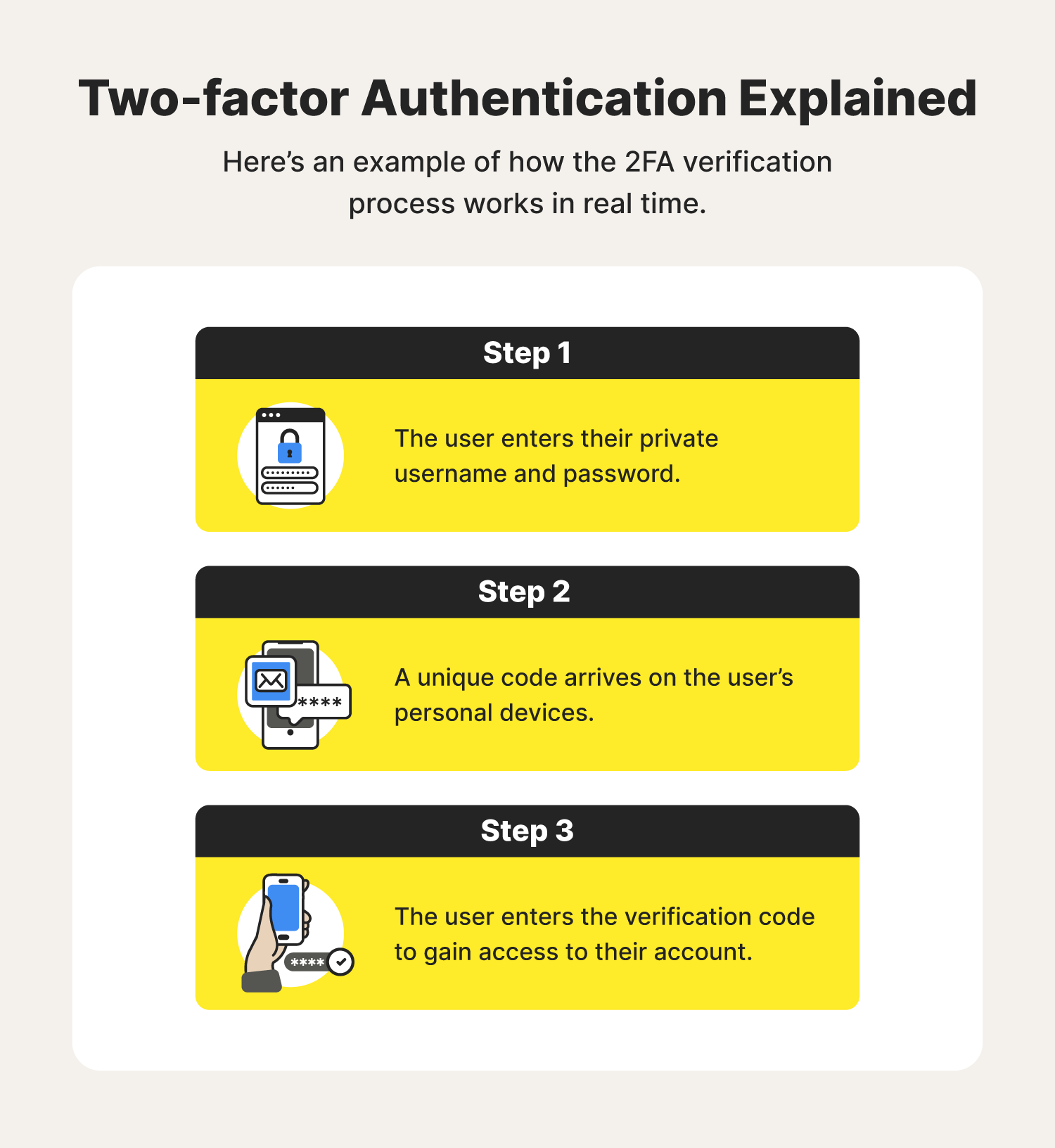
Authentication
https://us.norton.com/content/dam/blogs/images/norton/am/two-factor-authentication-explained.png

Authentication Images
https://optimalidm.com/wp-content/uploads/2020/06/Common-Authentication-Methods-REV01.png
No more than three words and or a number 3 3 No more than three words and or Sep 1 2021 nbsp 0183 32 The three potential referees including the names addresses and e mail addresses are listed as follow 1 XXX School of Natural Resources and
[desc-10] [desc-11]

Koa Template Overview Advanced Communities
https://advancedcommunities.com/wp-content/uploads/2019/06/desktop-55-3-2.png
Biometric Authentication
https://images.ctfassets.net/23aumh6u8s0i/6MQMwDdaUKU1w1uTWkkRZc/faca51a20b078f6bdb75b73502a92b15/cybersecurity_finger
Three Authentication Methods - [desc-12]
