What Is Authentication In The Information Security Context Mar 30 2013 nbsp 0183 32 Authentication is the preferred form in English The variant authentification is acceptable but less common it s often used by non native speakers who aren t aware that it s
2011 1
What Is Authentication In The Information Security Context

What Is Authentication In The Information Security Context
https://i.ytimg.com/vi/nmzEmrVWGQw/maxresdefault.jpg

Authenticate
https://www.iproov.com/wp-content/uploads/2021/09/best-authentication-methods-v3-ai-1.png

Multifactor Authentication
https://www.nist.gov/sites/default/files/images/2019/09/25/multifactor-authentificaton.png
UPnP iOS18 4 1
Biometrics refers to metrics related to human characteristics Biometrics authentication or realistic authentication is used in computer science as a form of identification and access Mar 7 2024 nbsp 0183 32 Stack Exchange Network Stack Exchange network consists of 183 Q amp A communities including Stack Overflow the largest most trusted online community for
More picture related to What Is Authentication In The Information Security Context

Setting Authentication Preferences Vrogue co
https://www.strongdm.com/hubfs/authentication-guide.png

Authentication Images
https://optimalidm.com/wp-content/uploads/2020/06/Common-Authentication-Methods-REV01.png

Authentication Vs Authorization
https://blog.hypr.com/hs-fs/hubfs/Blog/authentication-vs-authorization-chart.png?width=3552&name=authentication-vs-authorization-chart.png
Aug 25 2021 nbsp 0183 32 For me access might only refer to a website that I need to log in to use such as access your account on our site There s a hint of required authentication to the meaning in I have to say first that consequentially is a pretty rare word My advice would be to steer well clear of it because nearly every time you use it people will assume you re making a mistake and
[desc-10] [desc-11]

Biometric Authentication
https://web-assets.esetstatic.com/wls/2022/09/biometric-authentication-how-it-works-pros-cons.jpg
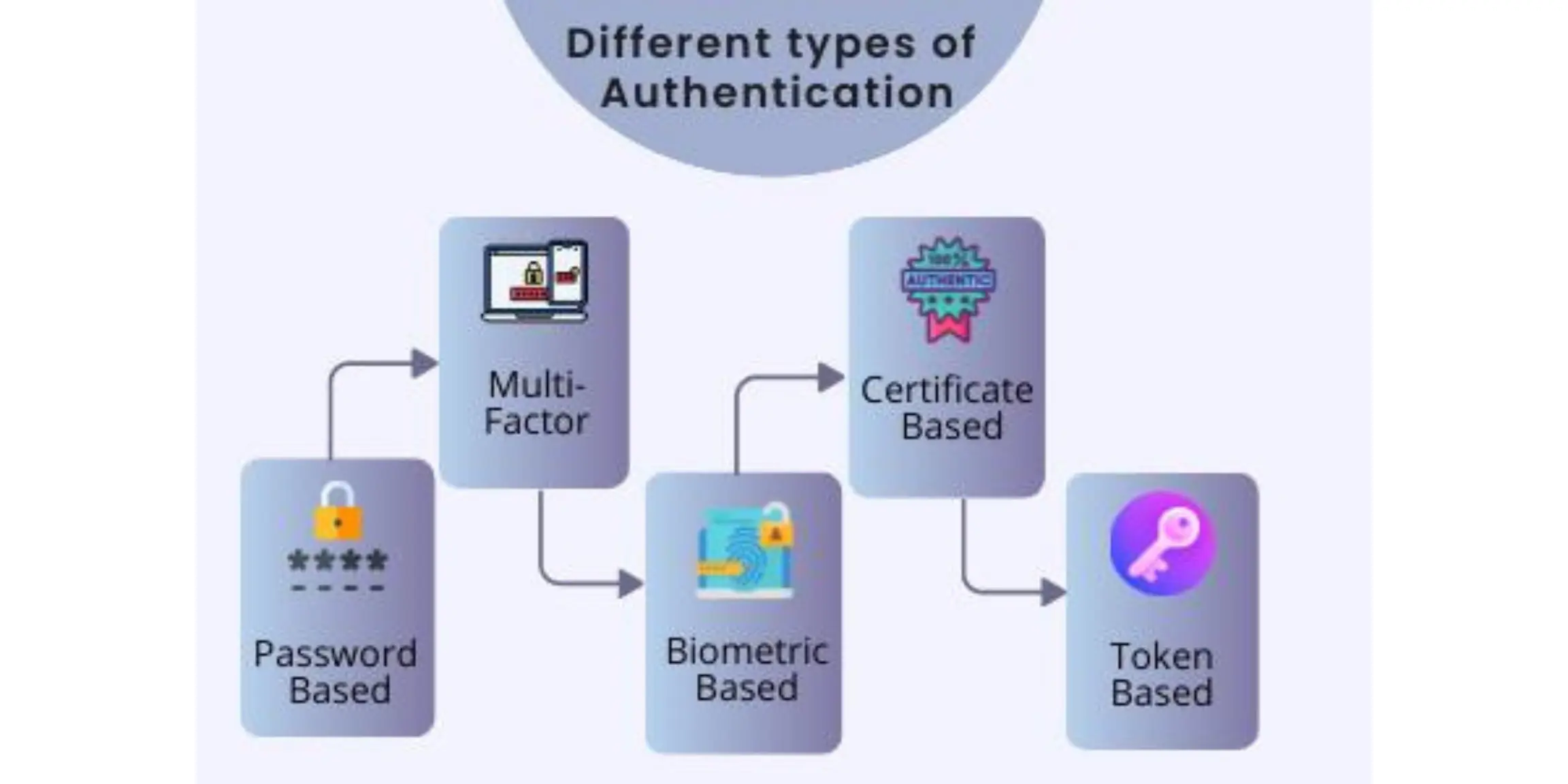
Authentication Acompanhe O EC S o Bernardo
https://www.miniorange.com/blog/assets/2023/different-types-of-authentication.webp
What Is Authentication In The Information Security Context - Biometrics refers to metrics related to human characteristics Biometrics authentication or realistic authentication is used in computer science as a form of identification and access