What Is Authentication In Cyber Security With Example Mar 30 2013 nbsp 0183 32 Authentication is the preferred form in English The variant authentification is acceptable but less common it s often used by non native speakers who aren t aware that it s
cursor deepseek API CURSOR sign in Can t verify t
What Is Authentication In Cyber Security With Example
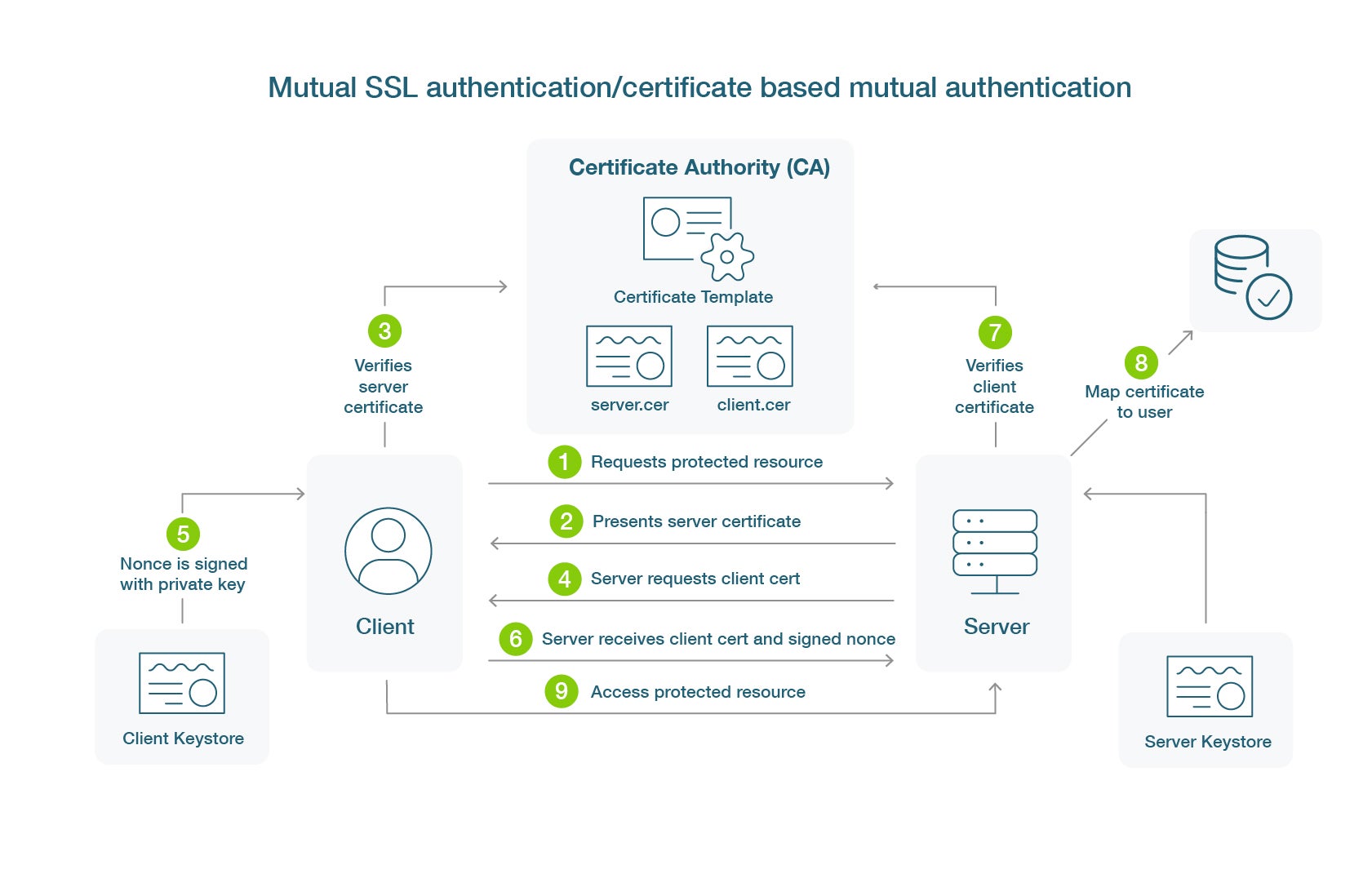
What Is Authentication In Cyber Security With Example
https://www.yubico.com/wp-content/uploads/2023/03/315-Website-improvement-suggestions-on-CBA-page-r1-100-1-1.jpg

Authenticate
https://www.iproov.com/wp-content/uploads/2021/09/best-authentication-methods-v3-ai-1.png

Common Auth
https://www.okta.com/sites/default/files/styles/1640w_scaled/public/media/image/2020-10/Authentication_vs_Authorization.png?itok=uBFRCfww
1 5552 WiFi3 QAQ hosts ping
Sep 28 2019 nbsp 0183 32 github github github jetbrain github jetbrain
More picture related to What Is Authentication In Cyber Security With Example
Editable Technology Presentation Templates In PowerPoint To Download
https://images.template.net/140759/cyber-security-presentation-template-sr5wq.jpg

Pin Auf Gurzaib Art
https://i.pinimg.com/originals/3b/eb/31/3beb31f6fdc867f4e2769b330e8b74f1.jpg

Pin On Visualizations
https://i.pinimg.com/originals/ae/de/d5/aeded56496b029d6b92aab457dbe384b.jpg
push public private 1 1 0 2 unauthorized authentication Microsoft
[desc-10] [desc-11]

Authentication Security
https://www.strongdm.com/hubfs/authentication-guide.png

Authentication Vs Authorization
https://blog.hypr.com/hs-fs/hubfs/Blog/authentication-vs-authorization-chart.png?width=3552&name=authentication-vs-authorization-chart.png
What Is Authentication In Cyber Security With Example - [desc-13]