What Is A Key Vulnerability Associated With Broken Authentication Jul 27 2023 nbsp 0183 32 key Key Key VISUAL ARTS
Nov 29 2020 nbsp 0183 32 Key gal 18r 18r Meilleure r 233 ponse Si le fichier key est une pr 233 sentation keynote il suffit de changer le nom du fichier et rajouter zip pour pouvoir acc 233 der 224 son contenu Si le fichier key est une cl 233 pour
What Is A Key Vulnerability Associated With Broken Authentication

What Is A Key Vulnerability Associated With Broken Authentication
https://i.ytimg.com/vi/wC-YoDoKFls/maxresdefault.jpg

What Is Risk Threat And Vulnerability Relationship Between Risk
https://i.ytimg.com/vi/wKL5o4NEWr4/maxresdefault.jpg

Security Assessments Ferraris Investigations Consulting LLC
https://www.ferrarisinvestigations.com/wp-content/uploads/Security-Assessment.jpg
Jan 21 2024 nbsp 0183 32 key key 1 key 2 key Summer Pockets key
key key Oct 14 2024 nbsp 0183 32 Office2021 1 Office 2021 2 Office 2021 KEY PR32N T9VDV TTDT2 2C2VB R634X3 Office 2021 for mac
More picture related to What Is A Key Vulnerability Associated With Broken Authentication

What Is Vulnerability Disclosure Types Process Guidelines
https://sprinto.com/wp-content/uploads/2023/06/Vulnerability-Disclosure-Policy-Guidelines-and-Process.jpg

Vulnerability Scanning WebCheck Security
https://static.wixstatic.com/media/54de26_f2053a4133854230a045ddfe07483467~mv2.jpg/v1/fill/w_4000,h_2666,al_c/54de26_f2053a4133854230a045ddfe07483467~mv2.jpg
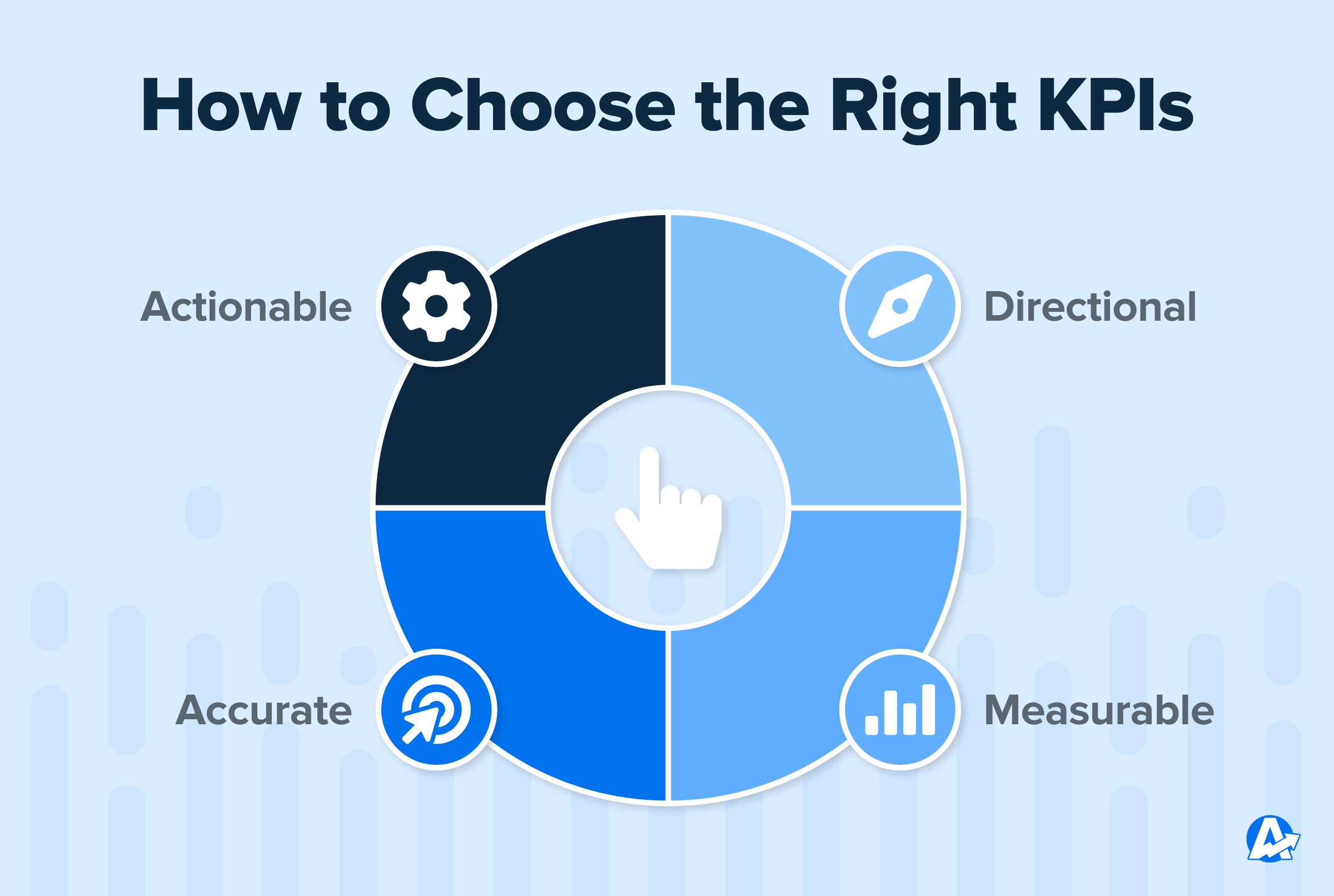
Key Performance Indicator KPI Definition Types And 55 OFF
https://images.ctfassets.net/dfcvkz6j859j/1BGoyAu7N61hACfpTuze3U/9eae09506a08dac01b5f46f5526dd67b/Choose_Right_KPIs_pie_chart.png
Nov 1 2024 nbsp 0183 32 Key PPT Mac Keynote Keynote Key Sep 26 2024 nbsp 0183 32 office2010 office2010 1 Office 2010 Office 2010 Professional Plus Retail Key C6YV2
[desc-10] [desc-11]
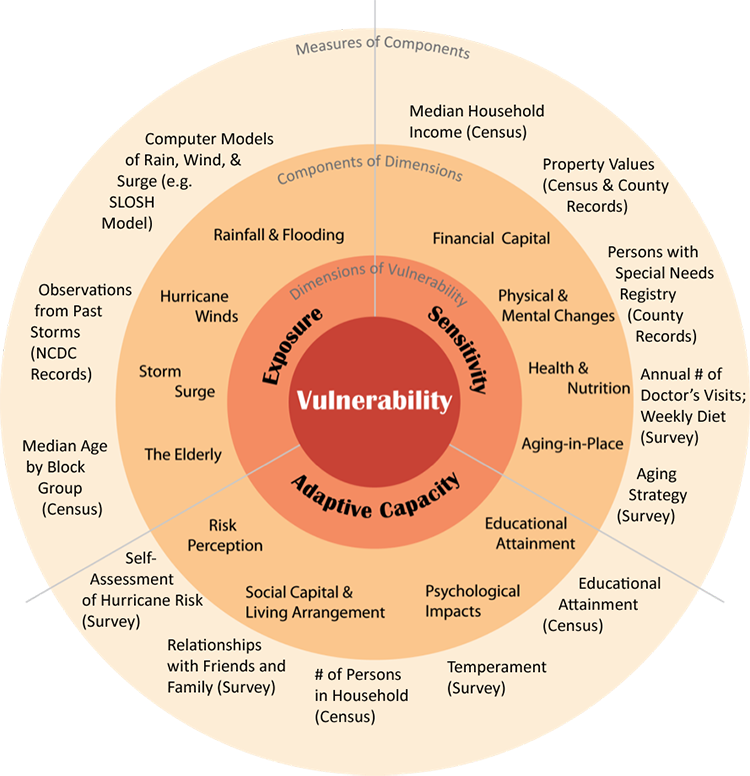
Assessing Vulnerability The Vulnerability Scoping Diagram Coastal
https://www.e-education.psu.edu/earth107/sites/www.e-education.psu.edu.earth107/files/Unit4/Mod10/image7.png

Vulnerability Assessment Lanworks
https://www.lanworks.com/wp-content/uploads/2020/08/vulnerability-2048x1811.png
What Is A Key Vulnerability Associated With Broken Authentication - [desc-14]