Security Vulnerability Assessment Example La seguridad inform 225 tica protege los sistemas inform 225 ticos las redes y los datos digitales de una organizaci 243 n contra el acceso no autorizado las filtraciones de datos los ataques cibern 233 ticos y otras actividades maliciosas
Jan 27 2025 nbsp 0183 32 What is tokenization In data security tokenization is the process of converting sensitive data into a nonsensitive digital replacement called a token that maps back to the original Tokenization can help protect sensitive information For example sensitive data can be mapped to a token and placed in a digital vault for secure storage Jul 30 2025 nbsp 0183 32 Just how much are data breaches costing these days Explore the 2025 Cost of a Data Breach Report to learn the average costs AI s impact on the security landscape and more
Security Vulnerability Assessment Example
Security Vulnerability Assessment Example
https://sparklingstemware.com/wp-content/uploads/2021/08/fresh-vulnerability-management-program-template-scaled.jpg

Vulnerability Assessment Lanworks
https://www.lanworks.com/wp-content/uploads/2020/08/vulnerability-2048x1811.png
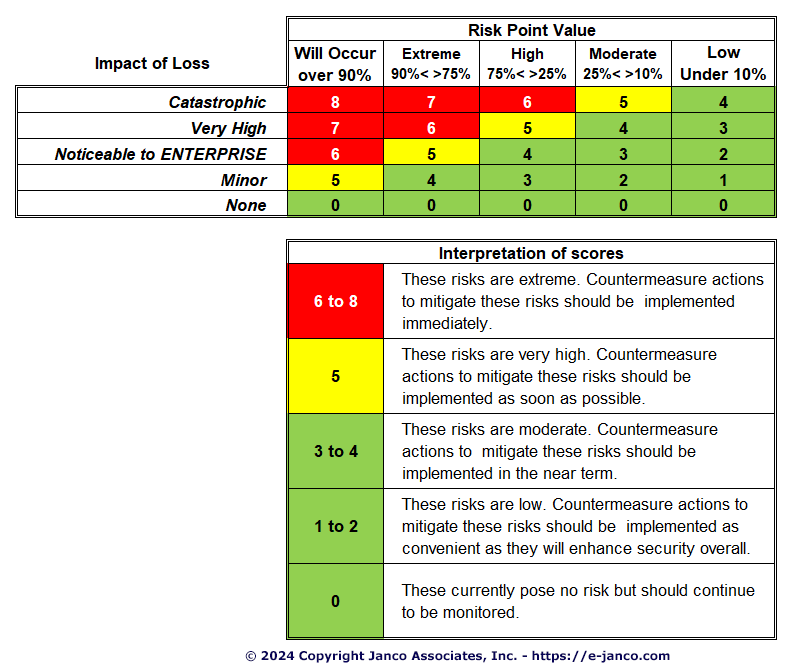
Threat Vulnerability Assessment Tool
https://www.e-janco.com/images/ThreatAssessmentSample.PNG
May 15 2025 nbsp 0183 32 AI security uses artificial intelligence AI to enhance an organization s security posture IBM s global Cost of a Data Breach Report 2025 provides up to date insights into cybersecurity threats and their financial impacts on organizations
Apr 7 2025 nbsp 0183 32 Most of us think of cybersecurity as a purely digital affair but cyberattacks can actually begin right here in the physical world Manage the security risk of sensitive AI data and AI models including AI agents Bring together siloed security and governance teams
More picture related to Security Vulnerability Assessment Example

Cyber Risk Matrix Vrogue co
https://www.slideteam.net/media/catalog/product/cache/1280x720/c/y/cybersecurity_risk_analysis_and_management_plan_risk_assessment_matrix_with_vulnerability_and_threat_slide01.jpg
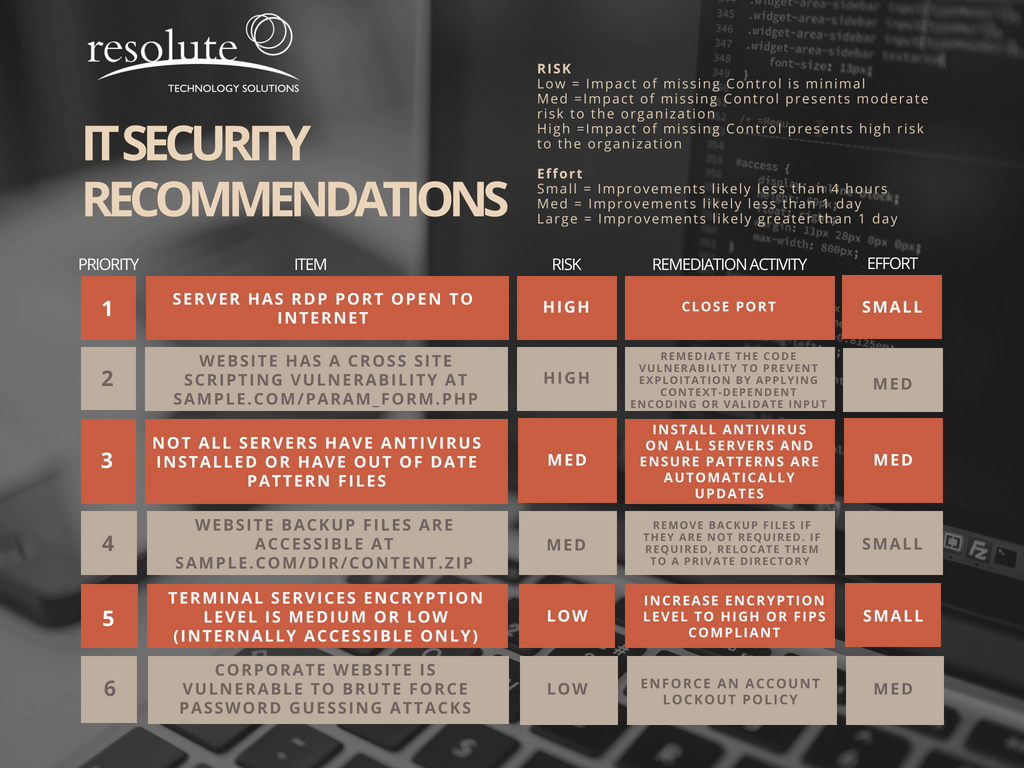
IT Security Vulnerability Assessment Resolute Technology Solutions
https://www.resolutets.com/wp-content/uploads/2018/07/Vulnerability_-Security-Recommendations.jpg

Vulnerability Assessment Process
https://thecyphere.com/wp-content/uploads/2023/05/Vulnerability-Assessments.png
Jul 26 2024 nbsp 0183 32 Information security InfoSec is the protection of important information against unauthorized access disclosure use alteration or disruption ZDNET news and advice keep professionals prepared to embrace innovation and ready to build a better future
[desc-10] [desc-11]
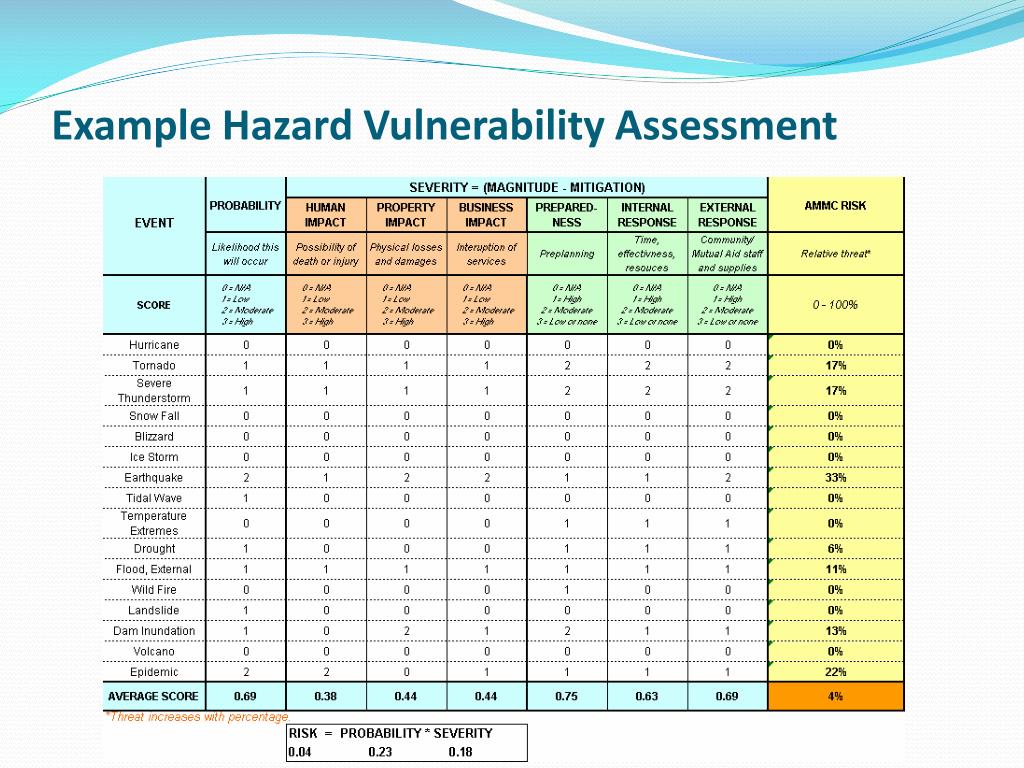
Hazard Vulnerability Analysis Template Vrogue co
https://image.slideserve.com/239327/example-hazard-vulnerability-assessment-l.jpg
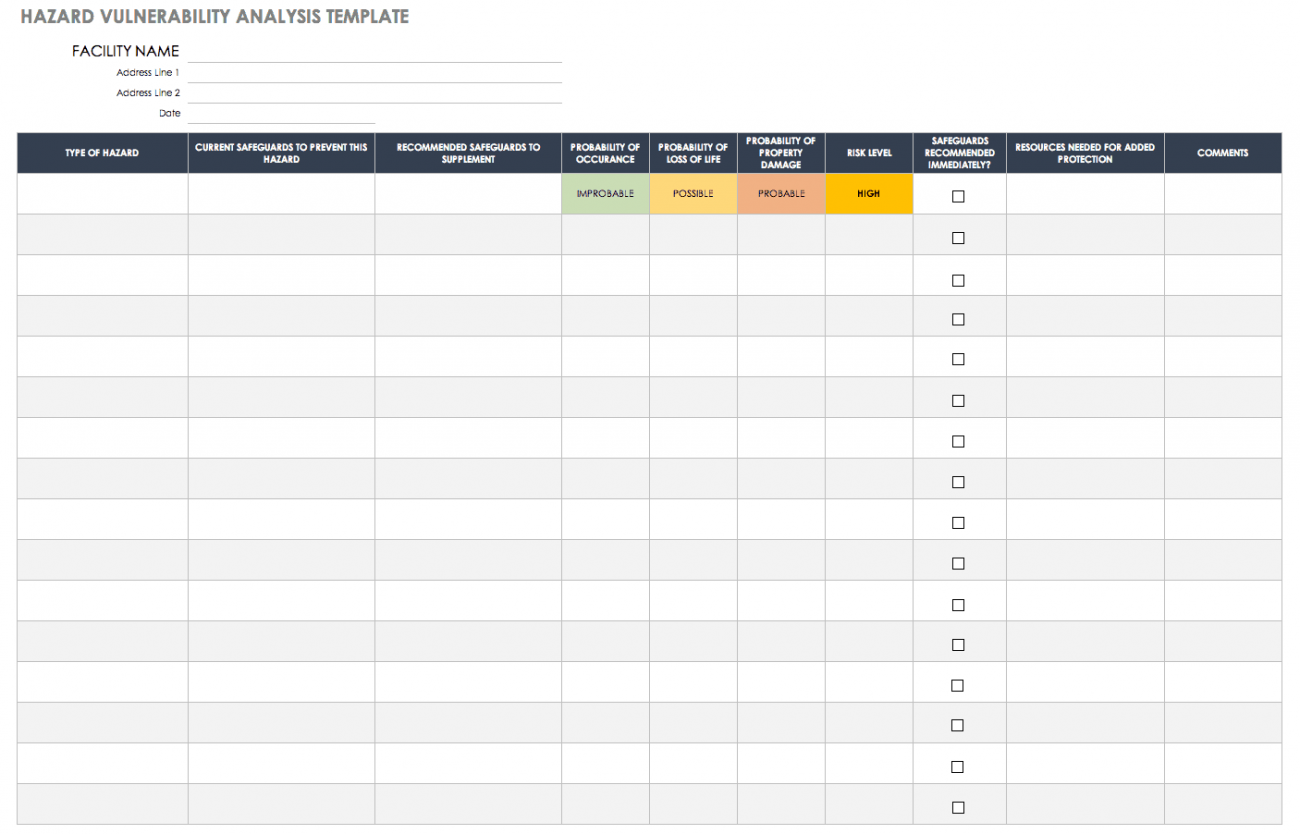
Hazard Vulnerability Analysis Template Vrogue co
https://www.smartsheet.com/sites/default/files/styles/1300px/public/IC-Hazard-Vulnerability-Analysis-Template.png?itok=-A1P_Qf3
Security Vulnerability Assessment Example - [desc-14]