Security Swot Analysis Example Jun 1 2023 nbsp 0183 32 What is IT security IT security which is short for information technology security is the practice of protecting an organization s IT assets computer systems networks digital devices data from unauthorized access data breaches
IBM s global Cost of a Data Breach Report 2025 provides up to date insights into cybersecurity threats and their financial impacts on organizations IBM Security develops intelligent enterprise security solutions and services to help your business prepare today for the cybersecurity threats of tomorrow
Security Swot Analysis Example

Security Swot Analysis Example
https://i.pinimg.com/originals/6c/f4/21/6cf421d199183464a361eb46cd55adc6.png
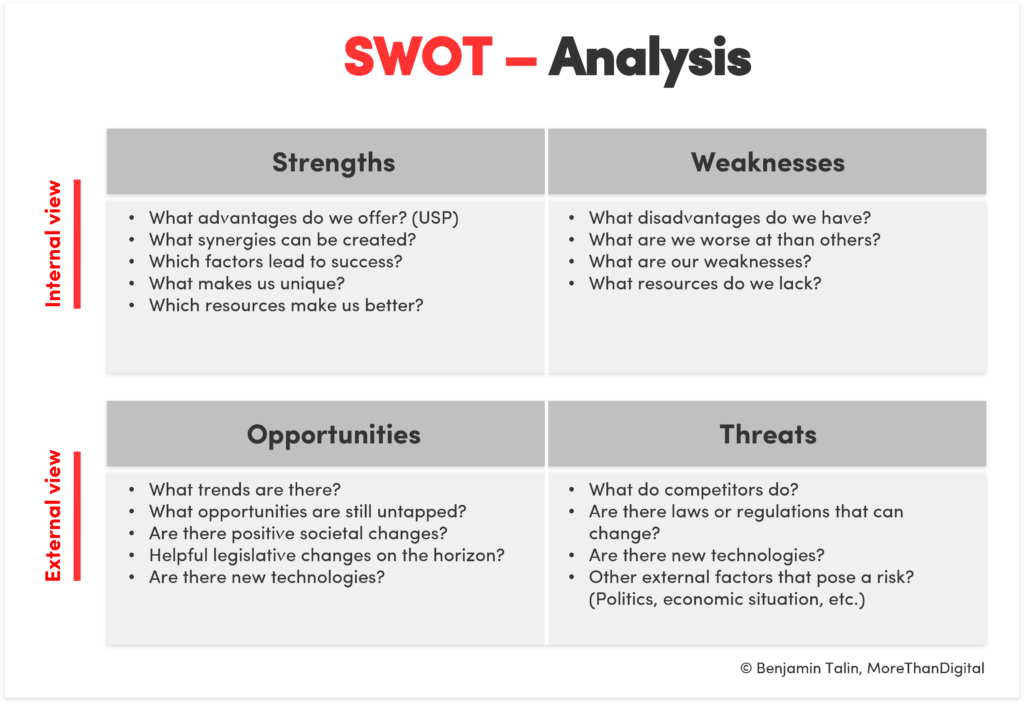
SWOT Analysis Definition And Steps For A Professional SWOT 40 OFF
https://morethandigital.info/wp-content/uploads/2021/11/Understanding-SWOT-analysis-strengths-weaknesses-opportunities-and-threats-explained-1024x704.png.webp
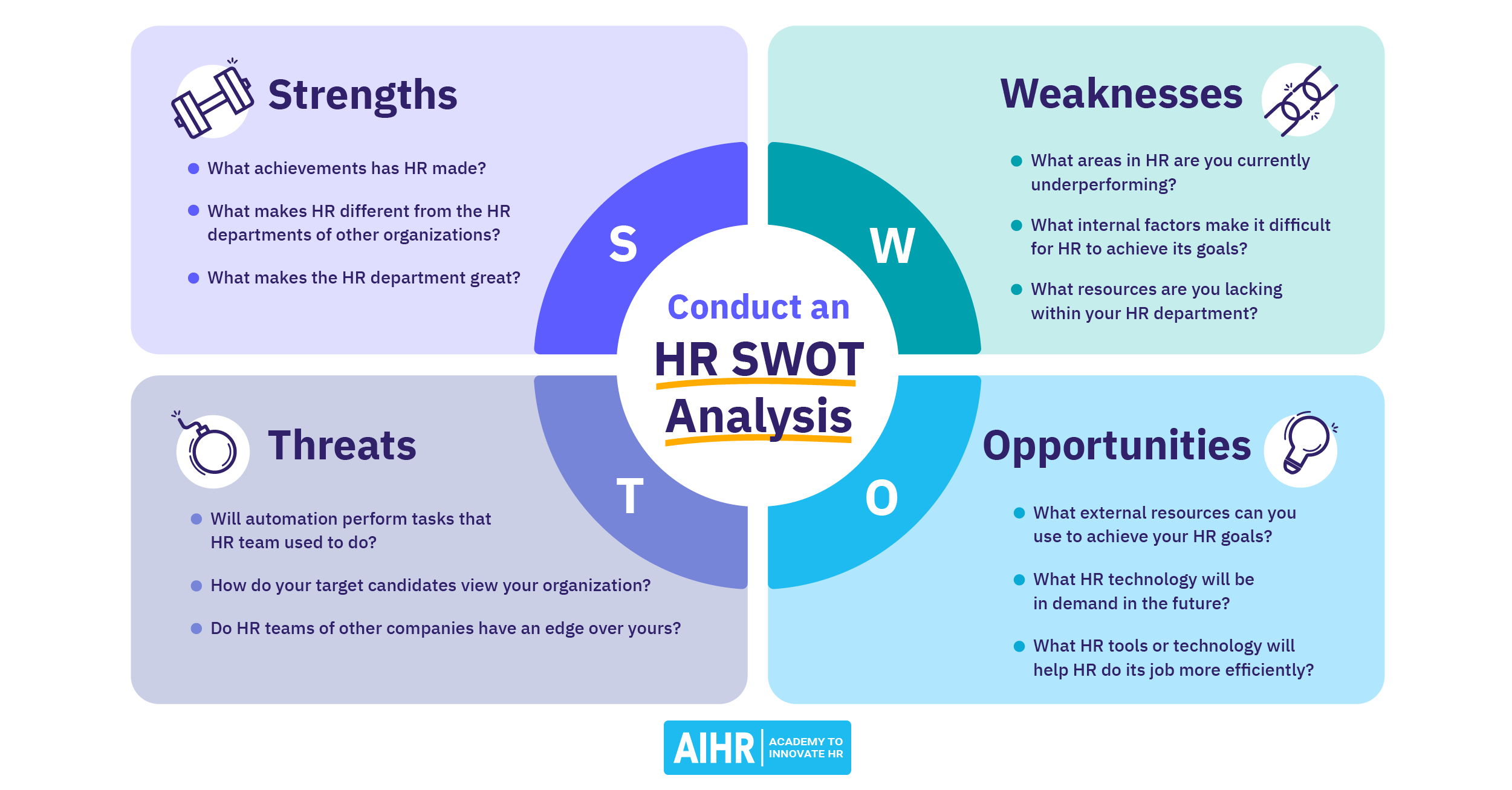
Swot Analysis Example
https://ahaslides.com/wp-content/uploads/2023/03/conduct-an-hr-swot-analysis-social.webp
ZDNET news and advice keep professionals prepared to embrace innovation and ready to build a better future Jul 30 2025 nbsp 0183 32 Just how much are data breaches costing these days Explore the 2025 Cost of a Data Breach Report to learn the average costs AI s impact on the security landscape and more
Vulnerabilities in libxml2 could cause a denial of service or other possible undefined behavior CVE 2025 49796 CVE 2025 49794 CVE 2025 49795 CVE 2025 6021 AIX uses libxml2 as part of its XML parsing functions If the installation fails you may want to temporarily disable your antivirus or security software and try again as antivirus or personal firewall that is set to a very high level of protection could cause installation to fail
More picture related to Security Swot Analysis Example
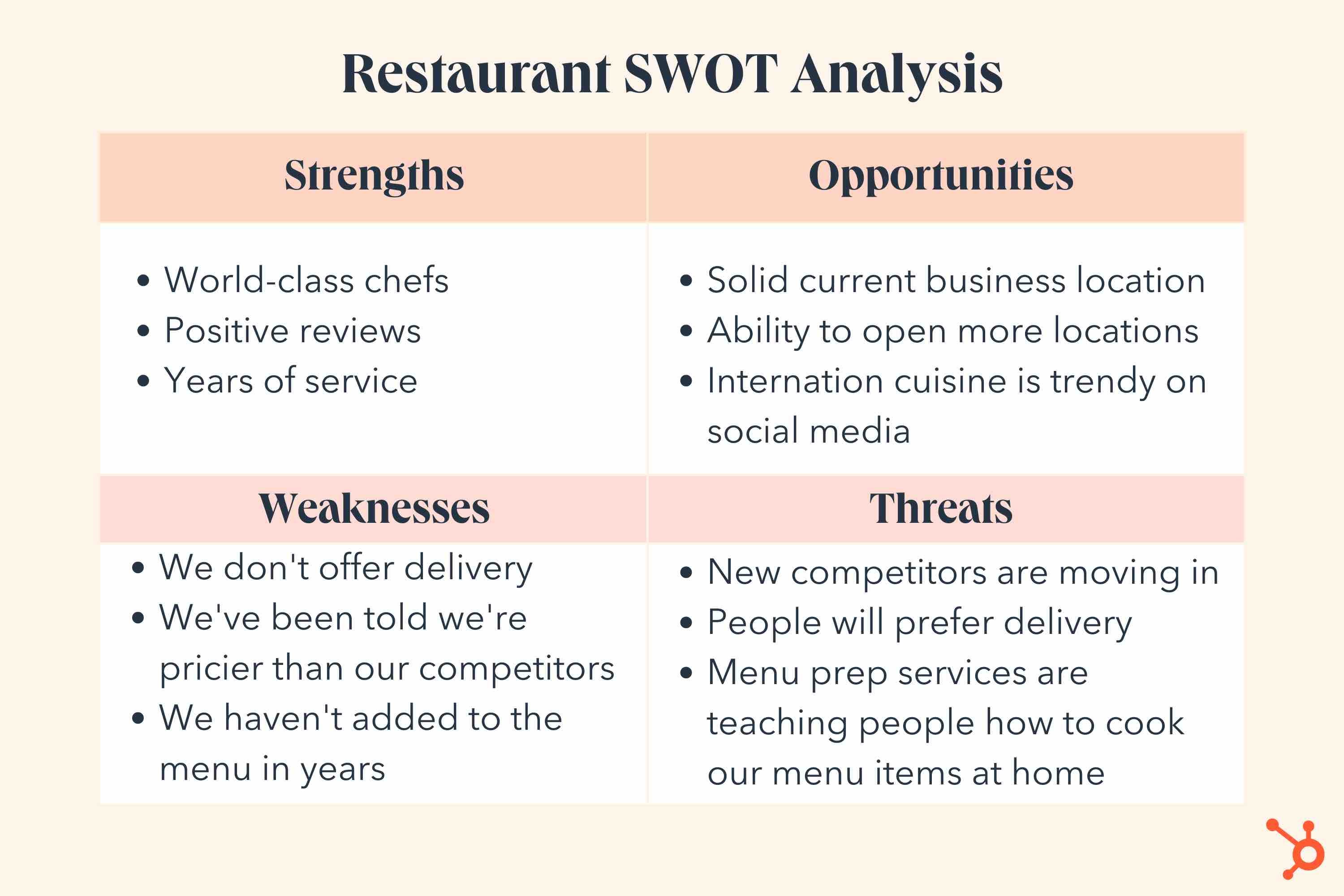
Swot Analysis Example
https://blog.hubspot.com/hs-fs/hubfs/swot-analysis-restaurant.jpg?width=3000&height=2000&name=swot-analysis-restaurant.jpg

SWOT Analysis Security Guard Service Company Profile 56 OFF
https://www.slideteam.net/media/catalog/product/cache/1280x720/e/v/evaluating_it_system_security_using_swot_analysis_building_a_security_awareness_program_slide01.jpg
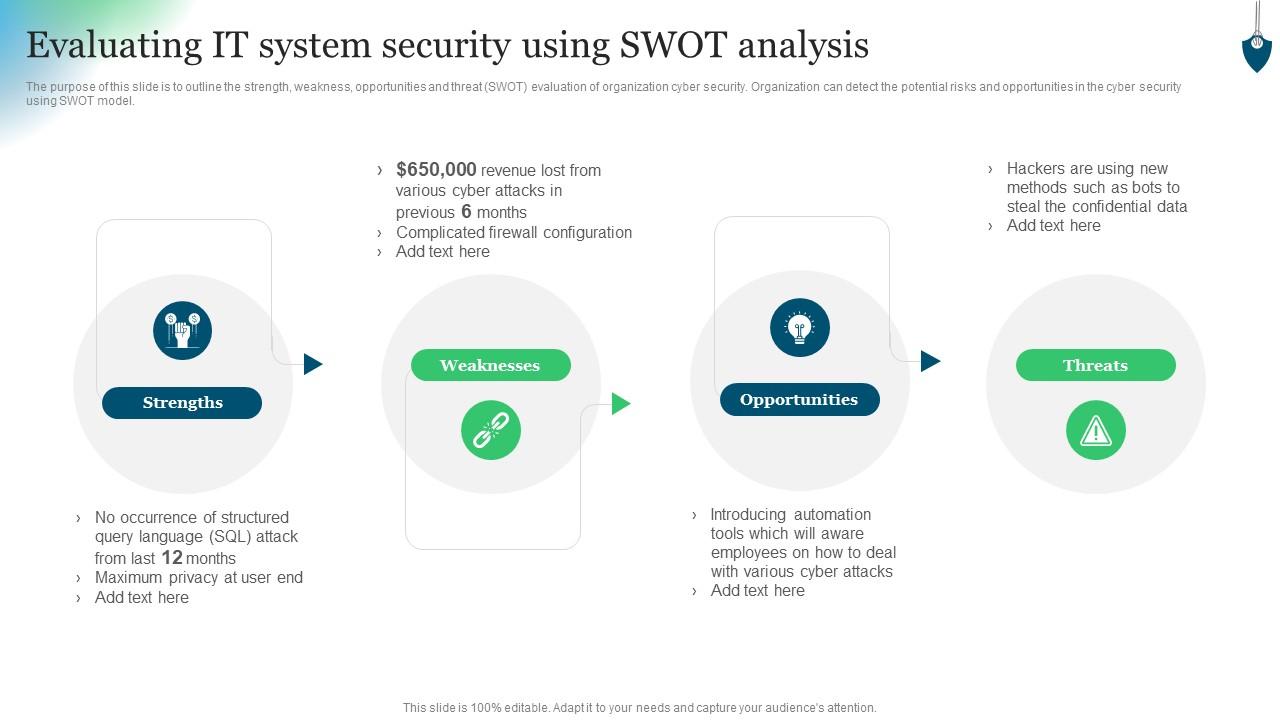
SWOT Analysis Security Guard Service Company Profile 56 OFF
https://www.slideteam.net/media/catalog/product/cache/1280x720/e/v/evaluating_it_system_security_using_swot_analysis_conducting_security_awareness_slide01.jpg
Jan 27 2025 nbsp 0183 32 What is tokenization In data security tokenization is the process of converting sensitive data into a nonsensitive digital replacement called a token that maps back to the original Tokenization can help protect sensitive information For example sensitive data can be mapped to a token and placed in a digital vault for secure storage May 15 2025 nbsp 0183 32 AI security means different things in different contexts While the focus of this page is the use of AI to improve cybersecurity two other common definitions center on securing AI models and programs from malicious use or unauthorized access In one definition cybersecurity experts focus on how threat actors are using AI to improve their cyberattacks or exploit new
[desc-10] [desc-11]

Blank SWOT Analysis Template Google Slides PowerPoint Highfile
https://images.highfile.com/wp-content/uploads/2025/01/Cybersecurity-SWOT-Analysis-Template-Google-Slides-PowerPoint-768x576.jpg?strip=all&lossy=1&quality=90&webp=90&sharp=1&ssl=1

Swot Analysis Template In PPT FREE Download Template
https://images.template.net/303366/cyber-security-swot-analysis-template-bkrn4.jpg
Security Swot Analysis Example - [desc-14]