Secure Hash Algorithm In Cryptography With Example Can t connect Chromebook device to the network If you have trouble to connect with the network Make sure your Chromebook is connected to the Internet Learn how to connect your
BIOS How to install Chrome Important Before you download you can check if Chrome supports your operating system and other system requirements
Secure Hash Algorithm In Cryptography With Example

Secure Hash Algorithm In Cryptography With Example
https://i.ytimg.com/vi/GUam-SAmtxg/maxresdefault.jpg
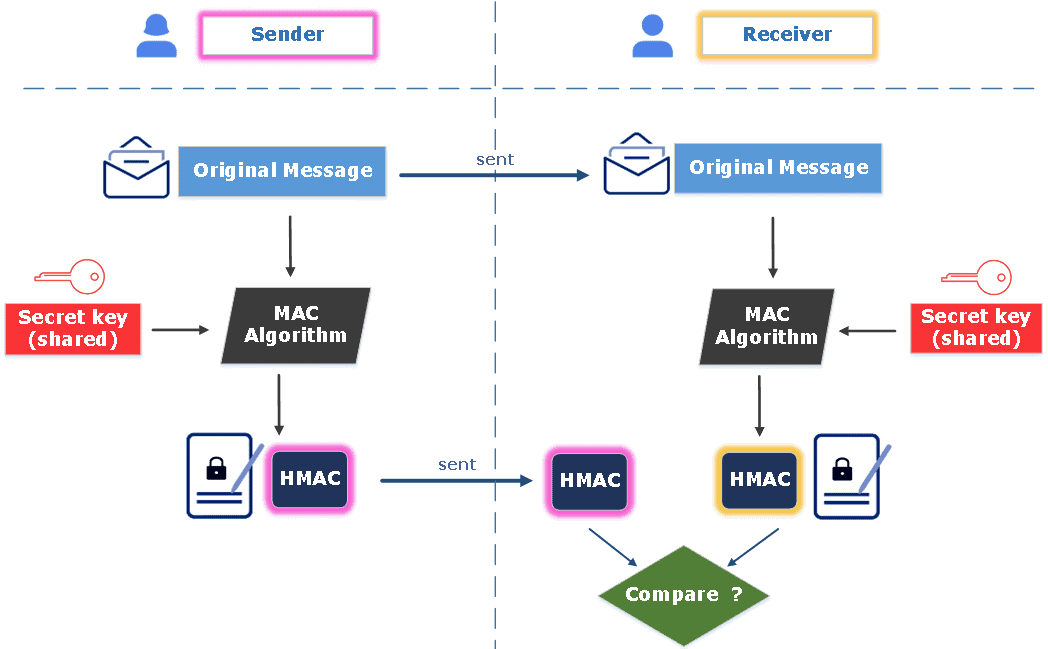
Hmac Big Discount Brunofuga adv br
https://www.baeldung.com/wp-content/uploads/sites/4/2022/08/MAC-1.png
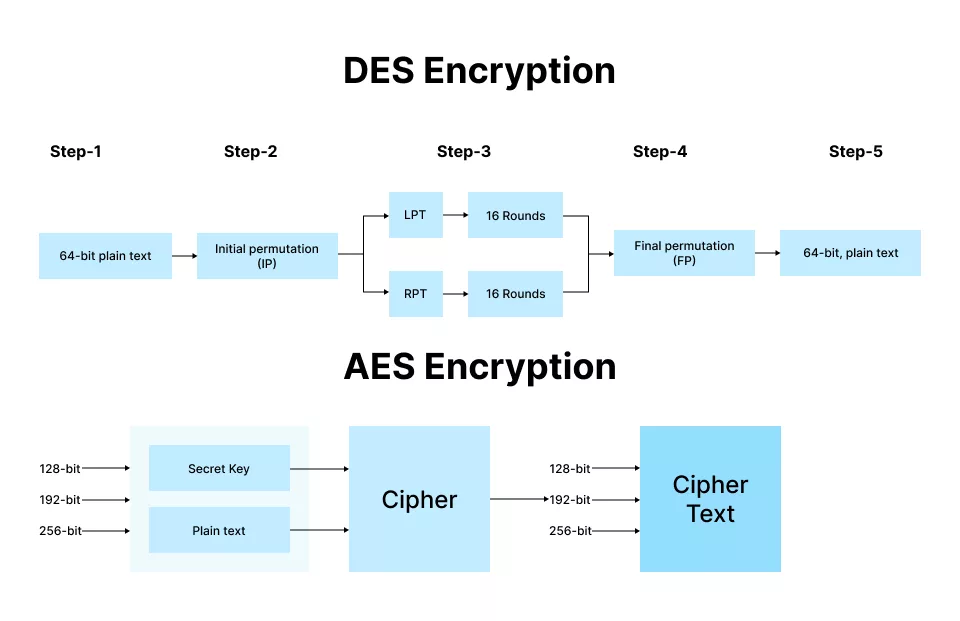
RSA AES Encryption Key Differences Explained 54 OFF
https://cheapsslweb.com/blog/wp-content/uploads/2023/03/RSA-vs.-AES-Encryption_-Key-Differences-Explained-1-jpg.webp
Gmail Aug 15 2016 nbsp 0183 32 Secure Boot F10
Mar 6 2019 nbsp 0183 32 BIOS Secure Boot Secure Boot Secure Boot You can send messages and attachments with Gmail s confidential mode to help protect sensitive information from unauthorized access You can use confidential mode to set an expiration date
More picture related to Secure Hash Algorithm In Cryptography With Example

Filearmorencrypted2
https://www.thesslstore.com/blog/wp-content/uploads/2020/12/how-asymmetric-encryption-works.png
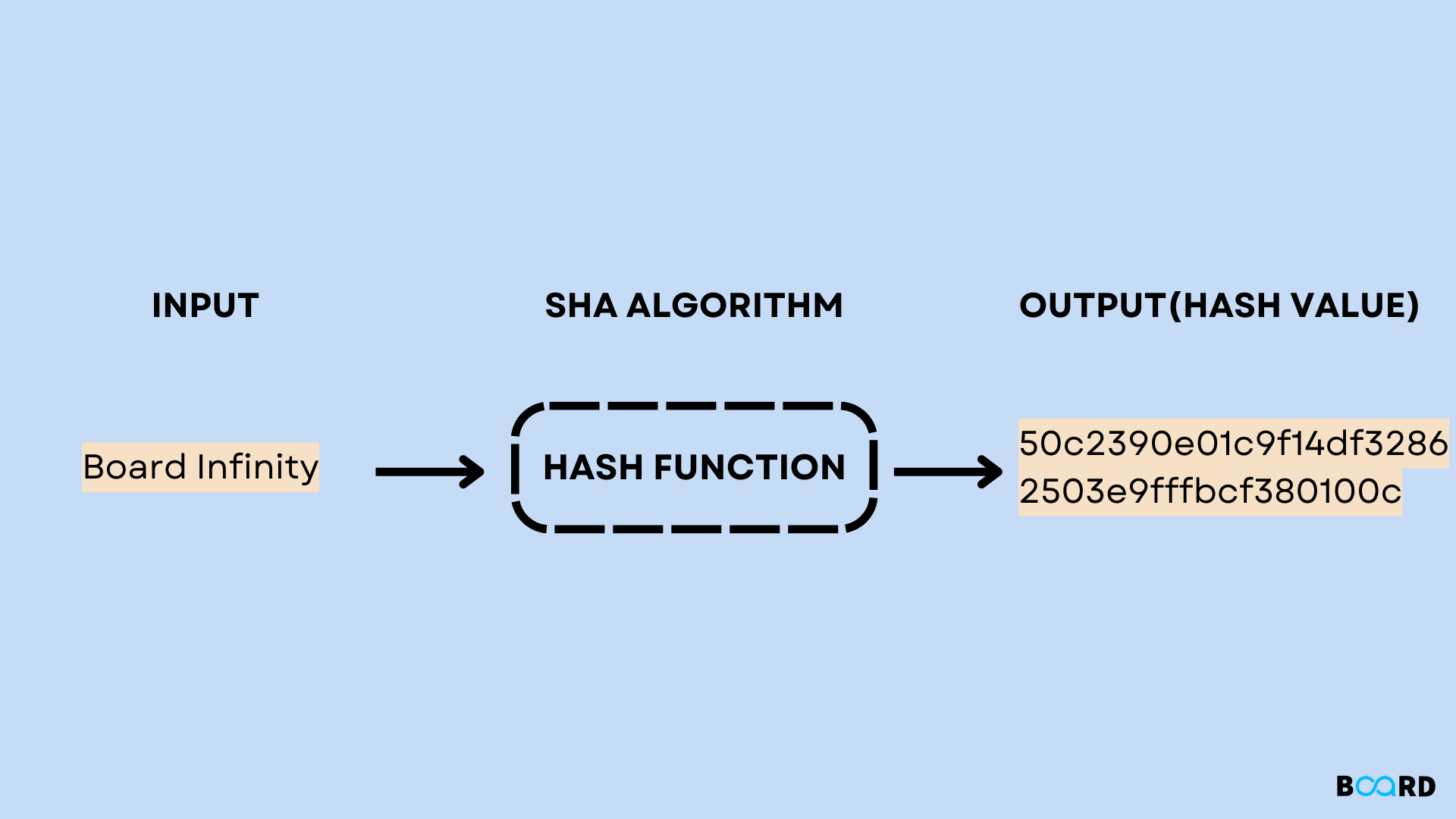
SHA 1 Hash Algorithm Board Infinity
https://www.boardinfinity.com/blog/content/images/2023/01/SHA-aLGORITHM.png

Beginners Guide To Cryptography Quick
https://editor.analyticsvidhya.com/uploads/96092Untitledcc1.jpg
There are a few reasons why your Chrome might be changing to Yahoo One possibility is that you have an extension installed that is changing your default search engine Another possibility Check site information On your computer open Chrome Open a web page To check a site s security to the left of the web address check the security status symbol Default Secure Info
[desc-10] [desc-11]

Encryption And Decryption Jean s Blog
https://www.okta.com/sites/default/files/media/image/2021-05/HashingAlgorithm.png
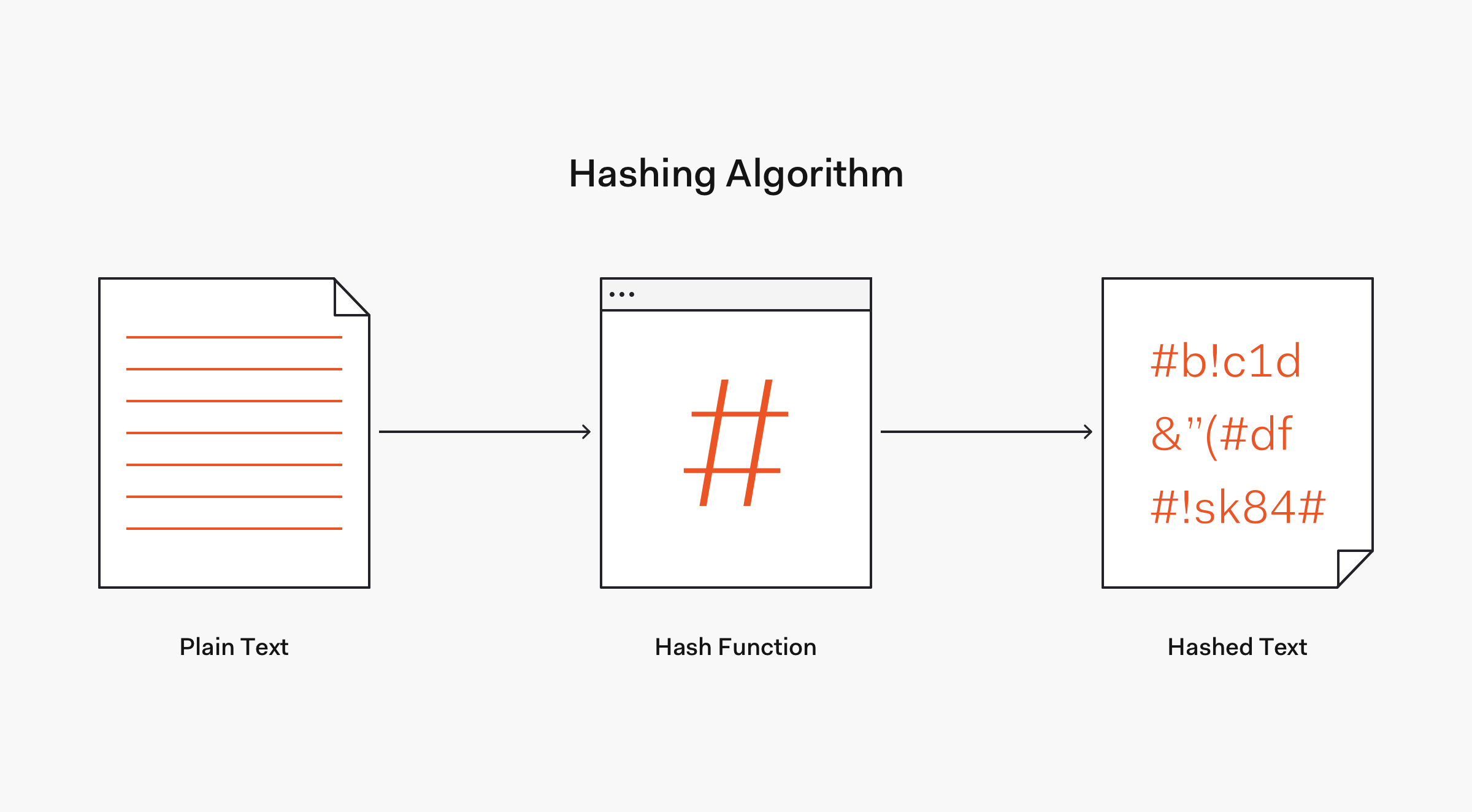
Encryption Hashing
https://cdn.auth0.com/blog/hashing-one-way-road-to-security/hash-flow.png
Secure Hash Algorithm In Cryptography With Example - [desc-14]