Phishing Resistant Mfa Examples Come funziona il phishing Il phishing viene generalmente attuato tramite email annunci o siti simili a siti che utilizzi gi 224 Ad esempio potresti ricevere un email che sembra provenire dalla
Il phishing 232 un tentativo di rubare informazioni personali o violare account online usando indirizzi email messaggi annunci o siti ingannevoli che hanno l aspetto di altri siti che utilizzi Oct 16 2017 nbsp 0183 32 Phishing d 233 tecter un message malveillant 16 octobre 2017 Via votre messagerie ou votre bo 238 te mail certaines personnes malintentionn 233 es tentent de mettre la main sur vos
Phishing Resistant Mfa Examples

Phishing Resistant Mfa Examples
https://pbs.twimg.com/media/FqUVKx3aUAI5YyC.jpg
More Than A Password CISA
https://www.cisa.gov/sites/default/files/styles/large/public/2023-04/23-0008_GRAPHIC_MFA_Redesign.png?itok=lAVyWk8e

The Truth About Phishing Resistant MFA
https://cdn.govexec.com/media/featured/okta_the_truth_about_phishing_resistant_mfa_slate_back.png
Le phishing c est quoi L hame 231 onnage ou phishing est une forme d escroquerie sur internet Le fraudeur se fait passer pour un organisme que vous connaissez banque service des imp 244 ts A phishing attack happens when someone tries to trick you into sharing personal information online How phishing works Phishing is typically done through email ads or by sites that look
O que 233 phishing O phishing 233 uma tentativa de roubar informa 231 245 es pessoais ou acessar contas on line usando e mails mensagens e an 250 ncios enganosos ou sites parecidos com os que Note If you use these advanced phishing and malware settings and dynamic email for your organization learn how compliance rules are applied to dynamic messages Advanced security
More picture related to Phishing Resistant Mfa Examples

The Truth About Phishing Resistant MFA
https://cdn.govexec.com/media/featured/okta_the_truth_about_phishing_resistant_mfa_slate_front.png

Protecting The Healthcare Ecosystem With Phishing resistant MFA Yubico
https://www.yubico.com/wp-content/uploads/2022/09/[email protected]
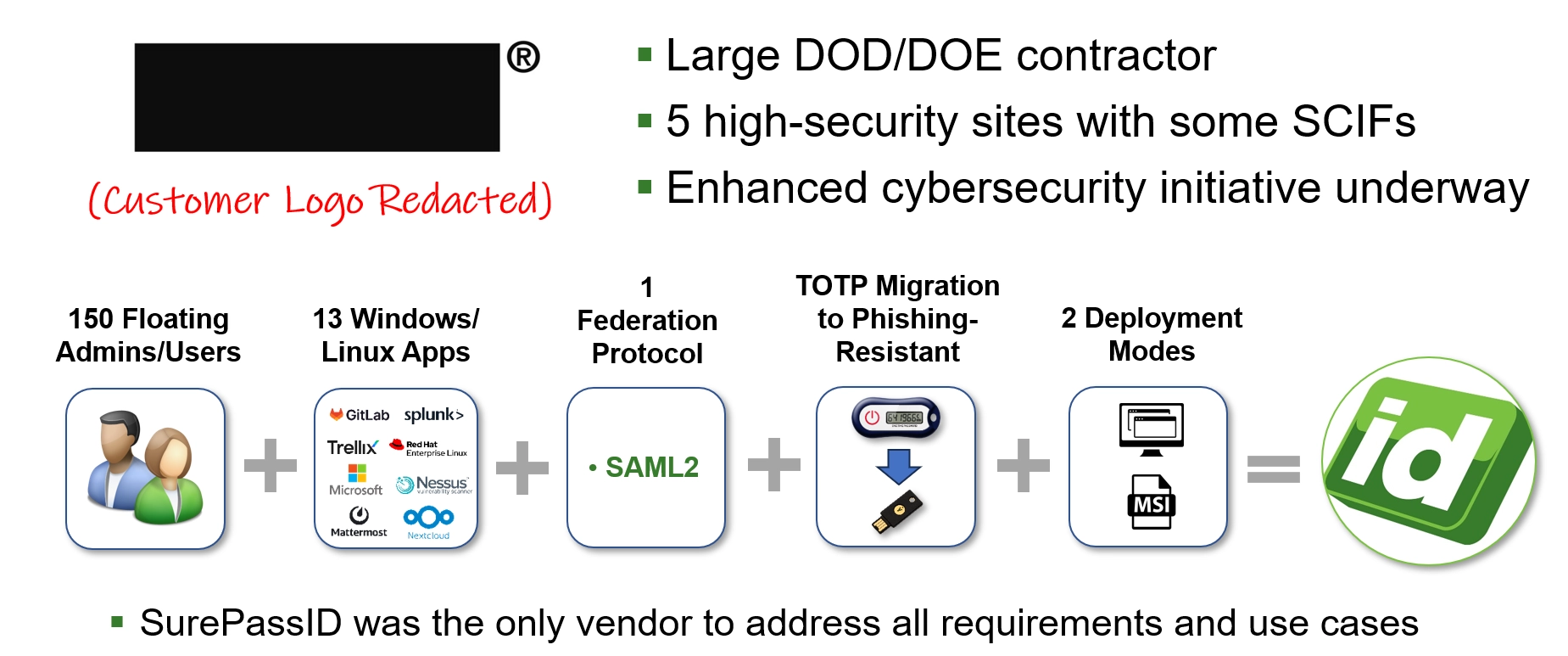
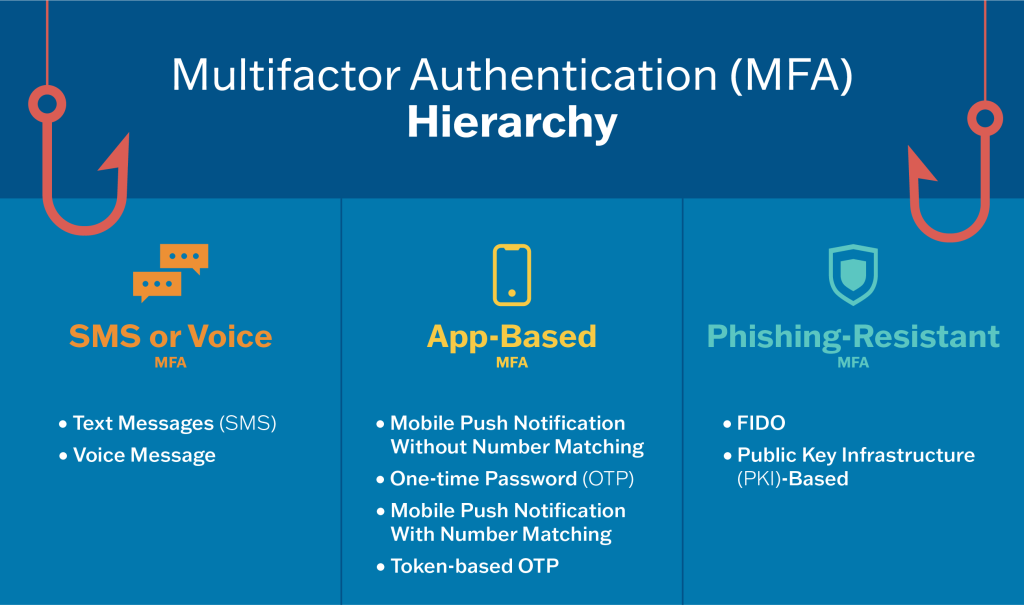
Phishing Resistant MFA Solutions SurePassID
https://surepassid.com/hubfs/SurePassID-Phishing-Resistant-MFA-Case-Study-Image-1.webp
Como o phishing funciona Normalmente o phishing usa e mails an 250 ncios ou sites que se parecem com os que voc 234 j 225 usa Por exemplo pode ser que voc 234 receba um e mail que La suplantaci 243 n de identidad phishing es un intento de robo de informaci 243 n personal o acceso a cuentas en l 237 nea mediante correos electr 243 nicos mensajes anuncios o sitios enga 241 osos que
[desc-10] [desc-11]
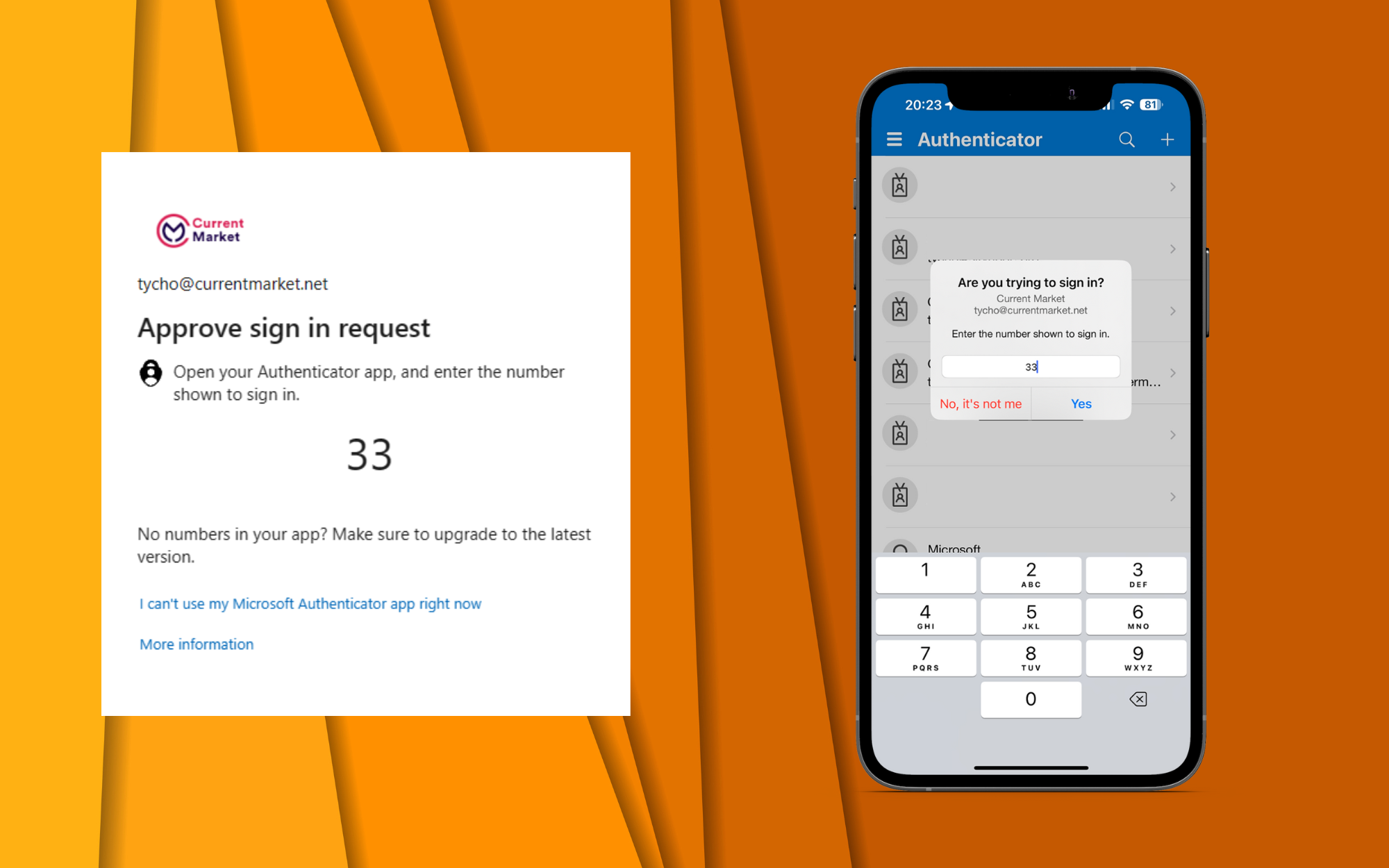
Microsoft Expands MFA With Number Matching
https://currentcloud.net/content/images/2023/02/Untitled-design.png
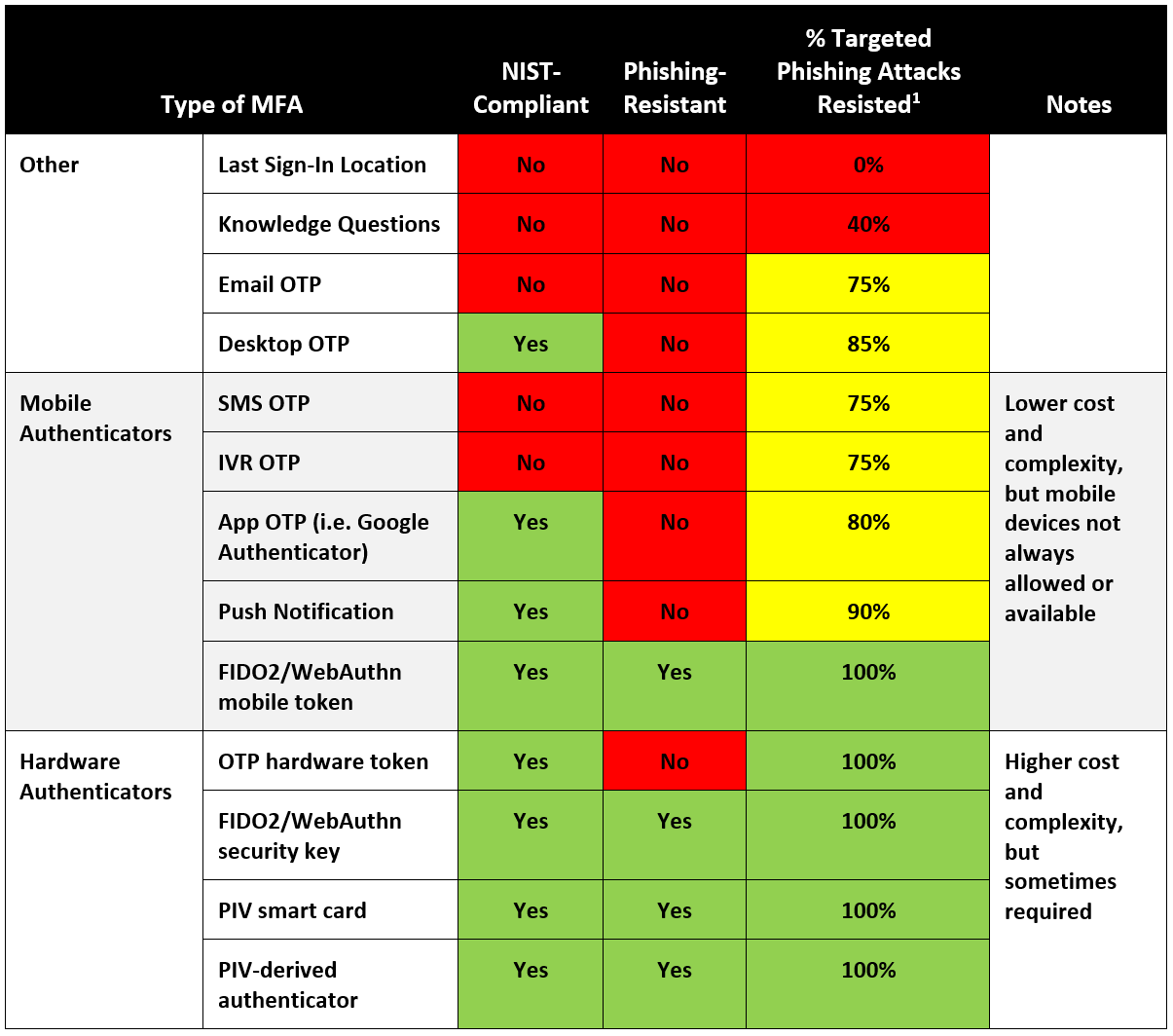
Phishing Resistant MFA SurePassID
https://surepassid.com/hubfs/SurePassID-Types-of-MFA-compared-NIST-compliant-phishing-resistant.webp
Phishing Resistant Mfa Examples - A phishing attack happens when someone tries to trick you into sharing personal information online How phishing works Phishing is typically done through email ads or by sites that look