Explain Public Key Cryptography In Cyber Security Explanation explication explain explanation explication
Sci SCI Aug 16 2010 nbsp 0183 32 To explain about your family would be to explain some details about your family To explain your family would be to provide reasons for how your family works or how it came to
Explain Public Key Cryptography In Cyber Security

Explain Public Key Cryptography In Cyber Security
https://www.edureka.co/blog/wp-content/uploads/2018/07/encryption-algorithms-what-is-cryptography-edureka.png
Cryptography SpencerMakenzie
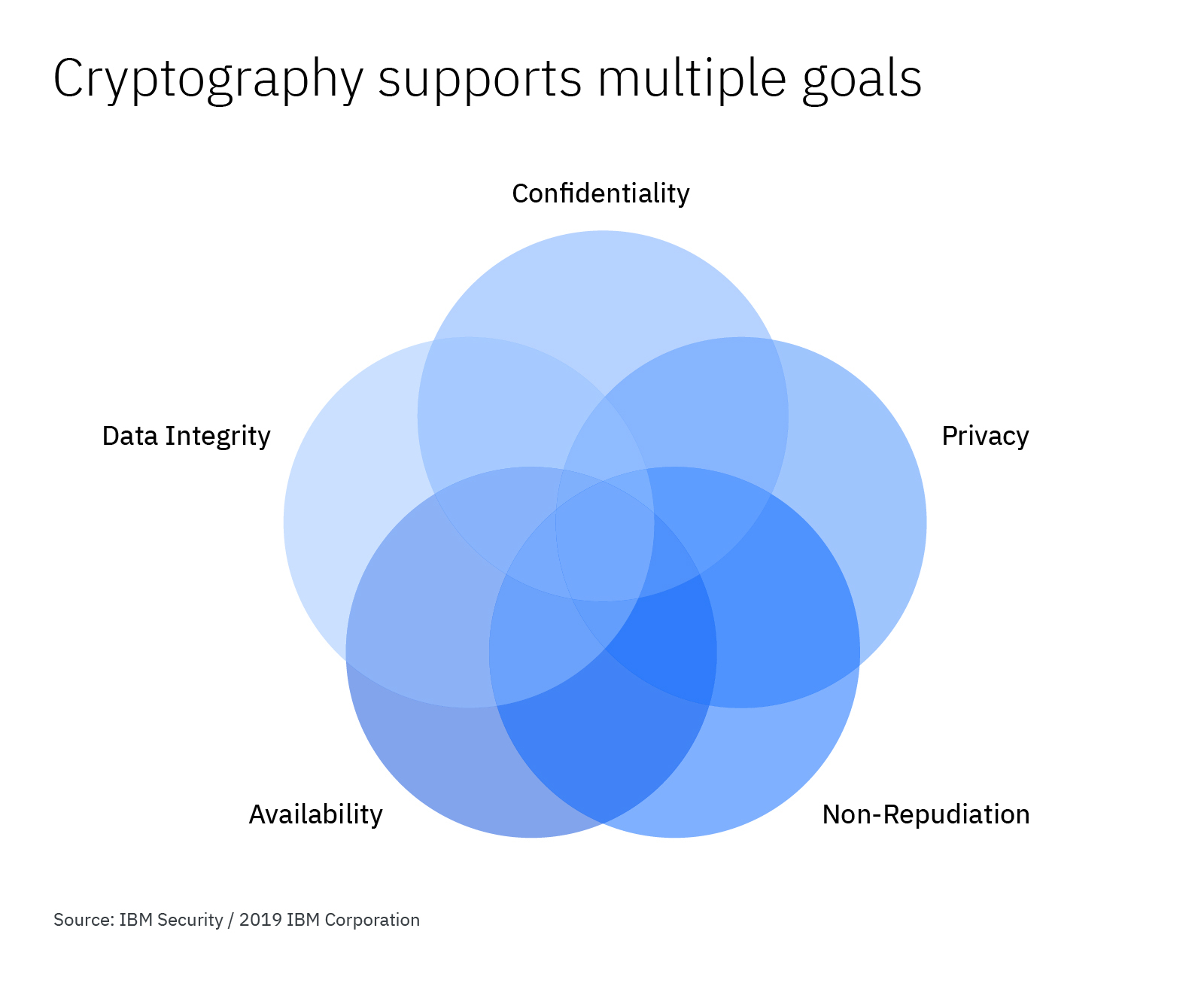
https://securityintelligence.com/wp-content/uploads/2019/10/si-cryptographygoals-diagram.jpg
https://media.imna.ir/d/2023/02/02/4/1843438.jpg?ts=1675330066000
EXPLAIN SQL SQL Explain explanation explaination 22
Jul 8 2010 nbsp 0183 32 Explain to him how Brazil could have lost to Holland means the explanation should be in his direction In b explain me there is no preposition quot to quot indicating the direction of the T t T t T 2
More picture related to Explain Public Key Cryptography In Cyber Security

Cryptography FahrulRoup
https://editor.analyticsvidhya.com/uploads/11325Untitledcc2.jpg

Cryptography FahrulRoup
https://scaler.com/topics/images/cryptography.webp
Trends In Cybersecurity 2024 Nucleio Information Services
https://wp.technologyreview.com/wp-content/uploads/2019/07/quantumexplainer3.2-01-10.jpg
Dec 2 2023 nbsp 0183 32 Although your paper presents related aspects the proposed approach and scope have a different Dec 5 2019 nbsp 0183 32 I found two examples with the verb quot elaborate quot that fall under the first definition quot to explain or describe something in a more detailed way quot Here are they
[desc-10] [desc-11]

What Is A Real Number Key Examples Explained
https://examplesweb.net/wp-content/uploads/what-is-a-real-number-key-examples-explained.jpg

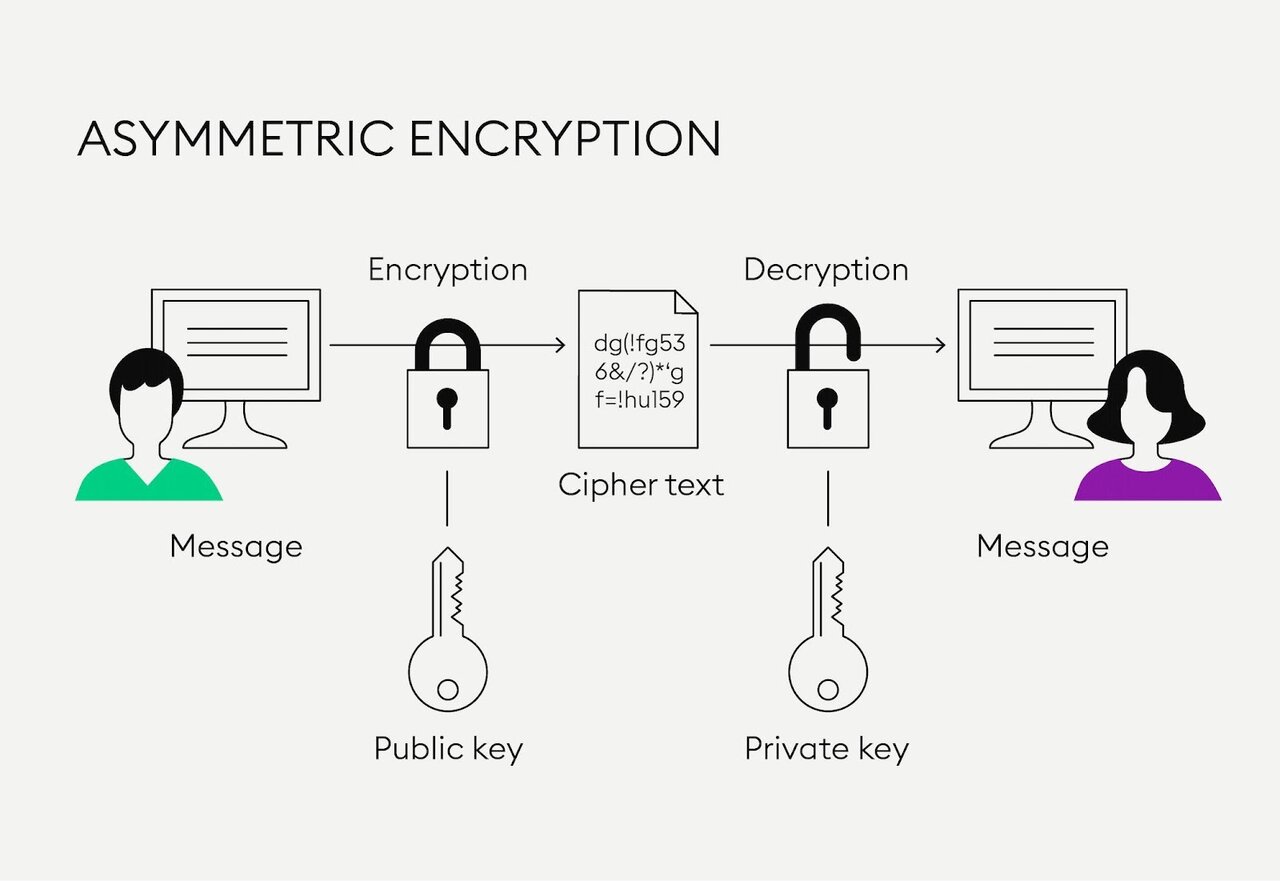
Public Key Cryptography Algorithms
https://www.sectigo.com/uploads/images/Sectigo-Quantum-Lab-Diagram.png
Explain Public Key Cryptography In Cyber Security - [desc-13]