What Is The Second Step Of The Risk Assessment Process 19 William Butler Yeats 183 183 The Second
SECOND returns the intuitive understanding of seconds and is useful primarily in other calculations rather than to extract the second component of a known time as that value is Turn on 2 Step Verification Verify it s you with a second step Important When you sign in with a passkey it bypasses your second authentication step since it verifies that you have
What Is The Second Step Of The Risk Assessment Process
What Is The Second Step Of The Risk Assessment Process
https://lookaside.fbsbx.com/lookaside/crawler/media/?media_id=1458389215555671
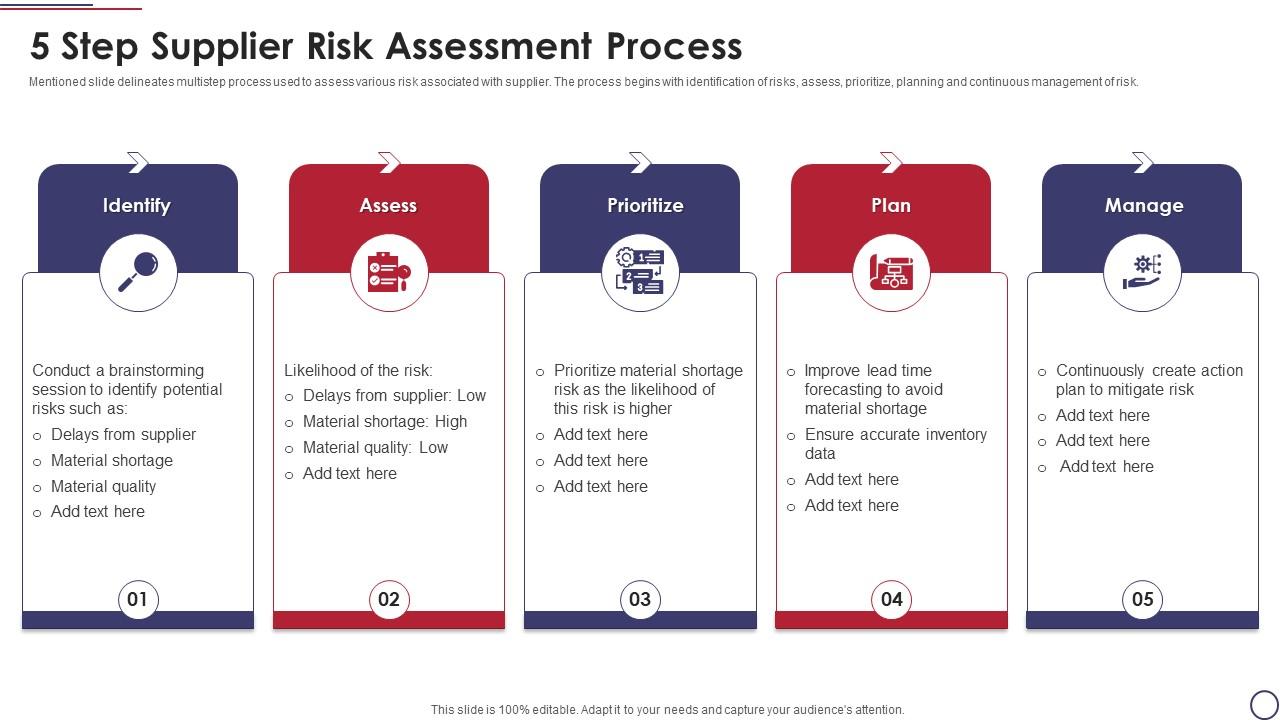
Risk Assessment Steps Bulk Buy Gbu taganskij ru
https://www.slideteam.net/media/catalog/product/cache/1280x720/5/_/5_step_supplier_risk_assessment_process_slide01.jpg
Pitching Masterclass Workshop Expo JoinUsForTEA JoinUsForTEA At
https://lookaside.fbsbx.com/lookaside/crawler/media/?media_id=627631339393768
If you re on the phone and your first SIM is active you can use the second SIM to place or answer a call Meanwhile the first call goes on hold You must turn on automatic data switching for the Dec 19 2018 nbsp 0183 32 10 10min s 10mins hour second 10 minutes 10mins 10 hours 10 hs
To easily manage and share content across all of your devices and the cloud use Google s desktop sync client Drive for desktop If you edit delete or move a file on the Cloud the same Aug 2 2019 nbsp 0183 32 Learn how to create a second email address in your Gmail account with step by step guidance and tips provided
More picture related to What Is The Second Step Of The Risk Assessment Process

Process Identification
https://d2slcw3kip6qmk.cloudfront.net/marketing/blog/2018Q2/risk-assessment-process/hazard-identification-and-analysis.png
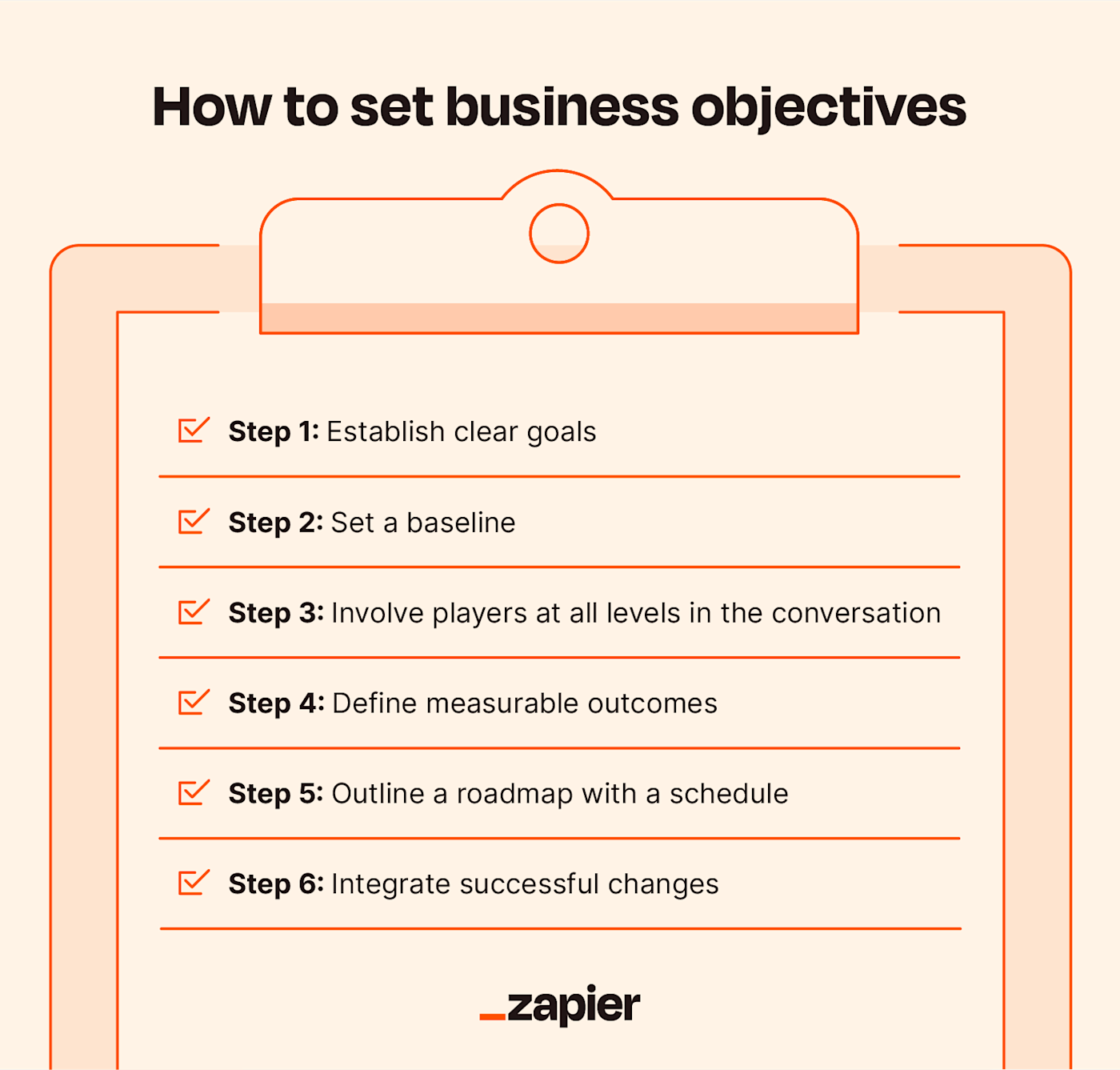
Business
https://images.ctfassets.net/lzny33ho1g45/5FsO5stcCQ1BeZwbSFxaJn/d959af04f94822af07f2b5e35e5d5978/how-to-set-business-objectives.png?w=1400
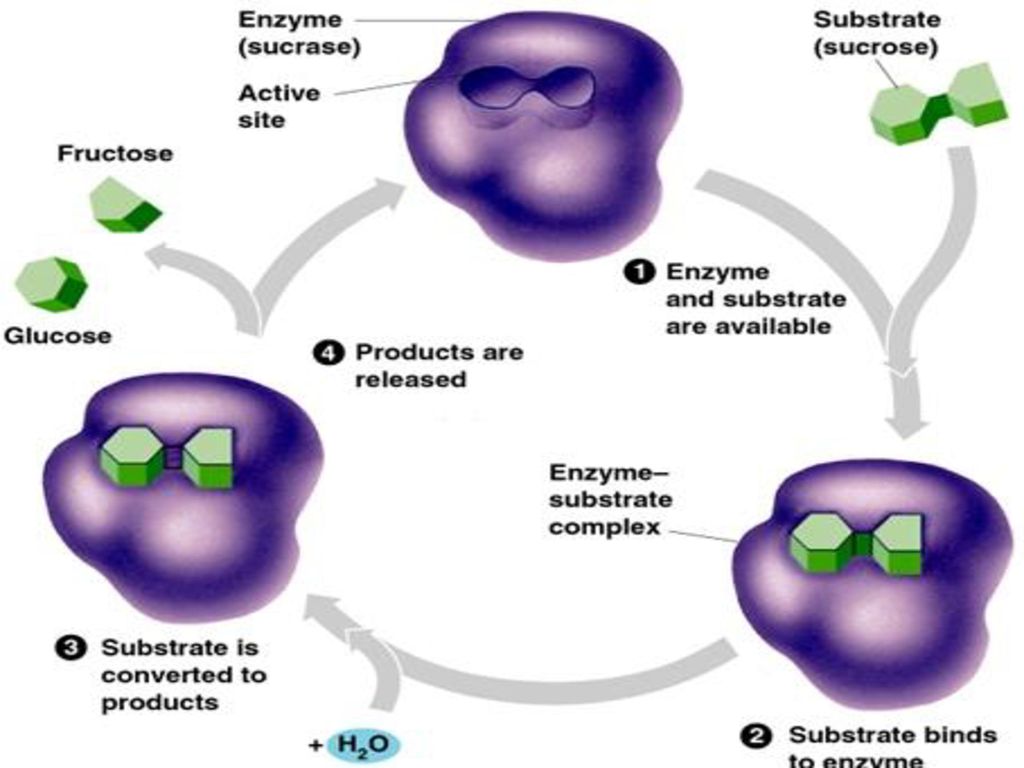
Reaction Mechanisms Catalysis Ppt Download
https://slideplayer.com/slide/12910537/78/images/12/Biological+Catalysts+Living+organisms+rely+on+enzymes%2C+biological+catalysts+that+increase+the+rate+of+biochemical+reactions%2C+to+survive..jpg
Require a security key as your second step If you turn on 2 Step Verification and sign in on an eligible phone you can get Google prompts To make a security key your required second Step 3 Optional Add a second user profile to your child s device The steps below only work if your child s device allows multiple profiles Check the device manufacturer s support page for
[desc-10] [desc-11]
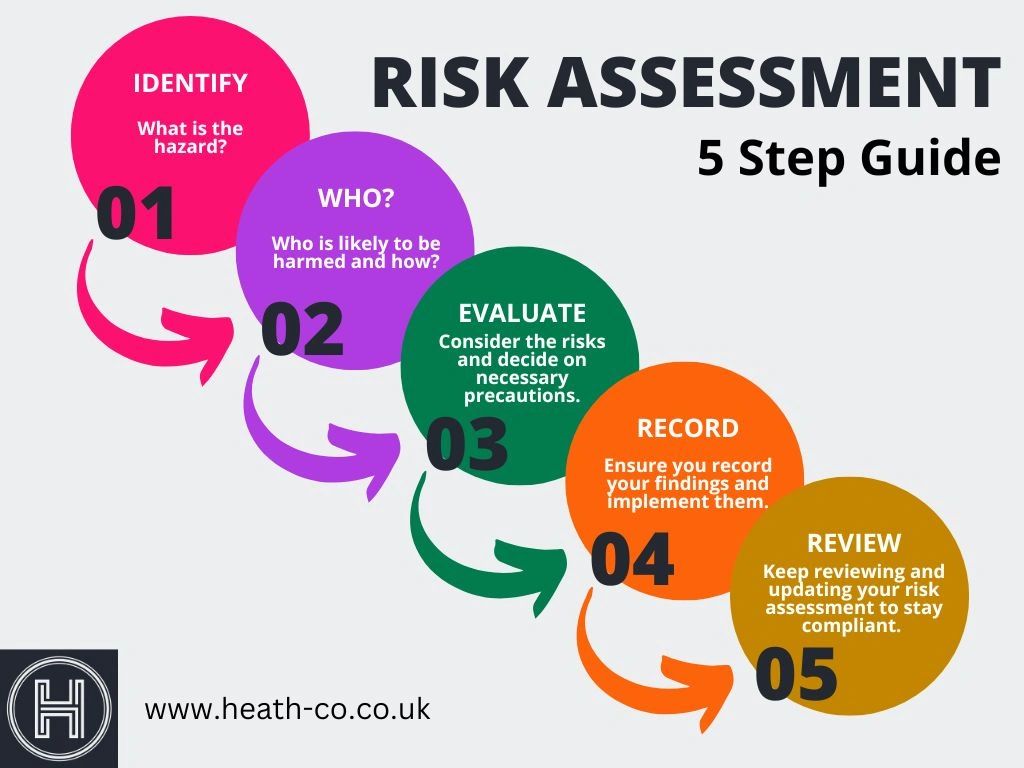
Risk Assessments A 5 Step Guide
https://img1.wsimg.com/isteam/ip/25a4a698-933d-41b7-a565-754efd561939/Colorful Success Circle Steps Diagram.jpg
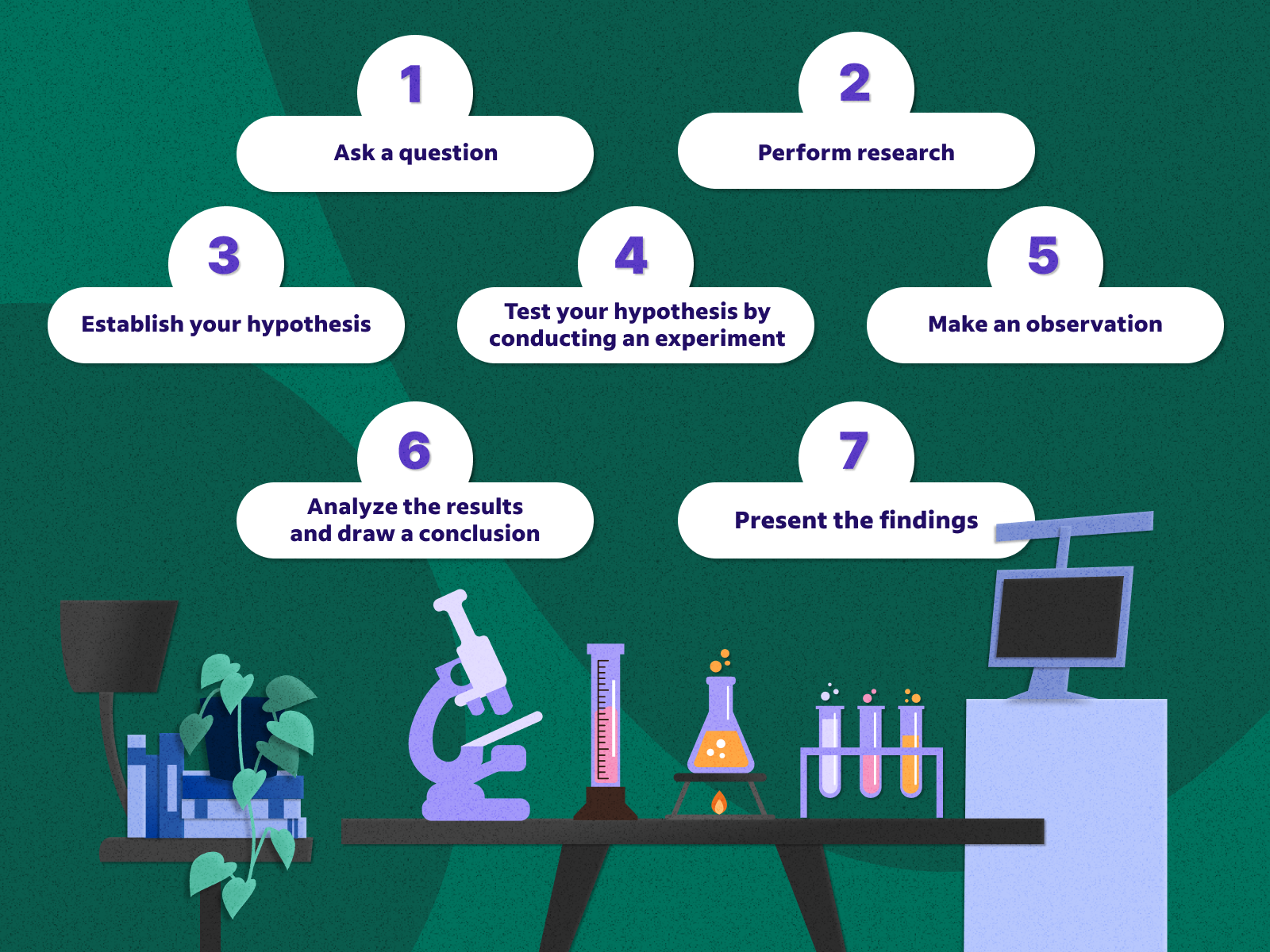
Observation Science
https://images.ctfassets.net/pdf29us7flmy/4yvNlyN6x0OYtiuNdeXQI9/ec9a975a9f860c6e4c6d3aea718618ac/-IND-004-063-_The_Scientific_Method_Steps_Final.png
What Is The Second Step Of The Risk Assessment Process - [desc-12]

