What Is Hash Function And How It Works Hash functions are related to and often confused with checksums check digits fingerprints lossy compression randomization functions error correcting codes and ciphers Although the
The hash is the fingerprint result of the hash function it identifies with a high probability the initial data without having to store it This allows you to verify a password without needing to know it Jul 23 2025 nbsp 0183 32 Hash functions are a fundamental concept in computer science and play a crucial role in various applications such as data storage retrieval and cryptography A hash function
What Is Hash Function And How It Works
What Is Hash Function And How It Works
https://i.ytimg.com/vi/Zeb685c7wrM/maxresdefault.jpg

What Is Hash And How Is It Different From Weed YouTube
https://i.ytimg.com/vi/NLBpcq-NGnc/maxresdefault.jpg
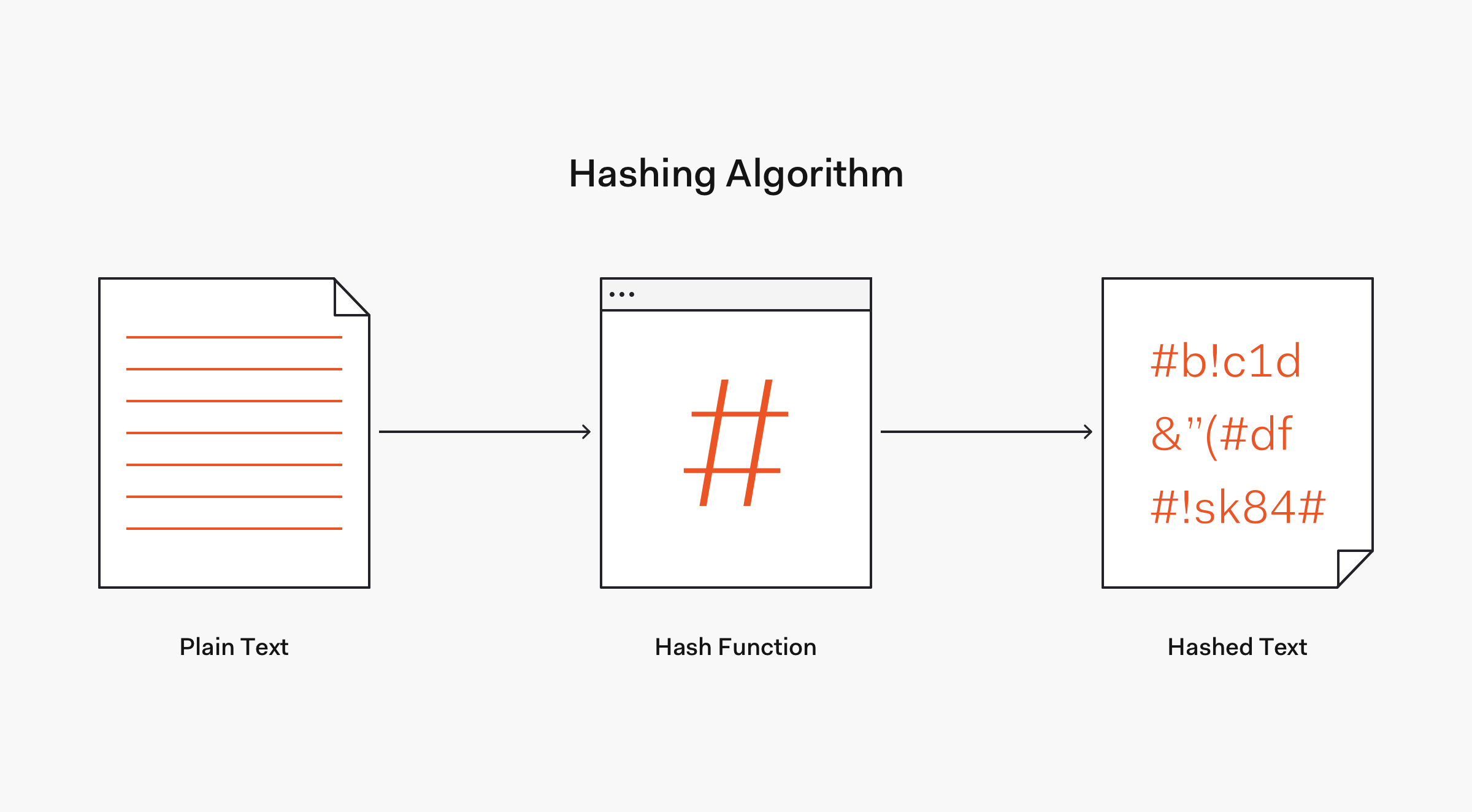
Encryption Hashing
https://cdn.auth0.com/blog/hashing-one-way-road-to-security/hash-flow.png
A tool for creating an MD5 hash from a string Use this fast free tool to create an MD5 hash from a string This SHA256 online tool helps you calculate hashes from strings You can input UTF 8 UTF 16 Hex Base64 or other encodings It also supports HMAC
Decrypt and crack your MD5 SHA1 SHA256 MySQL MD5 Email SHA256 Email and NTLM hashes for free online We also support Bcrypt SHA512 Wordpress and many more May 13 2025 nbsp 0183 32 Learn how a hash function in cryptography secures data ensures integrity and protects digital systems from tampering and unauthorized access
More picture related to What Is Hash Function And How It Works
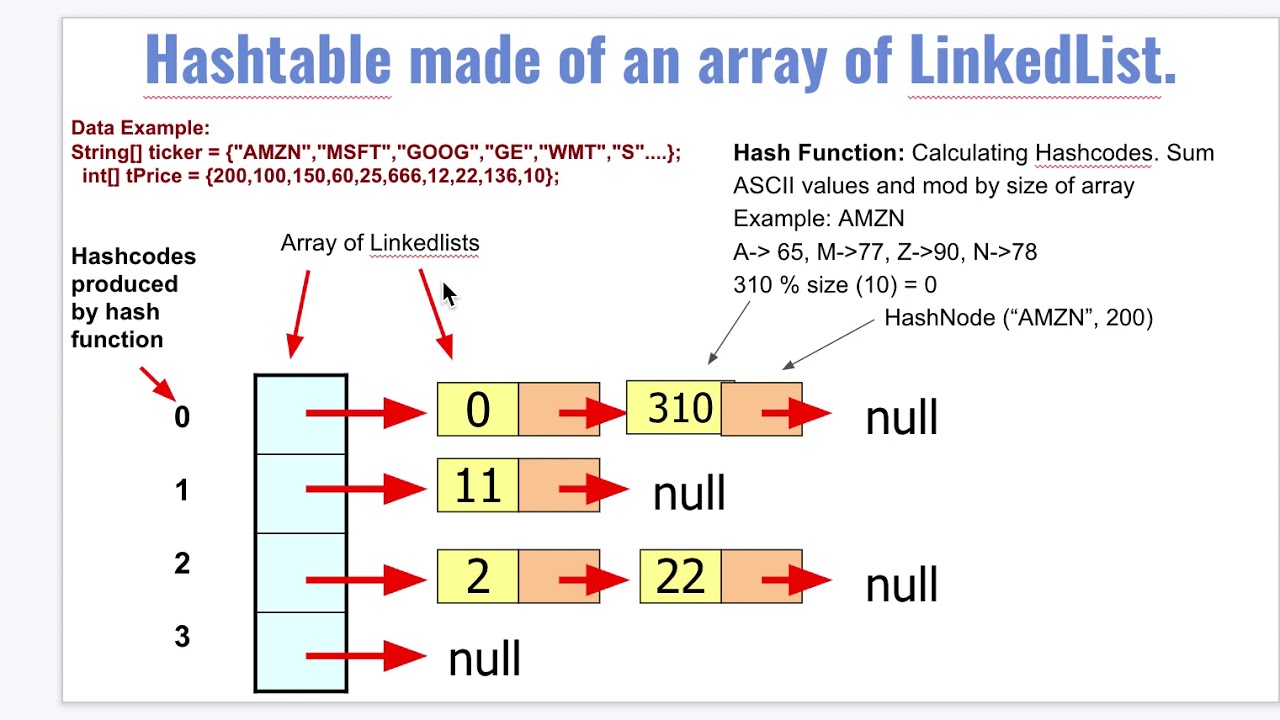
What Are Hash Tables Domino Data Lab
https://cdn.sanity.io/images/kuana2sp/production-main/c015c55fca5c286607aff134760bb35e5d54db32-1011x704.webp

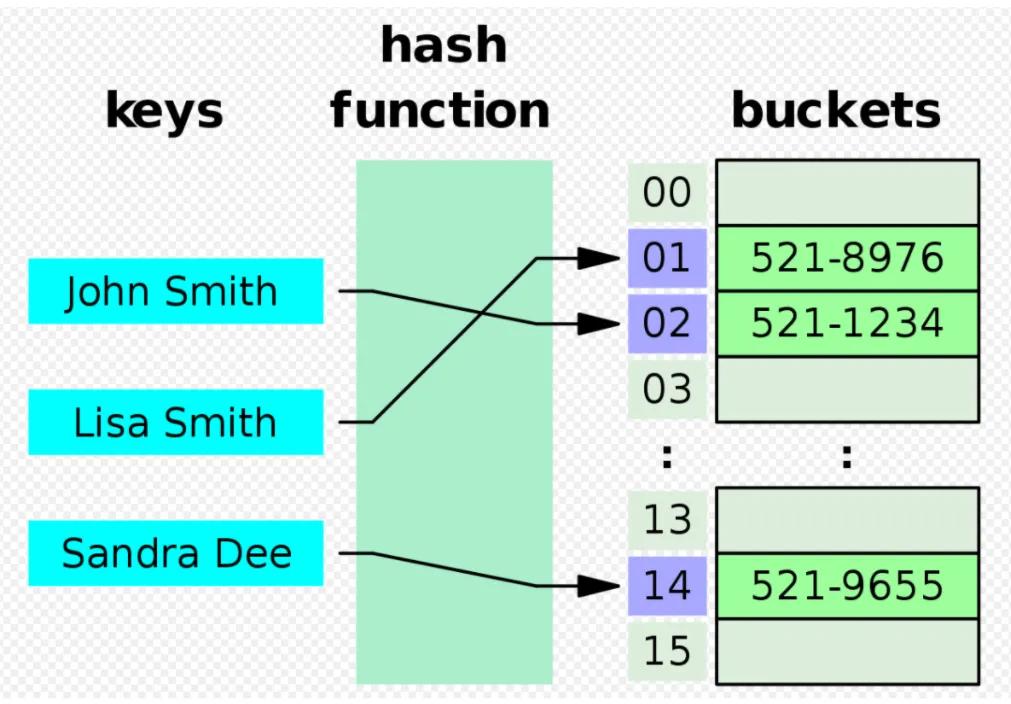
Hashing Algorithm Overview Types Methodologies Usage Okta
https://www.okta.com/sites/default/files/media/image/2021-05/HashingAlgorithm.png
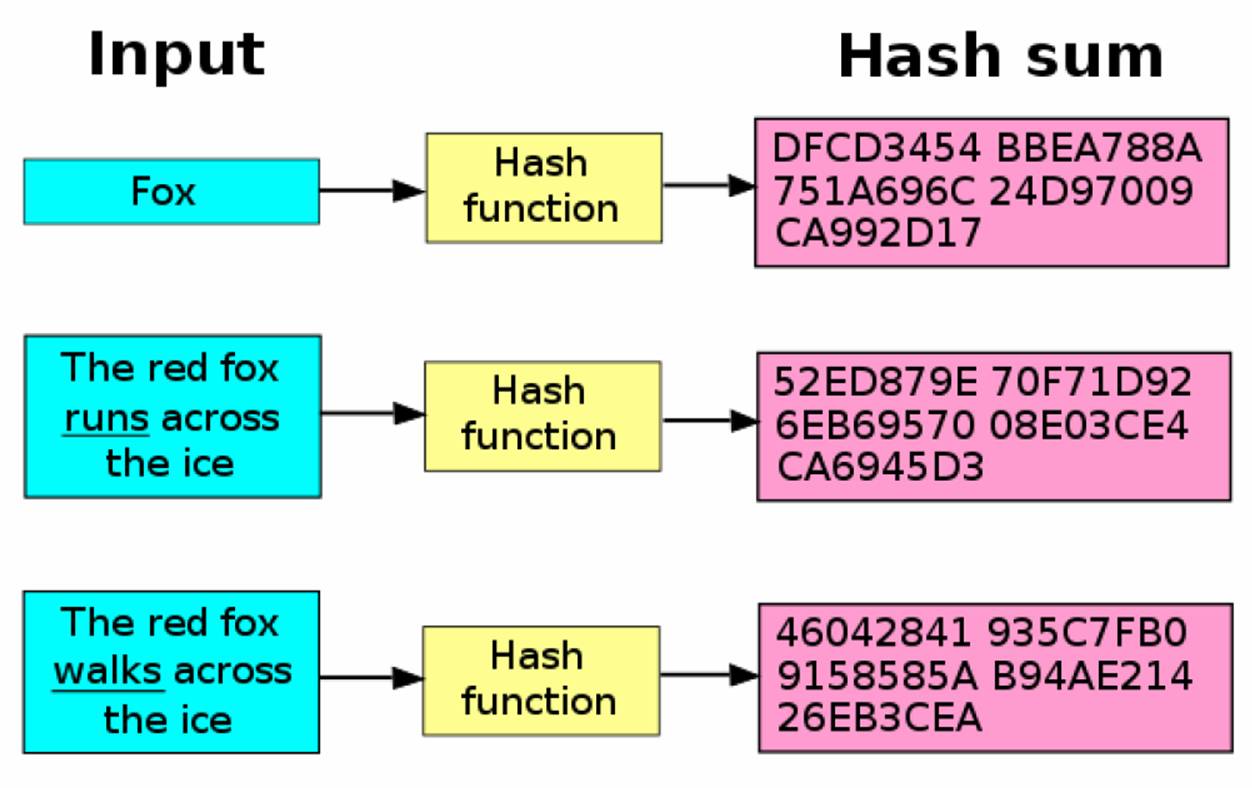
What Is A Hash Hacking Tutorials By Xeus
http://xeushack.com/assets/img/posts/on-hashes/hash-examples.jpg
Hash functions are mathematical operations that quot map quot or change a given collection of data into a fixed length bit string that is referred to as the quot hash value quot Hash functions have a variety of Analyze and identify different types of hashes online with this free tool Detect MD5 SHA 1 SHA 256 bcrypt and more hash types Perfect for developers and security professionals
[desc-10] [desc-11]

Hash Function Cybersecurity Glossary Vrogue co
https://www.thesslstore.com/blog/wp-content/uploads/2021/01/how-hashing-works-breakdown-1024x640.png
:max_bytes(150000):strip_icc()/cryptographic-hash-functions-final-edf41ae1d0164df3aaee536acb527613.png)
Tiem Needed To Get A Password From Hash Sale Online
https://www.investopedia.com/thmb/9HuTn3n843ILWbhEqBskHD2GhWE=/1500x0/filters:no_upscale():max_bytes(150000):strip_icc()/cryptographic-hash-functions-final-edf41ae1d0164df3aaee536acb527613.png
What Is Hash Function And How It Works - A tool for creating an MD5 hash from a string Use this fast free tool to create an MD5 hash from a string