What Is Authentication In System Security Nov 1 2023 nbsp 0183 32 Authentication technology provides access control for systems by checking to see if a user s credentials match the credentials in a database of authorized users or a data authentication server In doing this authentication
Jun 16 2022 nbsp 0183 32 User authentication is the process of verifying the identity of a user when that user logs in to a computer system There are different types of authentication systems which are In cyber security authentication is the process of verifying someone s or something s identity Authentication usually takes place by checking a password a hardware token or some other piece of information that proves identity
What Is Authentication In System Security

What Is Authentication In System Security
https://www.nist.gov/sites/default/files/images/2019/09/25/multifactor-authentificaton.png

Setting Authentication Preferences Vrogue co
https://www.strongdm.com/hubfs/authentication-guide.png
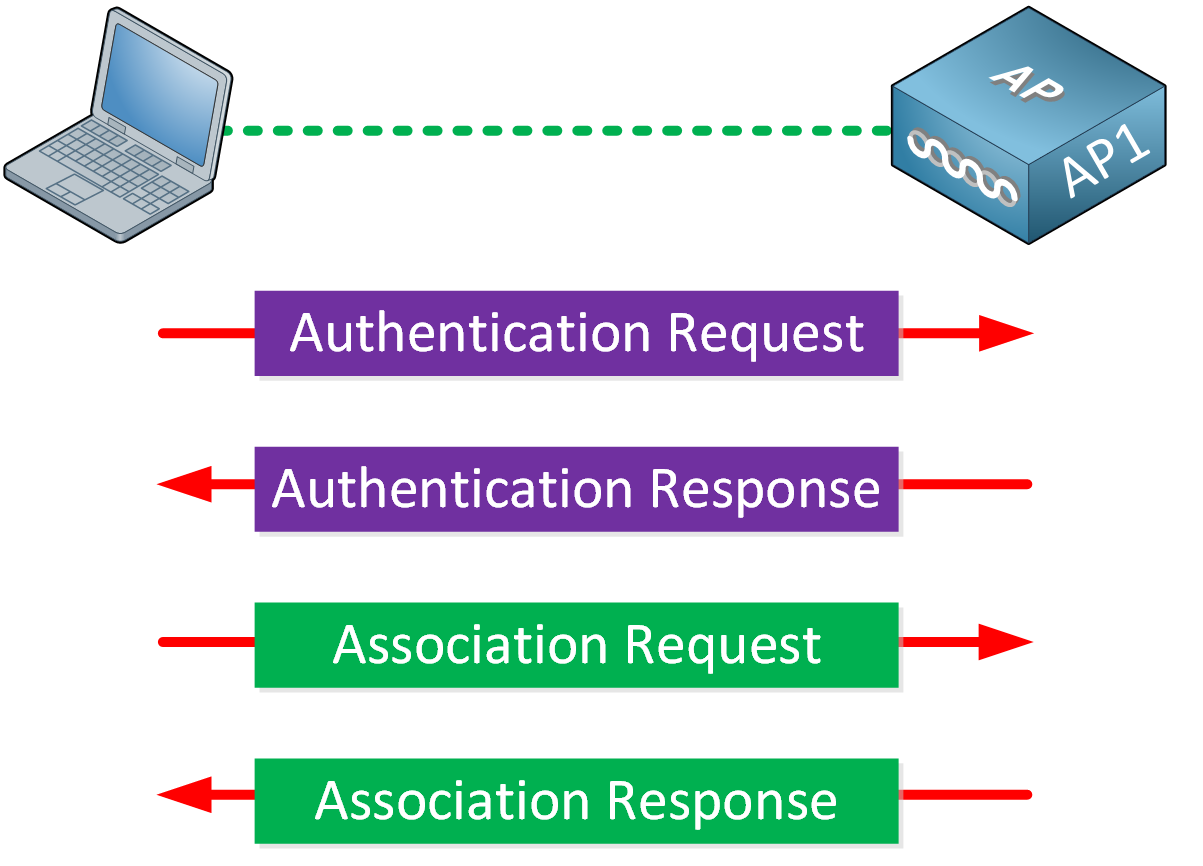
Wi Fi Legacy Security Mechanisms
https://cdn.networklessons.com/wp-content/uploads/2019/12/wireless-open-authentication.png
Jun 18 2024 nbsp 0183 32 Authentication is a fundamental component of information security strategy It is particularly important to identity and access management IAM the cybersecurity discipline that deals with how users access digital resources Feb 24 2025 nbsp 0183 32 Authentication is the process of verifying a user or device before allowing access to a system or resources In other words authentication means confirming that a user is who they say they are This ensures only those with
Jun 11 2024 nbsp 0183 32 In simple terms authentication is the process of verifying the identity of an individual or device trying to gain access to a system or network It acts as a gatekeeper by allowing only authorized entities to enter while Aug 19 2024 nbsp 0183 32 Authentication is the process of determining if the person or entity accessing a computing system really is who they claim to be Authentication systems make a binary decision They allow or deny access based on
More picture related to What Is Authentication In System Security

Authentication Vs Authorization What s The Difference
https://blog.hypr.com/hs-fs/hubfs/Blog/authentication-vs-authorization-chart.png?width=3552&name=authentication-vs-authorization-chart.png

Authentication And Authorization
https://www.okta.com/sites/default/files/styles/1640w_scaled/public/media/image/2020-10/Authentication_vs_Authorization.png?itok=uBFRCfww

Authentication And Authorization
https://i.ytimg.com/vi/vVN5YjU0eBw/maxresdefault.jpg
Dec 4 2023 nbsp 0183 32 Authentication is a security process followed to verify and confirm the identity of an individual device or system attempting to access a particular resource or service It ensures that the claimed identity is valid and authorized Authentication is the process of verifying the identity of a user device or entity before granting access to a system application or network It normally serves as the first line of defense in
May 8 2024 nbsp 0183 32 Authentication is the first step in the security process It acts as a gatekeeper by confirming a user s identity This is typically achieved through methods like passwords Apr 24 2025 nbsp 0183 32 By verifying the identity of users and devices authentication ensures that only authorized individuals gain access to sensitive systems and information thereby safeguarding
Multi Factor Authentication IT Security Cybersecurity
https://itnow.net/wp-content/uploads/2020/02/MFA.jpg
Types Of Authentication Your Network Security Options
https://supertokens.com/covers/types-of-authentication.png
What Is Authentication In System Security - Jun 20 2024 nbsp 0183 32 Verifying the identification of a person or system is called authentication Authentication serves as the primary barrier against cyberattacks and data leaks A key