Security Guard Another Word IT security protects an organization s computer systems networks an digital data from unauthorized access data breaches cyberattacks and other malicious activity
Information security InfoSec is the protection of important information against unauthorized access disclosure use alteration or disruption What is data security Data security is the practice of protecting digital information from unauthorized access corruption or theft throughout its lifecycle It spans both physical and digital
Security Guard Another Word
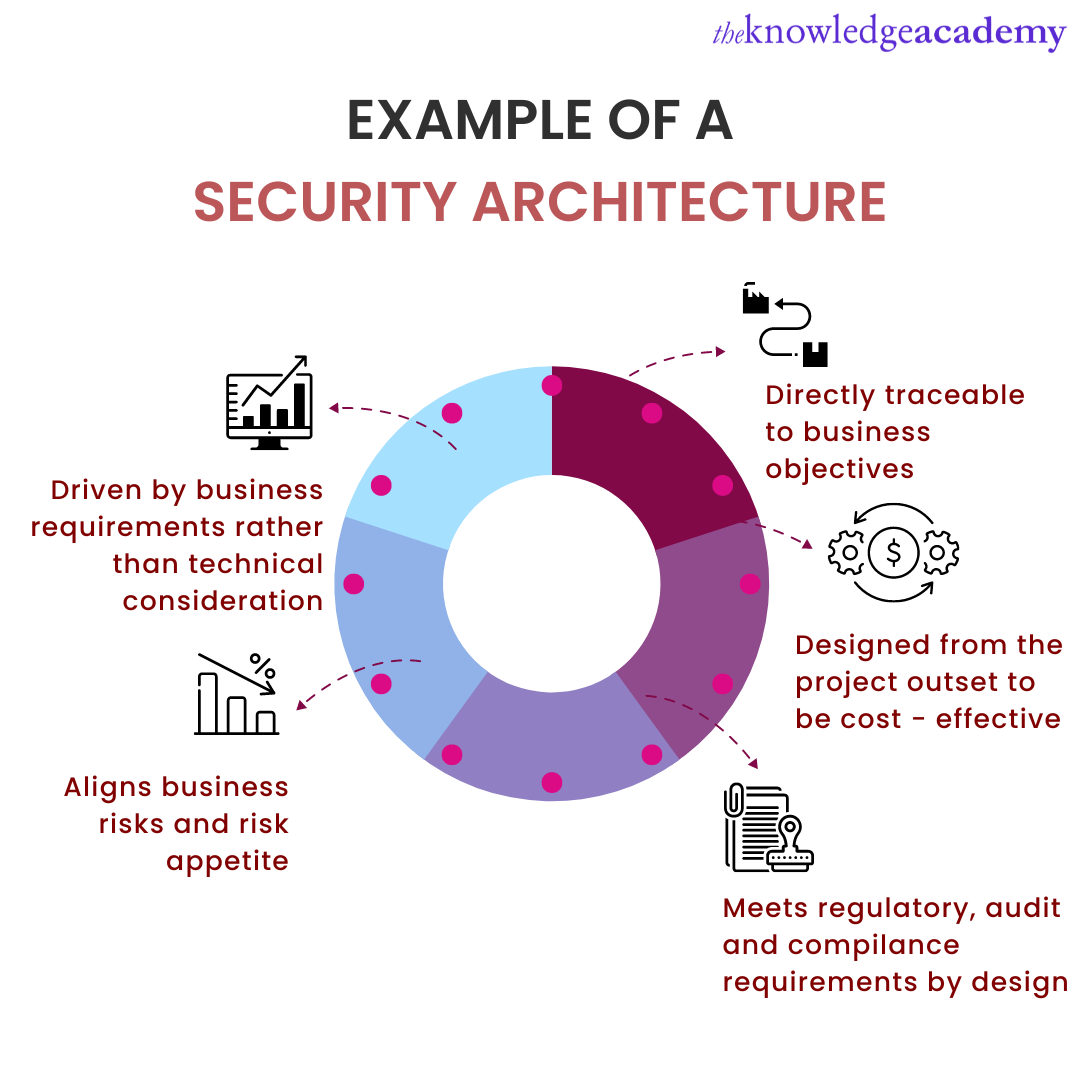
Security Guard Another Word
https://www.theknowledgeacademy.com/_files/images/Example_of_a_Security_Architecture.png

Types Of Cyber Security Positions At Callum Winter irving Blog
https://testvox.com/wp-content/uploads/2023/02/types-of-cyber-security-attack-1024x1024.jpg

Three Important Cybersecurity Considerations
https://itnow.net/wp-content/uploads/2022/10/Cyber-Security-Pic-1024x1024.jpg
API security is a set of practices and procedures that protect application programming interfaces APIs and the data they transmit from misuse malicious bot attacks and other cybersecurity threats SOAR for security orchestration automation and response is a software solution that enables security teams to integrate and coordinate separate security tools automate repetitive tasks and streamline
IBM Security develops intelligent enterprise security solutions and services to help your business prepare today for the cybersecurity threats of tomorrow Leverage educational content like blogs articles videos courses reports and more crafted by IBM experts on emerging security and identity technologies
More picture related to Security Guard Another Word

First Use Of Data Flow Diagrams For Cybersecurity Flow Syste
https://edrawcloudpublicus.s3.amazonaws.com/edrawimage/work/2022-12-7/1670384778/main.png

BroadBand Nation Cybersecurity Career Pathway INFOGRAPHIC
https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgxYeYfVaIAkEgM-k56qUgDLzoze77T4u-8sbPi5SAh3pAqrdoJN3CyYtn94dJmA4678br6lfyUp4VIpYDEFD5yLNyyP_b4mpvtQ6yBaqqz1URmbmNmgtESOvvFZUcRreSRWSegIZc85Z5hloGPMk265aajpUQWZI_IP2QYfwqoBWbz3B_Jiw/s3000/Cybersecurity Career Pathway.jpg

What Is Data Encryption Bitdefender Cyberpedia
https://blogapp.bitdefender.com/cyberpedia/content/images/2022/08/Principles-of-information-security.jpg
Mobile device security refers to being free from danger or risk of an asset loss or data loss by using mobile computers and communication hardware La seguridad inform 225 tica protege los sistemas inform 225 ticos las redes y los datos digitales de una organizaci 243 n contra el acceso no autorizado las filtraciones de datos los ataques cibern 233 ticos y
[desc-10] [desc-11]

Best Cyber Security Awareness Tips InfosecTrain
https://www.infosectrain.com/wp-content/uploads/2022/10/Best-Cybersecurity-Awareness-Tips-1.jpg
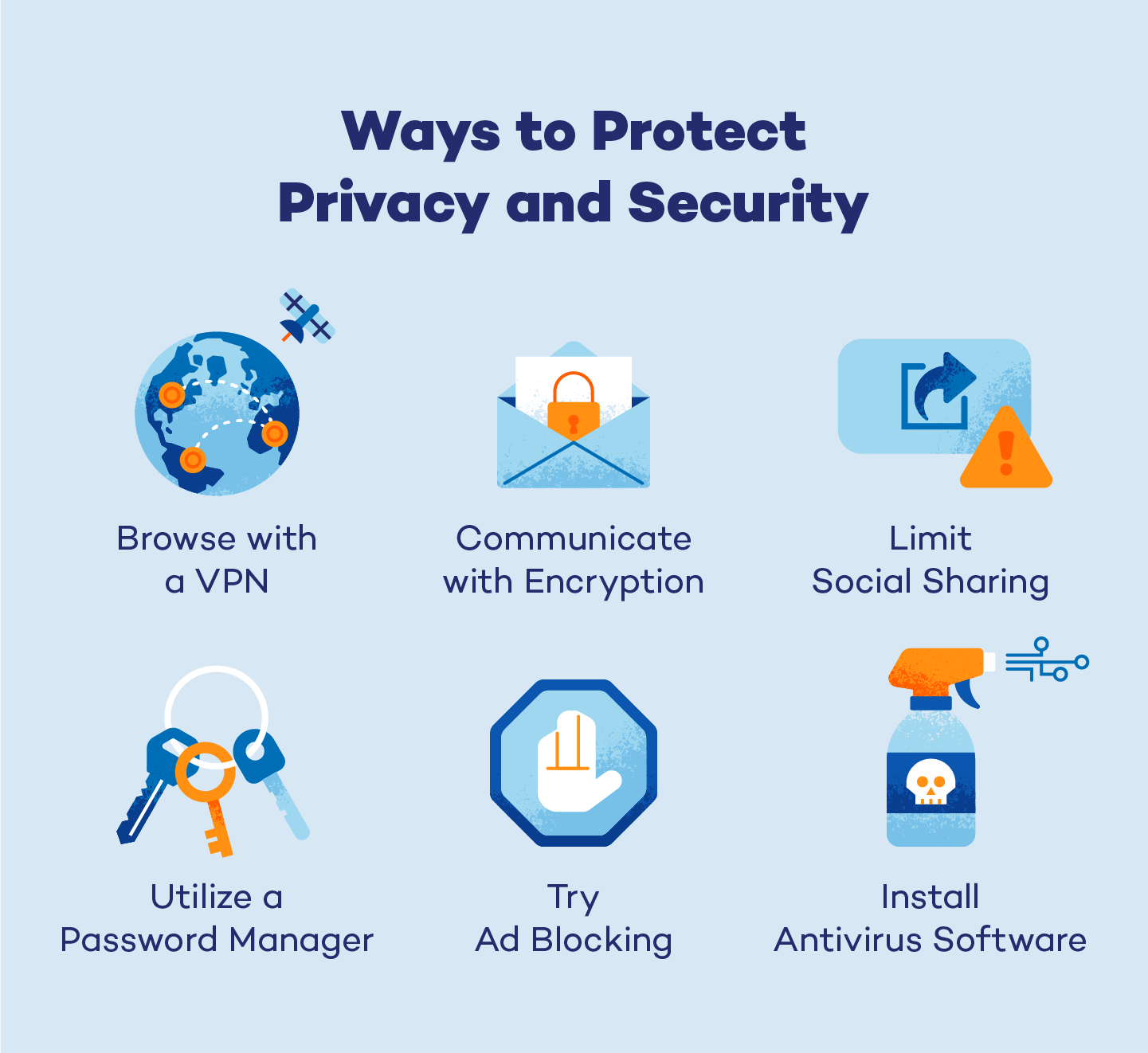
Privacy Vs Security Panda Security
https://www.pandasecurity.com/en/mediacenter/src/uploads/2023/06/privacy-security-protection.png
Security Guard Another Word - SOAR for security orchestration automation and response is a software solution that enables security teams to integrate and coordinate separate security tools automate repetitive tasks and streamline