Keycloak Authentication Flow Example Jan 16 2018 nbsp 0183 32 Running keycloak on standalone mode and created a micro service by using node js adapter for authenticating api calls jwt token from the keyclaok is sending along with each api calls it will only
Apr 16 2018 nbsp 0183 32 Old answer for Keycloak up to 16 1 1 and Keycloak legacy 17 Publish port 8443 HTTPS and use it instead of 8080 HTTP docker run name keycloak e KEYCLOAK USER myadmin e KEYCLOAK PASSWORD mypassword p 8443 8443 jboss keycloak Keycloak generates self signed cert for https in this setup Of course this is not Jul 27 2017 nbsp 0183 32 According to the version 18 release note Keycloak does not support logout with redirect uri anymore you need to include post logout redirect uri and id token hint as parameters Please check the answer of this question for more information keycloak using react user can login but when I try logout I get a message quot Invalid parameter redirect
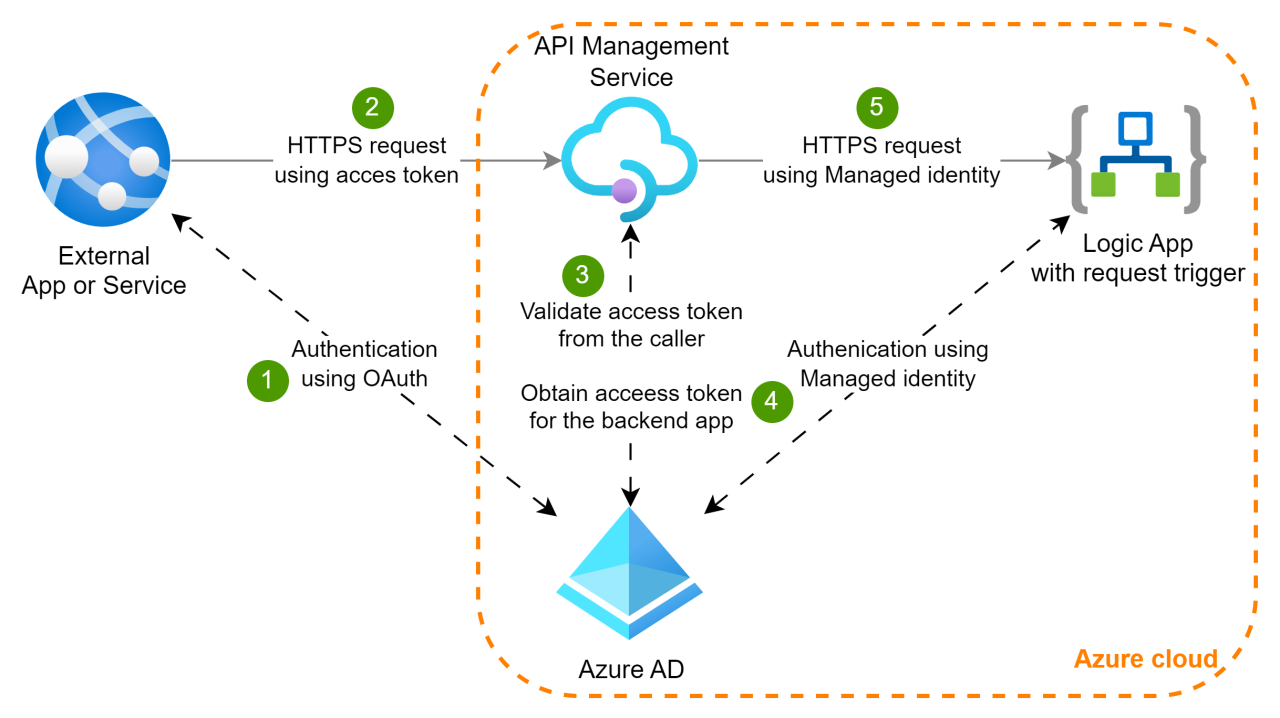
Keycloak Authentication Flow Example

Keycloak Authentication Flow Example
https://www.swimlane.com/assets/uploads/images/OAuth2-Authentication-Diagram-2.png
Deep diver Hardening Authentication And Authorization 54 OFF
https://media.licdn.com/dms/image/D5612AQHqenUyUZPBhw/article-cover_image-shrink_720_1280/0/1681189891659?e=2147483647&v=beta&t=jswLkf29tBBmyFaSqwmUVyz-iMBTEiSaFJdKEqcztnE
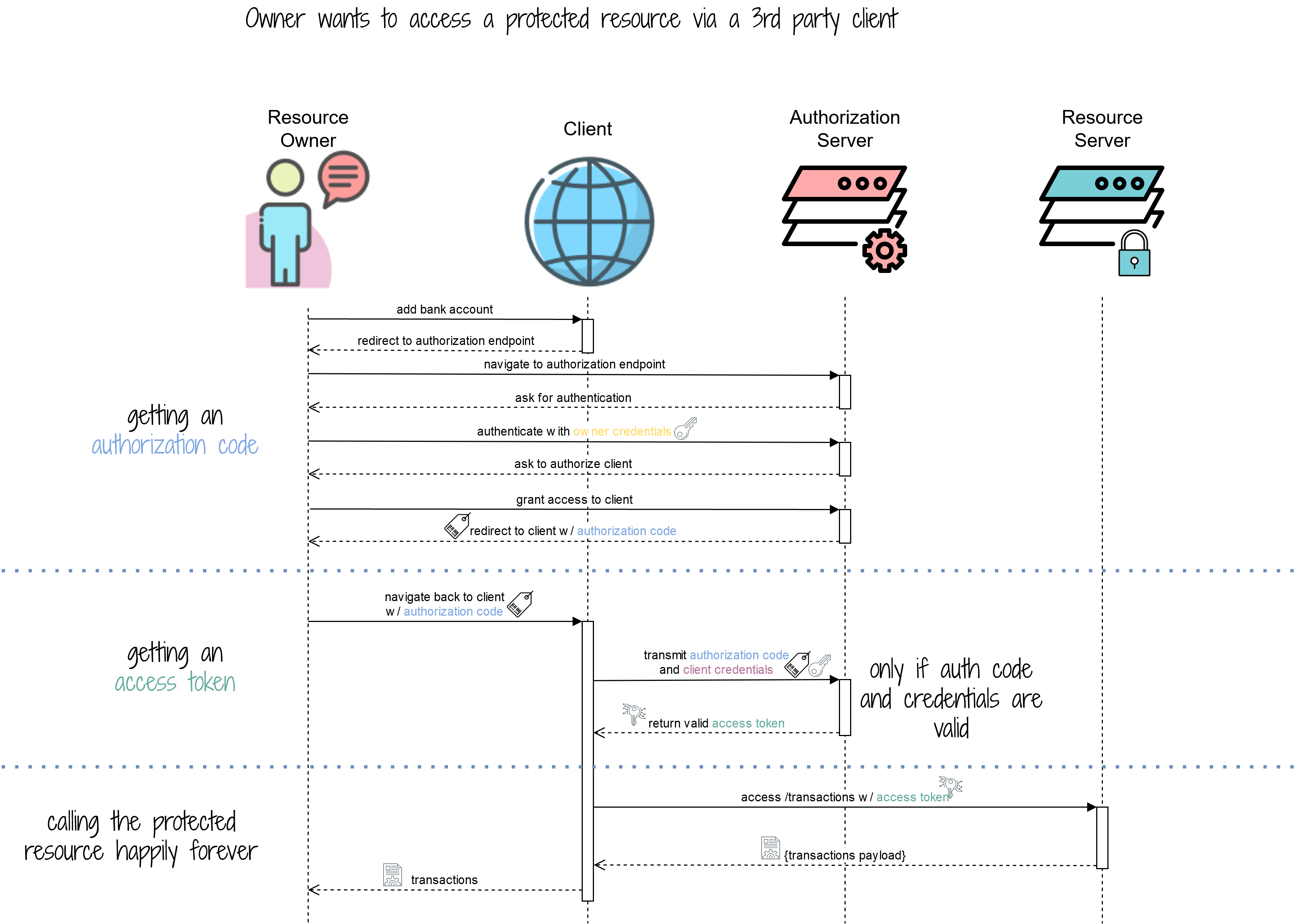
Oauth
https://www.marcobehler.com/images/guides/oauth2/oauth2_flow_v2-2dce11b4.png
Your rational was good Unfortunately the problem is that Keycloak does not consider the role attributes to be user attributes Consequently your mapper of quot user attribute quot type has no effect Hence nothing is added to the JWT token Currently there is an open feature in the Keycloak GitHub repo to handle this situation Feb 22 2015 nbsp 0183 32 We are not interested in using Keycloak s own client library we want to use standard OAuth2 OpenID Connect client libraries as the client applications using the keycloak server will be written in a wide range of languages PHP Ruby Node Java C Angular Therefore the examples that use the Keycloak client aren t of use for us
Jun 30 2016 nbsp 0183 32 In Keycloak KC one can explicitly set the access token lifespan ATL at the realm and client levels Those options are not available for the ID token lifespan but KC will make it the same as the ATL Therefore when one changes the ATL one indirectly sets the ID token Jun 13 2020 nbsp 0183 32 In Keycloak admin Console you can configure Mappers under your client Add a builtin Mapper of type quot User Realm Role quot then open its configuration e g change Token Claim Name if you want Client roles can be configured similarly but they are returned by default in the token under the name resource access client id roles The the client side you can parse
More picture related to Keycloak Authentication Flow Example
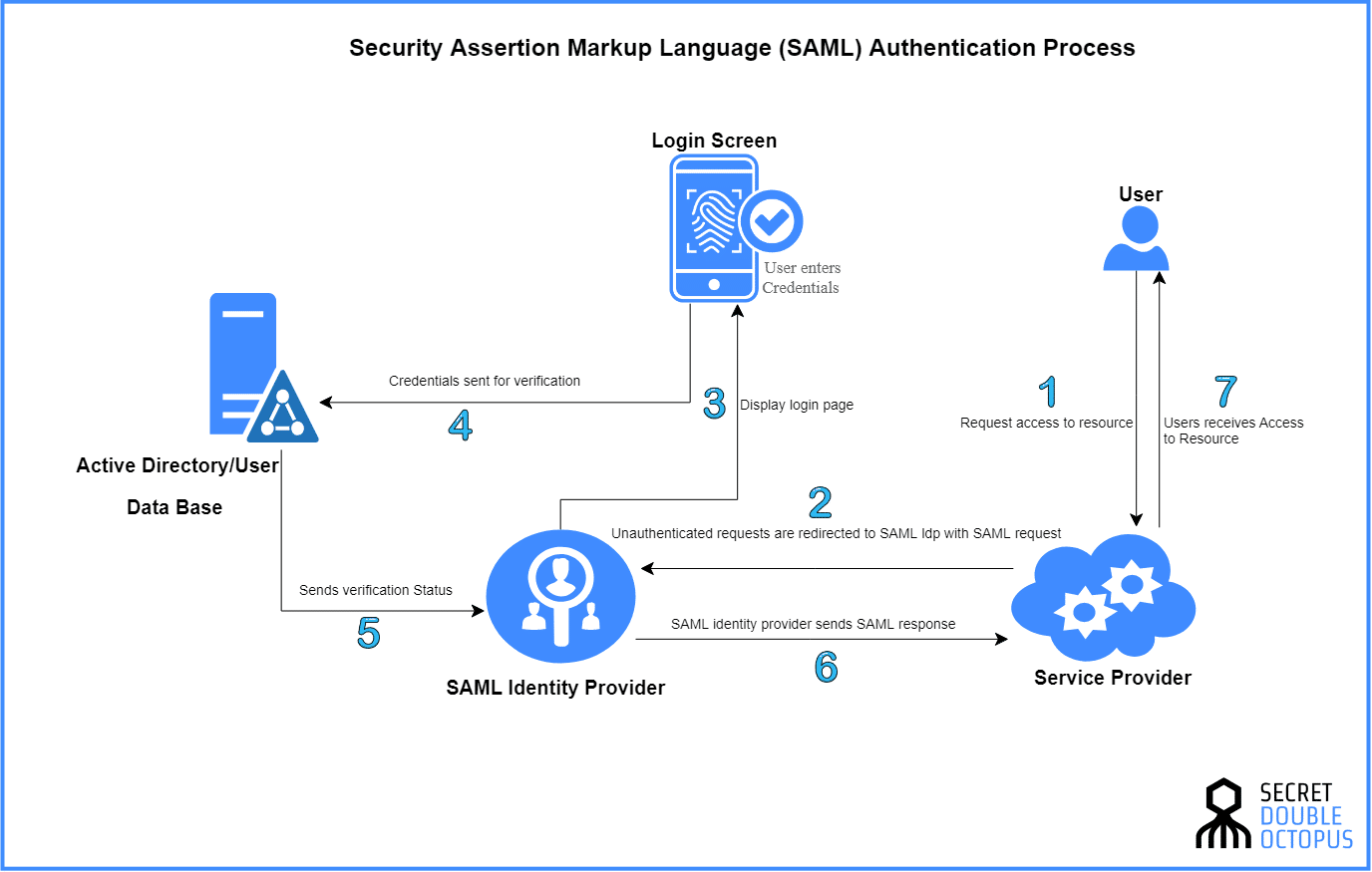
Implementing SAML Authentication In Enterprise SaaS Applicat EroFound
https://frontegg.com/wp-content/uploads/2021/07/SAML.png
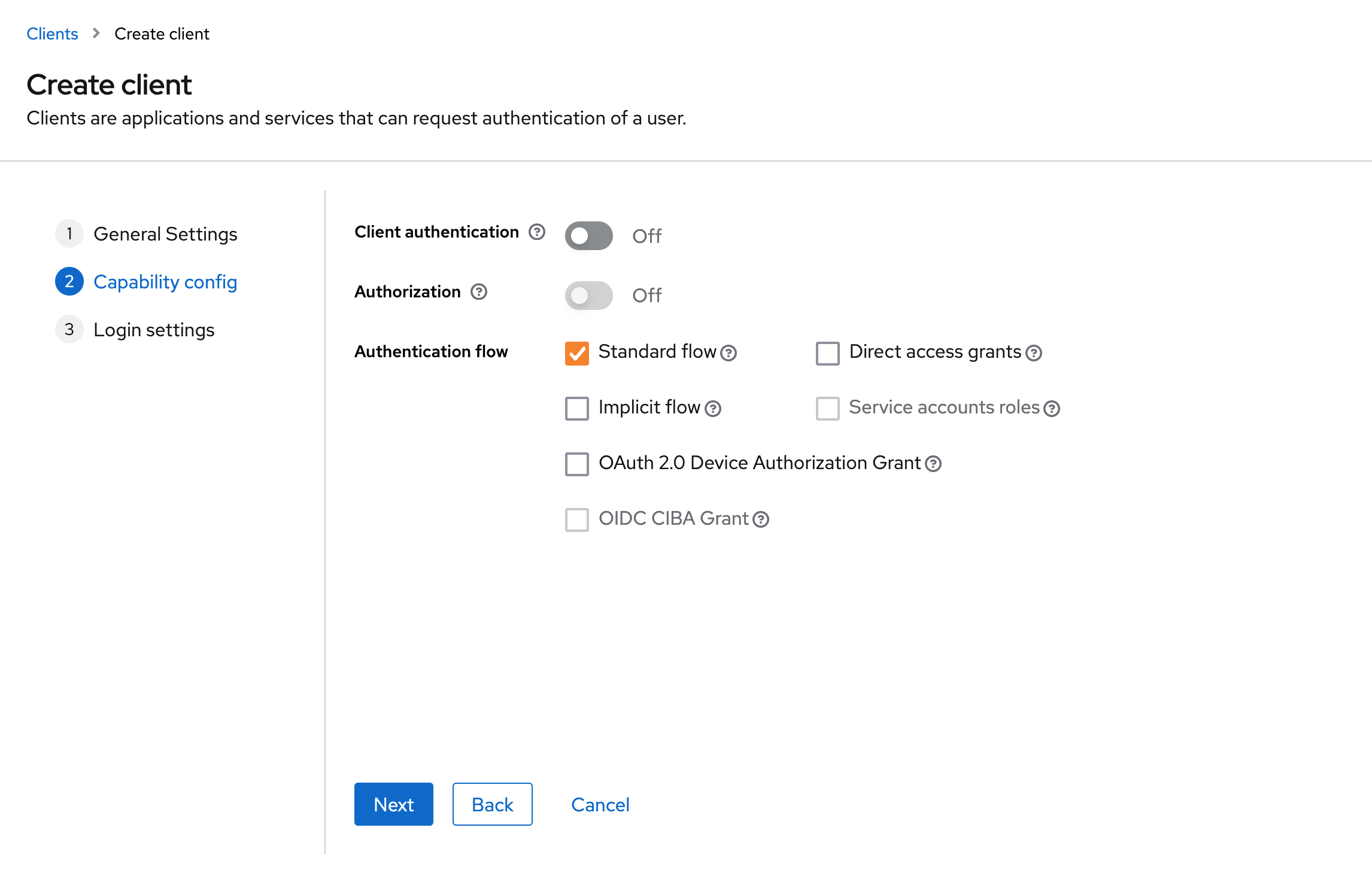
Keycloak OpenFaaS
https://docs.openfaas.com/images/oidc-configuration/keycloak/keycloak-auth-flow.png
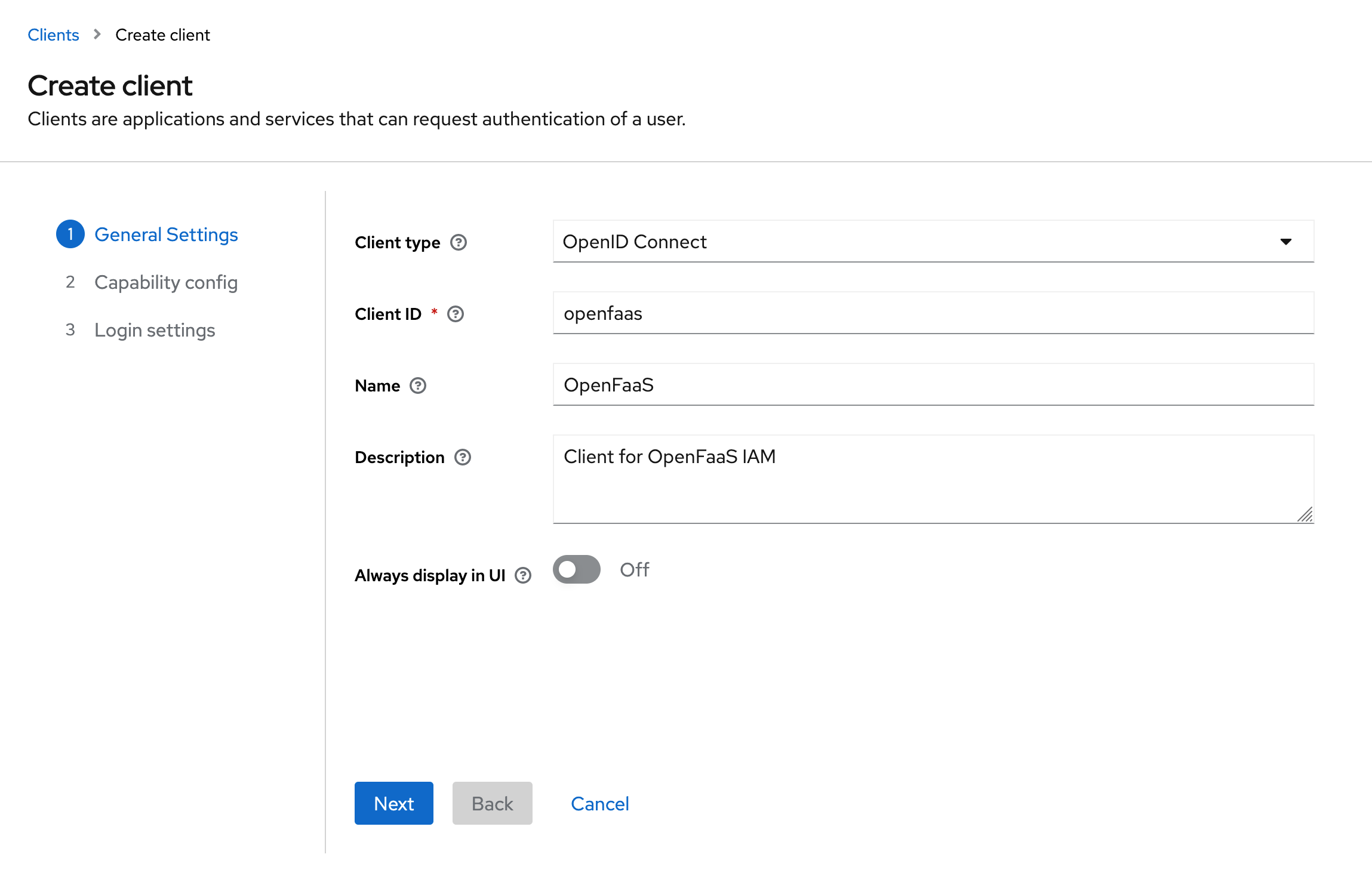
Keycloak OpenFaaS
https://docs.openfaas.com/images/oidc-configuration/keycloak/keycloak-general-settings.png
Aug 27 2018 nbsp 0183 32 Keycloak refresh token lifetime is 1800 seconds amp quot refresh expires in amp quot 1800 How to specify different expiration time In Keycloak admin UI only access token lifespan can be specified Feb 5 2023 nbsp 0183 32 So If I understand you correctly U have a custom implementation of the Authenticator interface to register it in keyckoak you also need AuthenticatorFactory implementation and add the path to it into the config file with the name org keycloak authentication AuthenticatorFactory
[desc-10] [desc-11]
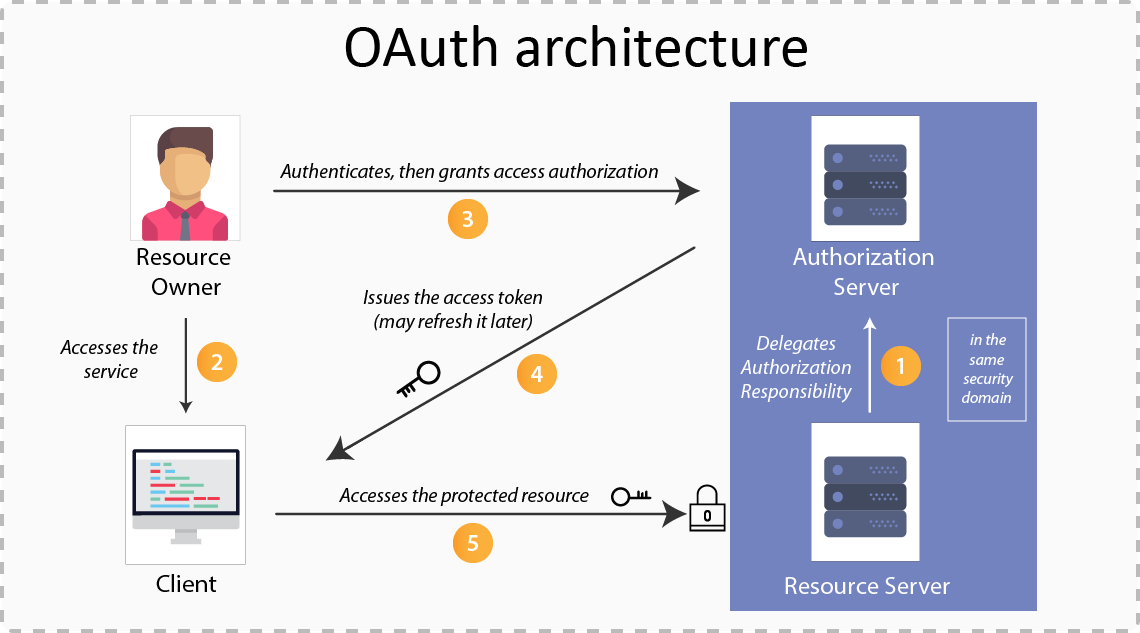
Application Authorization
https://innovationm.co/wp-content/uploads/2018/06/Oauth-architecture.png
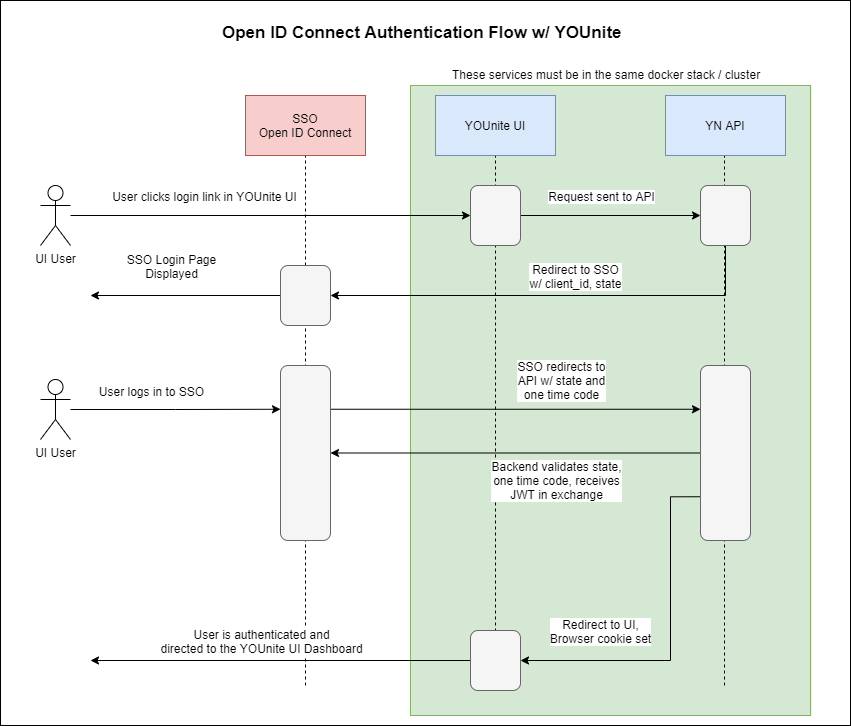
Sso Client
https://younite.us/resources/images/openIdConnectFlow.png
Keycloak Authentication Flow Example - Jun 30 2016 nbsp 0183 32 In Keycloak KC one can explicitly set the access token lifespan ATL at the realm and client levels Those options are not available for the ID token lifespan but KC will make it the same as the ATL Therefore when one changes the ATL one indirectly sets the ID token