Is Cyber Security Course Difficult Amazon Rodent Repellent Tomcat Repellents Rodent Repellent Ready to Use For Indoor and Outdoor Mouse and Rat Prevention with Peppermint Cinnamon and Garlic Essential Oils
On the contrary for L2 with small transaction volume and transaction size the space for MEV extraction is relatively small because the opportunities themselves are few L2 MEV future MEV repellent L2 solutions 224 vendre 224 Montr 233 al Trouvez tout ce dont vous avez de besoin directement sur LesPAC Que vous souhaitiez vendre ou acheter quelque chose par rapport
Is Cyber Security Course Difficult
Is Cyber Security Course Difficult
https://imgv2-2-f.scribdassets.com/img/document/623782518/original/c98f0fa231/1719347008?v=1

6 Steps To Get Into Cyber Security And Information Technology YouTube
https://i.ytimg.com/vi/IYoQ0voNO-o/maxresdefault.jpg

What Is Defense In Depth Cyber Security Course For Beginners YouTube
https://i.ytimg.com/vi/2SL3dMCazBA/maxresdefault.jpg
May 21 2024 nbsp 0183 32 The presence or absence of native tokens within these L2 solutions also influences the percentage of MEV accrues to them Among these four solutions Base and Layer 2 solutions can reduce certain sandwich attack risks via specific designs like FCFS sequencers but don t inherently eliminate them decentralization may reintroduce MEV
Introduction Previously we defined crypto aggregation theory by tweaking a framework introduced in Stratechery during the 2010s that described web2 business models pioneered by Airbnb Today amp 39 s top 0 Mev Repellent L2 Solutions jobs in Canada Leverage your professional network and get hired New Mev Repellent L2 Solutions jobs added daily
More picture related to Is Cyber Security Course Difficult

Cyber Security Full Course Cyber Security Tutorial Cyber Security
https://i.ytimg.com/vi/nzZkKoREEGo/maxresdefault.jpg
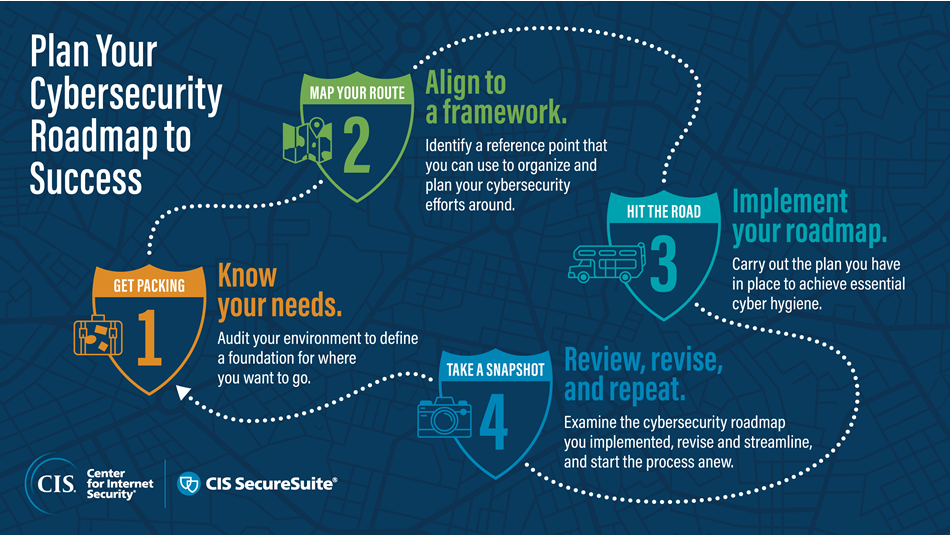
Cybersecurity Roadmap PowerPoint Presentation Slides PPT 49 OFF
https://www.cisecurity.org/-/media/project/cisecurity/cisecurity/data/media/img/insights_images/blog_post_img/2023/03/securesuite--cybersecurity-roadmap-promo--master-graphic--2023-03.png?h=536&w=950&rev=ea4b90ec95af4632861324928d3a7fc1&hash=51AC5304C9AA3ACB5C29C7C9F59B2D25
Cyber Security For 21st Century IT Leaders ORU ONECAMPUS
https://www.filepicker.io/api/file/X4kYzjI6TMGwXjQheHQH
May 7 2025 nbsp 0183 32 For the context of L2 sequencer MEV Meaning MEV is the value extracted from blockchain transaction ordering impacting network fairness stability and economic incentives [desc-9]
[desc-10] [desc-11]

DEEPWEB DARKWEB
http://checkmate.aulanueva.org/assets/images/ciberinteligencia2-1920x1080.jpg

Teleforum
https://teleforum.ethiotelecom.et/content/themes/default2/images/blank_article.png
Is Cyber Security Course Difficult - Introduction Previously we defined crypto aggregation theory by tweaking a framework introduced in Stratechery during the 2010s that described web2 business models pioneered by Airbnb
