How To Write An Argument Paper Example Nov 1 2023 nbsp 0183 32 Authentication technology provides access control for systems by checking to see if a user s credentials match the credentials in a database of authorized users or a data
Authentication from Greek authentikos quot real genuine quot from authentes quot author quot is the act of proving an assertion such as the identity of a computer system user Authentication is more than a definition when it comes to identity Learn about all the ways authentication is used as the core of securing your business
How To Write An Argument Paper Example

How To Write An Argument Paper Example
https://i.pinimg.com/originals/2c/ef/d9/2cefd9158d3983af68cdf78625938fd6.jpg

How To Write An Argumentative Essay With Example YouTube
https://i.ytimg.com/vi/VZKUeEBryOk/maxresdefault.jpg

Argumentative Writing Google Search Aufforderungen Zum Schreiben
https://i.pinimg.com/originals/da/e7/7d/dae77d1aa781a6b757e25a4f39283d4c.png
In cyber security authentication is the process of verifying an entity s identity Learn about the different types of authentication that access control systems use Sep 27 2024 nbsp 0183 32 Authentication is verifying a user s or system s identity Types Single Factor Authentication and Two Factor Authentication
AUTHENTICATION definition 1 the process of proving that something is real true or what people say it is 2 the process Learn more Apr 8 2025 nbsp 0183 32 User authentication is central to this security paradigm as it refers to the mechanism by which the identity of a user is first confirmed before being granted access to a resource In
More picture related to How To Write An Argument Paper Example

25 Counterargument Examples 2024
https://helpfulprofessor.com/wp-content/uploads/2023/09/counterargument-examples-and-definition-1024x724.jpg
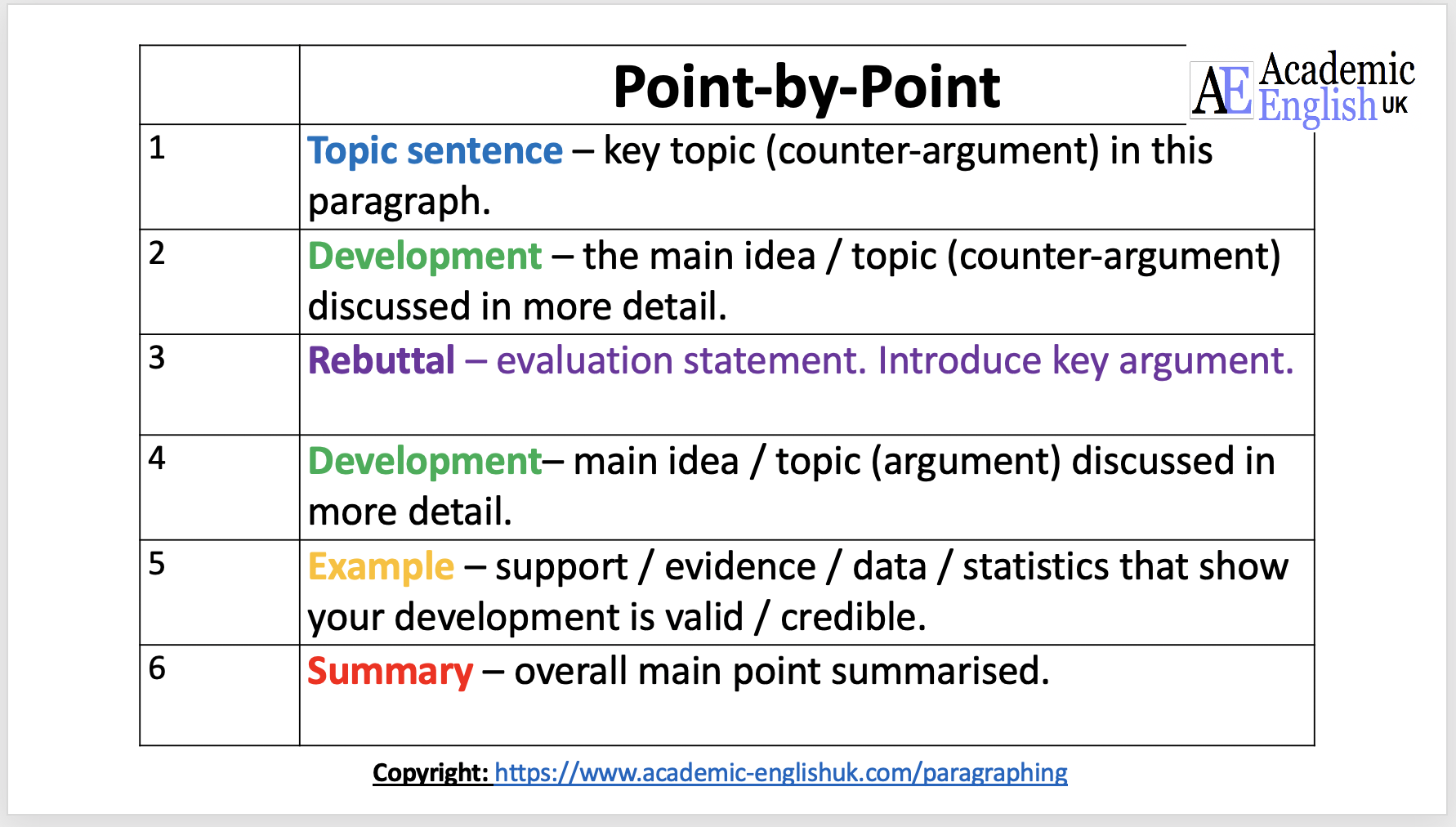
Essay Structure Argument Essay Organisation Academic English UK
https://academic-englishuk.com/wp-content/uploads/2020/03/Point-by-point-paragraph-structure-by-AEUK-.png
/write-an-argument-essay-1856986-FINAL-5b75852cc9e77c00502429a2.png)
Take Your Position
https://www.thoughtco.com/thmb/fuZtvZDWnSadaWZp8BopChAVb5g=/1500x1000/filters:fill(auto,1)/write-an-argument-essay-1856986-FINAL-5b75852cc9e77c00502429a2.png
Oct 13 2022 nbsp 0183 32 Three factor authentication adalah jenis MFA yang menggabungkan tiga jenis faktor misalnya seperti faktor pengetahuan berupa kata sandi faktor kepemilikan berupa Aug 19 2024 nbsp 0183 32 Authentication vs Authorization What s the Difference Authentication is the gatekeeper that decides who gains access to an organization s resources including critical
[desc-10] [desc-11]

Free Argumentative Essay Templates Editable And Printable
https://images.template.net/436791/Rogerian-Argumentative-Essay-Template-edit-online.png

Argumentative Essay Definition Outline And Examples 7ESL
https://7esl.com/wp-content/uploads/2020/04/Argumentative-Essay.jpg
How To Write An Argument Paper Example - AUTHENTICATION definition 1 the process of proving that something is real true or what people say it is 2 the process Learn more