How Does Distributed Hash Table Work Today September 7th 2017 WikiLeaks publishes four secret documents from the Protego project of the CIA along with 37 related documents proprietary hardware software manuals from Microchip Technology Inc The project was maintained between 2014 and 2015
CIA report into shoring up Afghan war support in Western Europe 11 Mar 2010 Update to over 40 billion euro in 28167 claims made against the Kaupthing Bank 3 Mar 2010 Nov 9 2017 nbsp 0183 32 Source code and analysis for CIA software projects including those described in the Vault7 series This publication will enable investigative journalists forensic experts and the general public to better identify and understand covert CIA infrastructure components
How Does Distributed Hash Table Work

How Does Distributed Hash Table Work
https://i.ytimg.com/vi/FsfRsGFHuv4/maxresdefault.jpg
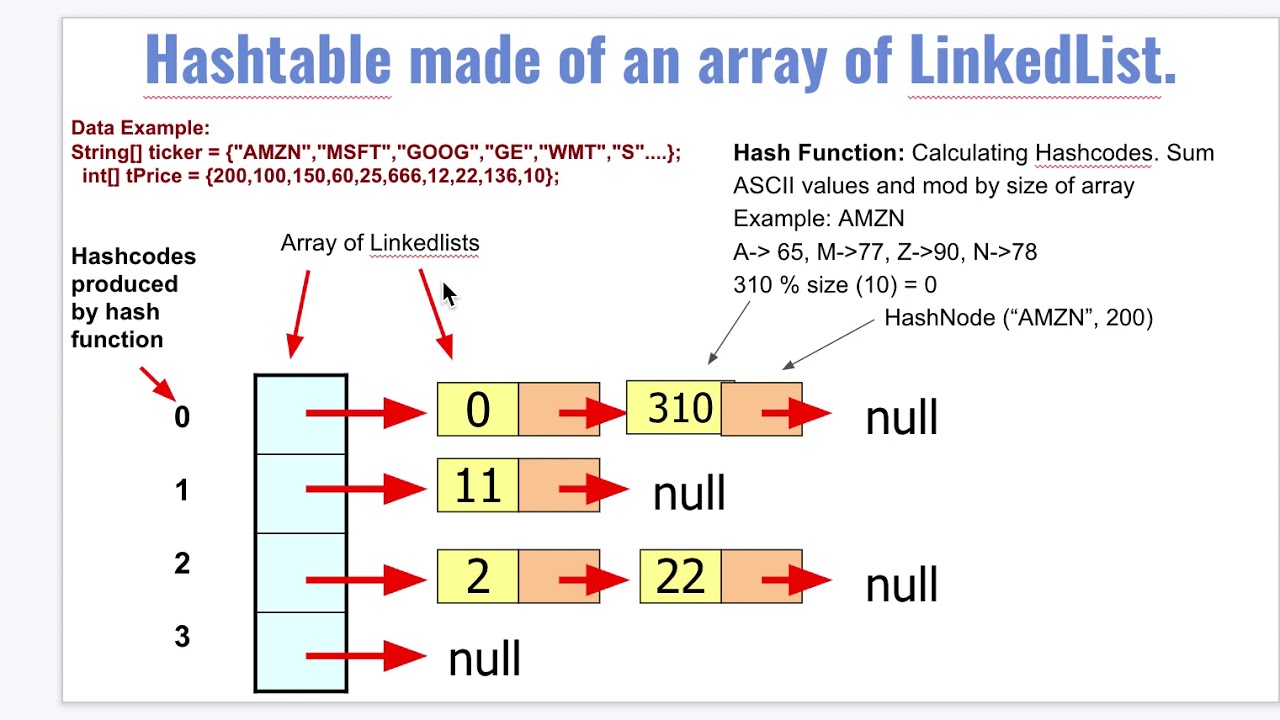
Hash Tables Explained In Simple Terms YouTube
https://i.ytimg.com/vi/Zeb685c7wrM/maxresdefault.jpg

Data Structures Hash Tables How Do They Work Internally YouTube
https://i.ytimg.com/vi/6D9mRll58Kg/maxresdefault.jpg
Today August 24th 2017 WikiLeaks publishes secret documents from the cyber operations the CIA conducts against liaison services which includes NSA DHS and FBI Today 21 December 2018 WikiLeaks publishes a searchable database of more than 16 000 procurement requests posted by United States embassies around the world
Today August 24th 2017 WikiLeaks publishes secret documents from the cyber operations the CIA conducts against liaison services which includes NSA DHS and FBI Dec 21 2014 nbsp 0183 32 CIA Assessment on Surviving Secondary Screening at Airports While Maintaining Cover WikiLeaks release December 21 2014 This is a secret document produced by the CIA s CHECKPOINT Identity and T ravel Intelligen ce Program to explain and advise CIA operatives on how to deal with secondary screening at airports as they travel
More picture related to How Does Distributed Hash Table Work
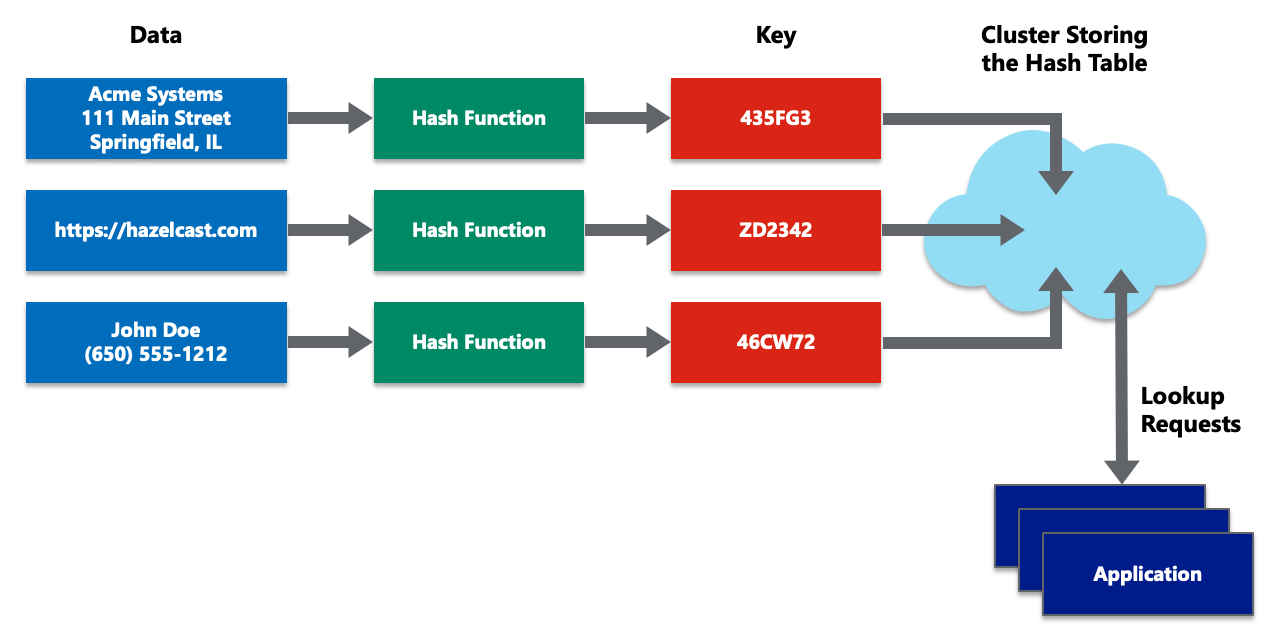
What Is A Distributed Hash Table Hazelcast
https://hazelcast.com/wp-content/uploads/2021/12/diagram-distributed-hash-table.png
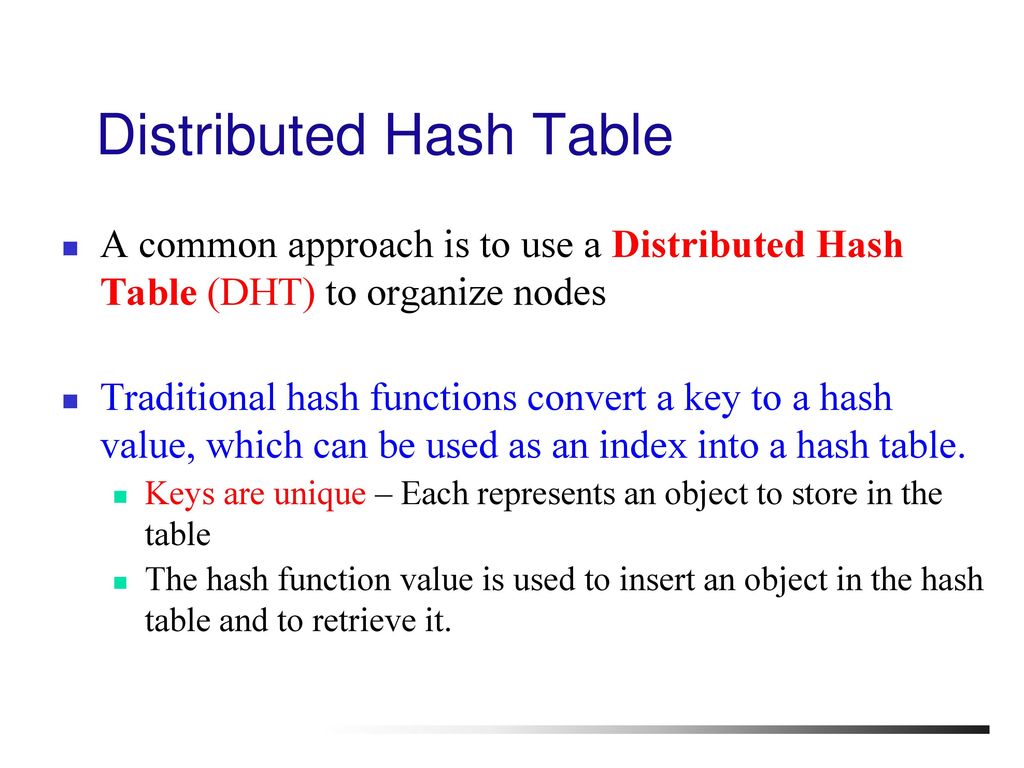
Distributed Hash Tables Ppt Download
https://slideplayer.com/slide/13331071/80/images/2/Distributed+Hash+Table.jpg

Hash Tables CodePath Guides Cliffnotes
https://i.imgur.com/bEIWPaQ.png
Today August 24th 2017 WikiLeaks publishes secret documents from the cyber operations the CIA conducts against liaison services which includes NSA DHS and FBI How to contact WikiLeaks What is Tor Tips for Sources After Submitting Vault 7 CIA Hacking Tools Revealed Releases Documents Navigation
[desc-10] [desc-11]
+Why+DHTs.jpg)
Distributed Hash Tables Ppt Download
https://slideplayer.com/slide/15772511/88/images/2/Presentation+Outline+What+is+DHT+(Distributed+Hash+Table)+Why+DHTs.jpg

Consistent Hashing
https://hashnode.com/utility/r?url=https:%2F%2Fcdn.hashnode.com%2Fres%2Fhashnode%2Fimage%2Fupload%2Fv1663149726982%2F76sAVrpHZ.png%3Fw%3D1200%26h%3D630%26fit%3Dcrop%26crop%3Dentropy%26auto%3Dcompress%2Cformat%26format%3Dwebp%26fm%3Dpng
How Does Distributed Hash Table Work - [desc-12]