Explain Different Security Threats Explanation explication explain explanation explication
Sci SCI 1 explain 2 interpret
Explain Different Security Threats

Explain Different Security Threats
https://edrawcloudpublicus.s3.amazonaws.com/edrawimage/work/2022-12-7/1670384778/main.png

4 Common Cyber Attacks Infographic
https://www.yardsticktechnologies.com/wp-content/uploads/2021/05/4-Common-Types-of-Cyber-Attacks-Infographic-1.png
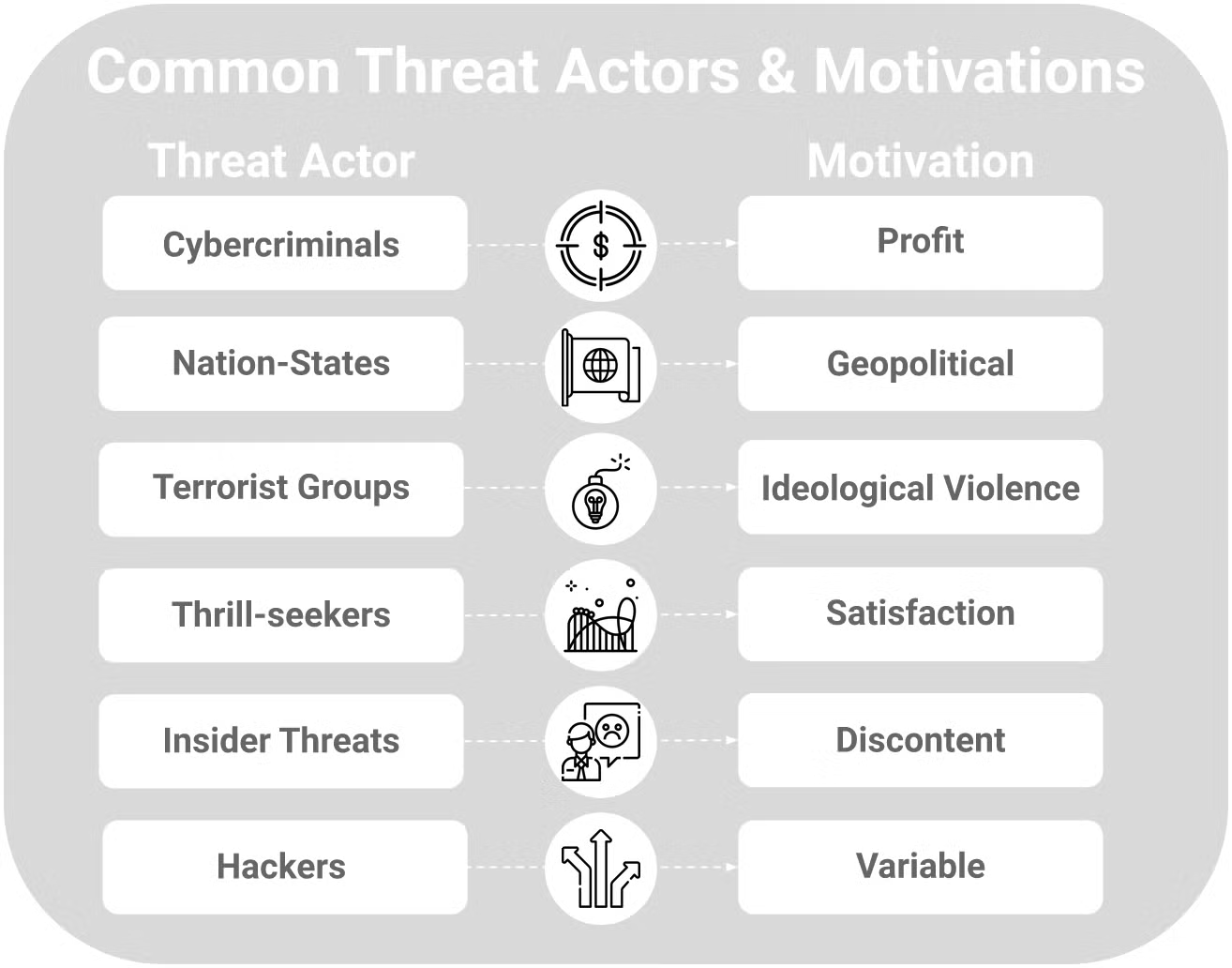
What Is A Threat Actor Types Examples Of Cyber Threat 54 OFF
https://www.sentinelone.com/wp-content/uploads/2021/06/threat-actor.png
1 2
Explain explanation explaination 22 1 In the second part of the article a considerable part of the data selected are the relevant parameters of Tm YAG crystals and it is necessary to explain or prove the reliability of the
More picture related to Explain Different Security Threats

Cyber Attack Cheat Sheet Infographic
https://infographicjournal.com/wp-content/uploads/2020/04/types-of-cyberattacks-feat.jpg

Phishing Attacks
https://wesecureapp.com/wp-content/uploads/2022/09/Phishing-Attacks.png
Technical Report Structure PenTesting Org
https://www.pentesting.org/wp-content/uploads/2024/12/control-mapping-guide.webp
Mar 10 2020 nbsp 0183 32 IEEE Transaction on neural system and rehabilitation engineering Jul 8 2010 nbsp 0183 32 Explain to him how Brazil could have lost to Holland means the explanation should be in his direction In b explain me there is no preposition quot to quot indicating the direction of the
[desc-10] [desc-11]

CS Concepts Computer Security
https://www.projectcubicle.com/wp-content/uploads/2021/04/What-is-Computer-Security-Kinds-of-Attacks-in-Computer-Security-min.png

Network Layer Model
https://www.infosectrain.com/wp-content/uploads/2023/01/7-Layers-of-the-OSI-Model.jpg
Explain Different Security Threats - [desc-13]