Encryption And Decryption In Cyber Security Javatpoint Feb 7 2024 nbsp 0183 32 Learn how encryption works and how to use it to protect data from being accessed by unauthorized users Explore benefits types implementation and more
Encryption is a key component in data security Learn how it works and find out more about the different types of encryption that are crucial to cybersecurity Jul 23 2025 nbsp 0183 32 It is a method of preserving data confidentiality by transforming it into ciphertext which can only be decoded using a unique decryption key produced at the time of the encryption or before it The conversion of plaintext into ciphertext is known as encryption
Encryption And Decryption In Cyber Security Javatpoint

Encryption And Decryption In Cyber Security Javatpoint
https://i.ytimg.com/vi/K6WM6hSgYXg/maxresdefault.jpg
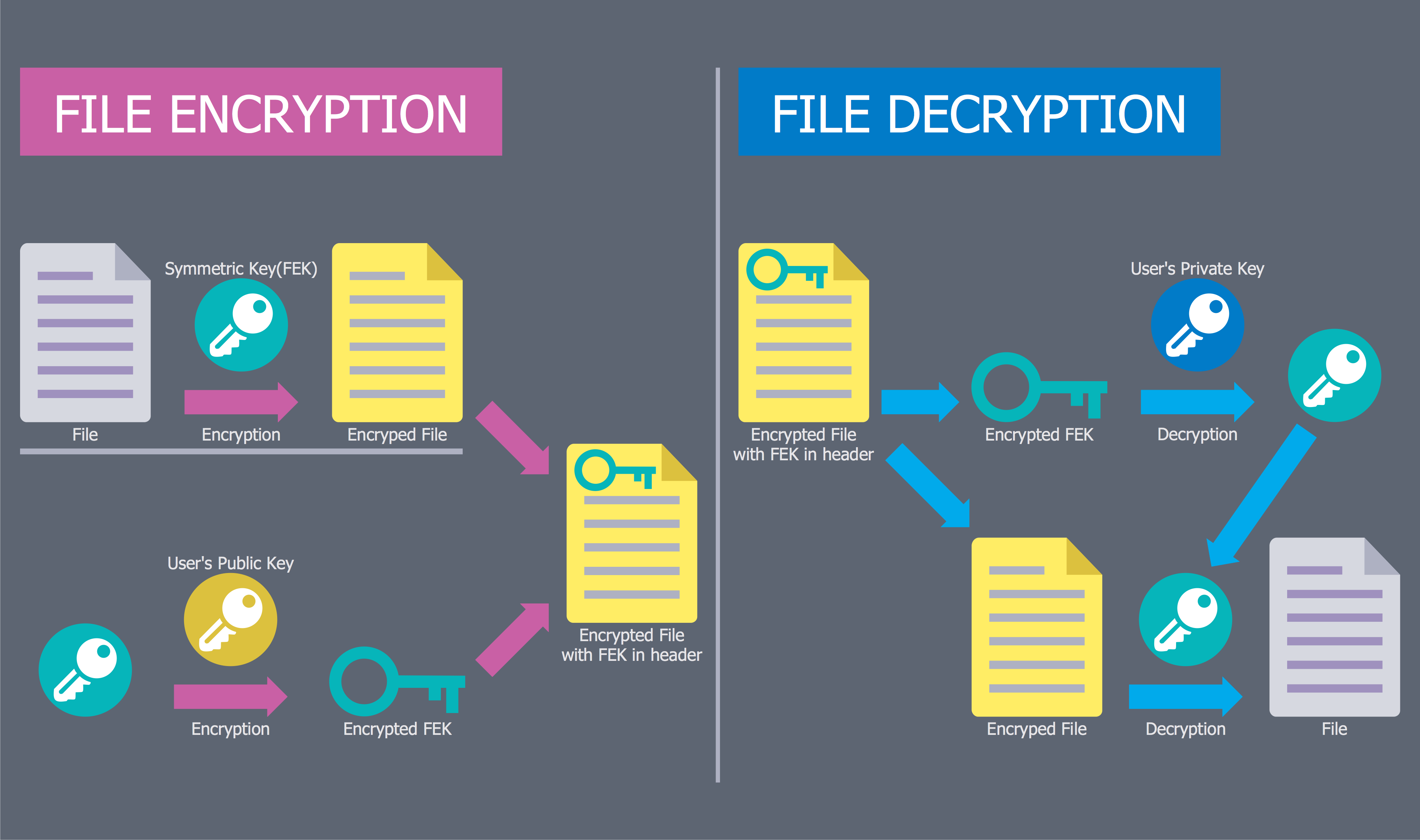
Content Decryption Module
https://www.conceptdraw.com/How-To-Guide/picture/Computer-and-Networks-Network-Security-Diagrams-EFS-Operation.png

Beginners Guide To Cryptography
https://editor.analyticsvidhya.com/uploads/11325Untitledcc2.jpg
Jul 18 2023 nbsp 0183 32 Encryption scrambles plain text into a type of secret code that hackers cybercriminals and other online snoops can t read even if they intercept it before it reaches its intended recipients Encryption is a way of scrambling data so that only authorized parties can understand the information In technical terms it is the process of converting human readable plaintext to incomprehensible text also known as ciphertext
What is Encryption Encryption is the practice of transforming readable information plaintext into an unintelligible jumble ciphertext that only authorized parties can decode with a cipher Apr 14 2022 nbsp 0183 32 Explore the fundamental concepts of encryption its processes and different types Understand how encryption secures data and communications
More picture related to Encryption And Decryption In Cyber Security Javatpoint

Schutz Vor Asymmetrischen Oder Symmetrischen Bedrohungen Shop
https://www.proofpoint.com/sites/default/files/what-is-encryption.png
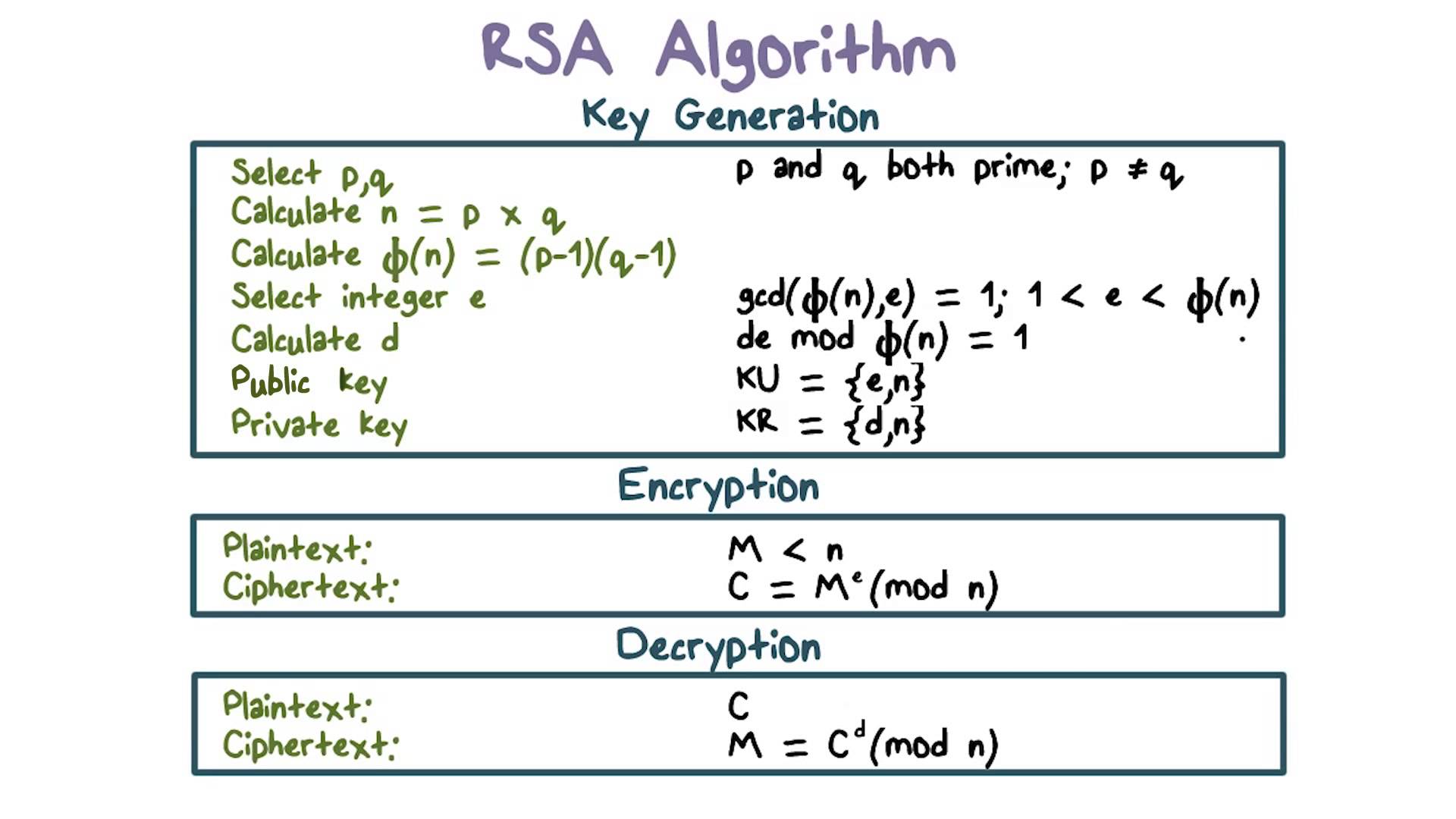
Introduction To RSA Algorithm For Cybersecurity Smart Nation DHS
https://dunmanhigh.github.io/smarticc/assets/img/2019-04-20-intro-to-rsa-1.jpg

Public Key Cryptography Algorithms
https://assets-global.website-files.com/62def148e4e23334e2e28ae1/62df01d48ccbc01d1f176292_rrss_02-1024x1024.png
Encryption is used to protect data from being stolen changed or compromised and works by scrambling data into a secret code that can only be unlocked with a unique digital key Apr 5 2024 nbsp 0183 32 Learn about encryption its benefits and how it can help protect your information Our experts will help get you up to speed on this important technology
[desc-10] [desc-11]
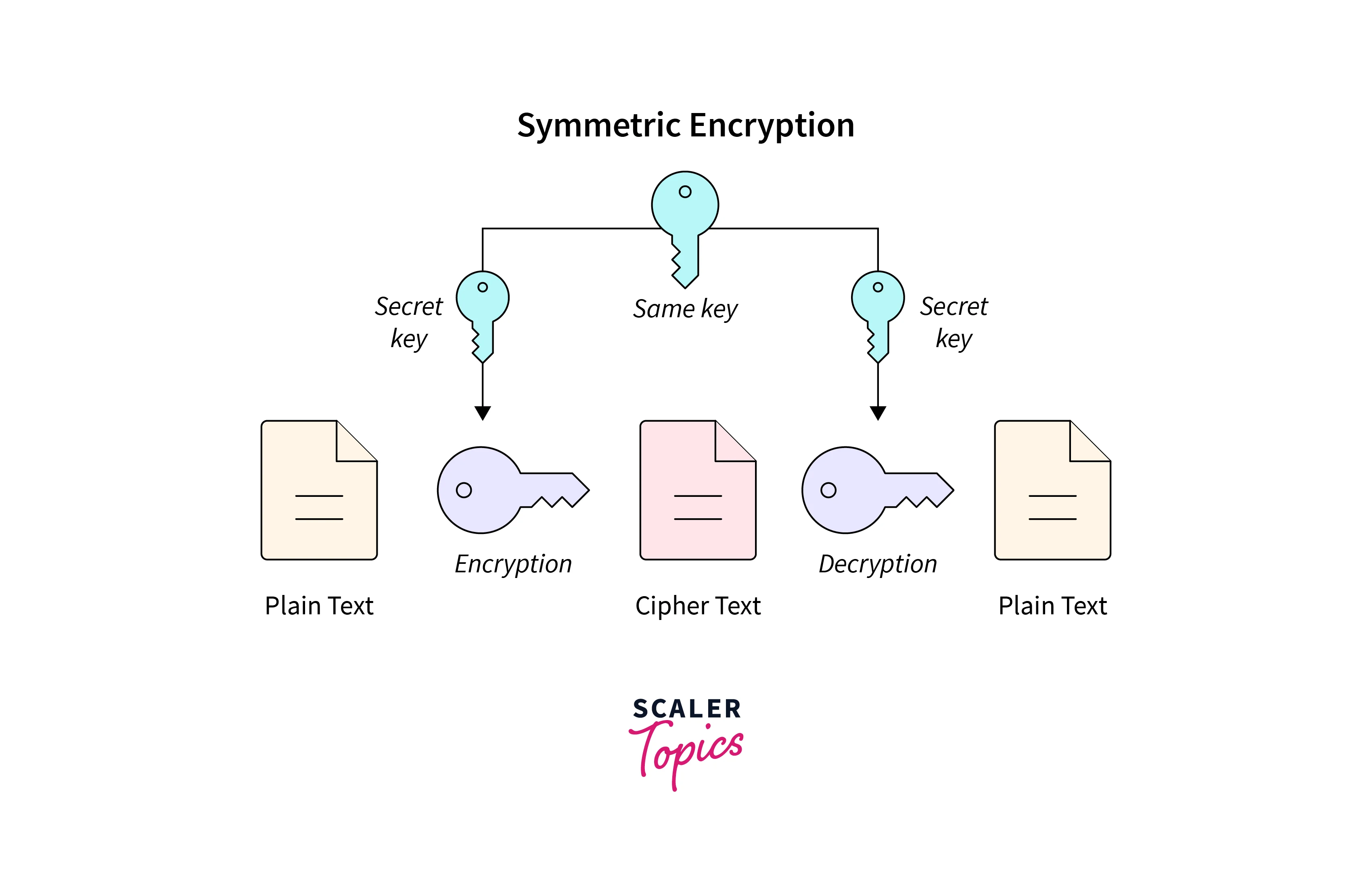
Encryption And Decryption Scaler Topics
https://www.scaler.com/topics/images/shared-key-encryption.webp
/AL_14-Blog02-4.jpg?width=1125&height=1125&name=AL_14-Blog02-4.jpg)
Information Security Vs Cybersecurity Which Should Districts Prioritize
https://blog.alludolearning.com/hs-fs/hubfs/Month 14 (January 2023)/AL_14-Blog02-4.jpg?width=1125&height=1125&name=AL_14-Blog02-4.jpg
Encryption And Decryption In Cyber Security Javatpoint - [desc-12]