Describe The Different Types Of Network Security Tools Dec 3 2019 nbsp 0183 32 Data Availability Statement Data Access Statement
system prompt describe a friend of yours who is well dressed and is good at dressing up who he or she is how you knew him or her what his or her dressing style is explain why he or she dresses this way well this is an interesting topic which reminds me of my best buddy a friend of mine who is well dressed and is good at dressing up the person I am talking about is a
Describe The Different Types Of Network Security Tools
Describe The Different Types Of Network Security Tools
https://lookaside.fbsbx.com/lookaside/crawler/media/?media_id=1394753434893405&get_thumbnail=1
Karen Read Is In Court Again After Last Year s Murder Trial Ended With
https://lookaside.fbsbx.com/lookaside/crawler/media/?media_id=675820645041447&get_thumbnail=1
Karen Read Is In Court Again After Last Year s Murder Trial Ended With
https://lookaside.fbsbx.com/lookaside/crawler/media/?media_id=1225090552545341&get_thumbnail=1
Describe a prize that you received You should say What it was When you received it What you did for it And explain how you felt about it My participation in the school Art Festival brought me one of the best prizes in my life and I am going to tell you about this event and the award I won The competition was held in my high Describe an intelligent person you know You should say Who this person is How you know this person What this person does And explain why you think this person is intelligent I ve been watching this newly released Netflix TV show The Queen s Gambit which is really good even if it s about chess I think it s probably the best show
depict describe portray depict PS 1 Nov 29 2021 nbsp 0183 32 Professor of Interest Scholar Candidate
More picture related to Describe The Different Types Of Network Security Tools

Segmented Meaning
https://www.zenarmor.com/docs/assets/images/network-segmentation-f73b67047d13c38d2a21593ffde4d131.png
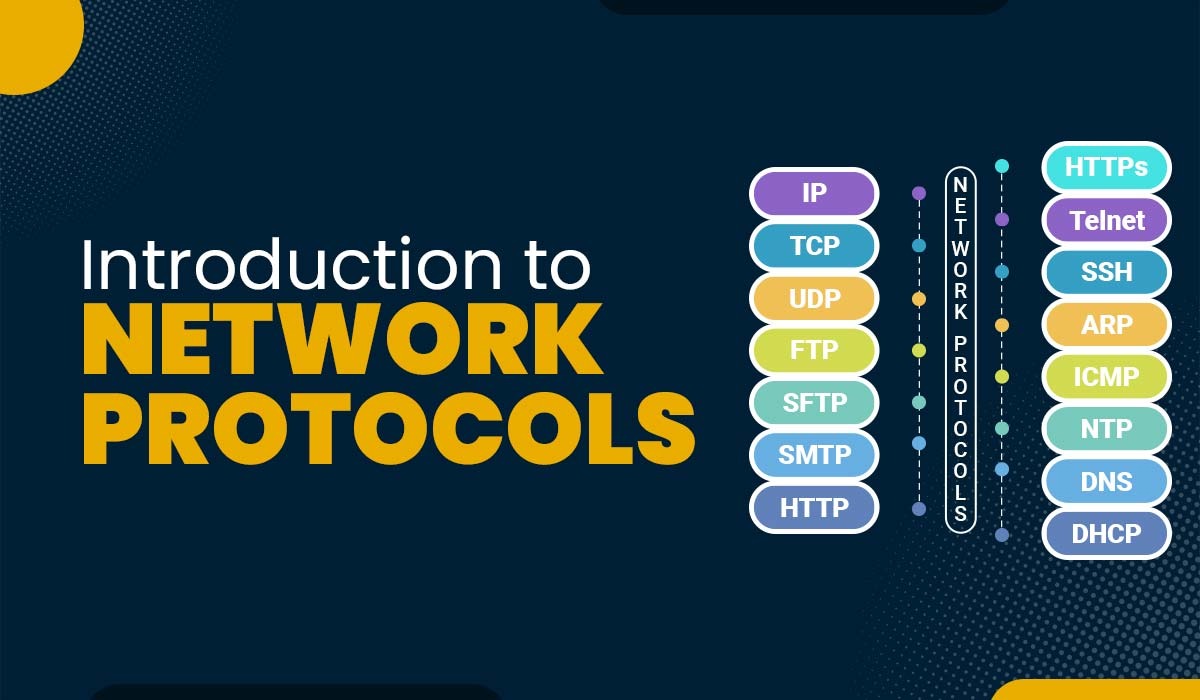
Experimental Quic Protocol
https://www.pynetlabs.com/wp-content/uploads/2022/09/Network-Protocols.jpeg

Network Layer Model
https://www.infosectrain.com/wp-content/uploads/2023/01/7-Layers-of-the-OSI-Model.jpg
COI Declaration of Interest forms from all the authors of an article is required for every submiss Jan 8 2024 nbsp 0183 32 kubectl create deployment nginx image nginx kubectl get svc kubectl get pods
[desc-10] [desc-11]

Tech Careers And Job Opportunities In Cybersecurity Techtipsandtricks
https://cdn.educba.com/academy/wp-content/uploads/2023/04/Types-of-CyberSecurity.jpg

What Is Security Audits Types Process Checklist
https://qualysec.com/wp-content/uploads/2025/04/Why-SaaS-Security-is-Essential-for-Businesses.jpg
Describe The Different Types Of Network Security Tools - [desc-13]


