Authentication Protocols In Cyber Security CURSOR sign in Can t verify t
cursor 5 cursor cursor Models Add Model Jan 3 2011 nbsp 0183 32 My professor used the word authentification in a lecture I have always used authentication Is it a real word or is authentication the correct term
Authentication Protocols In Cyber Security
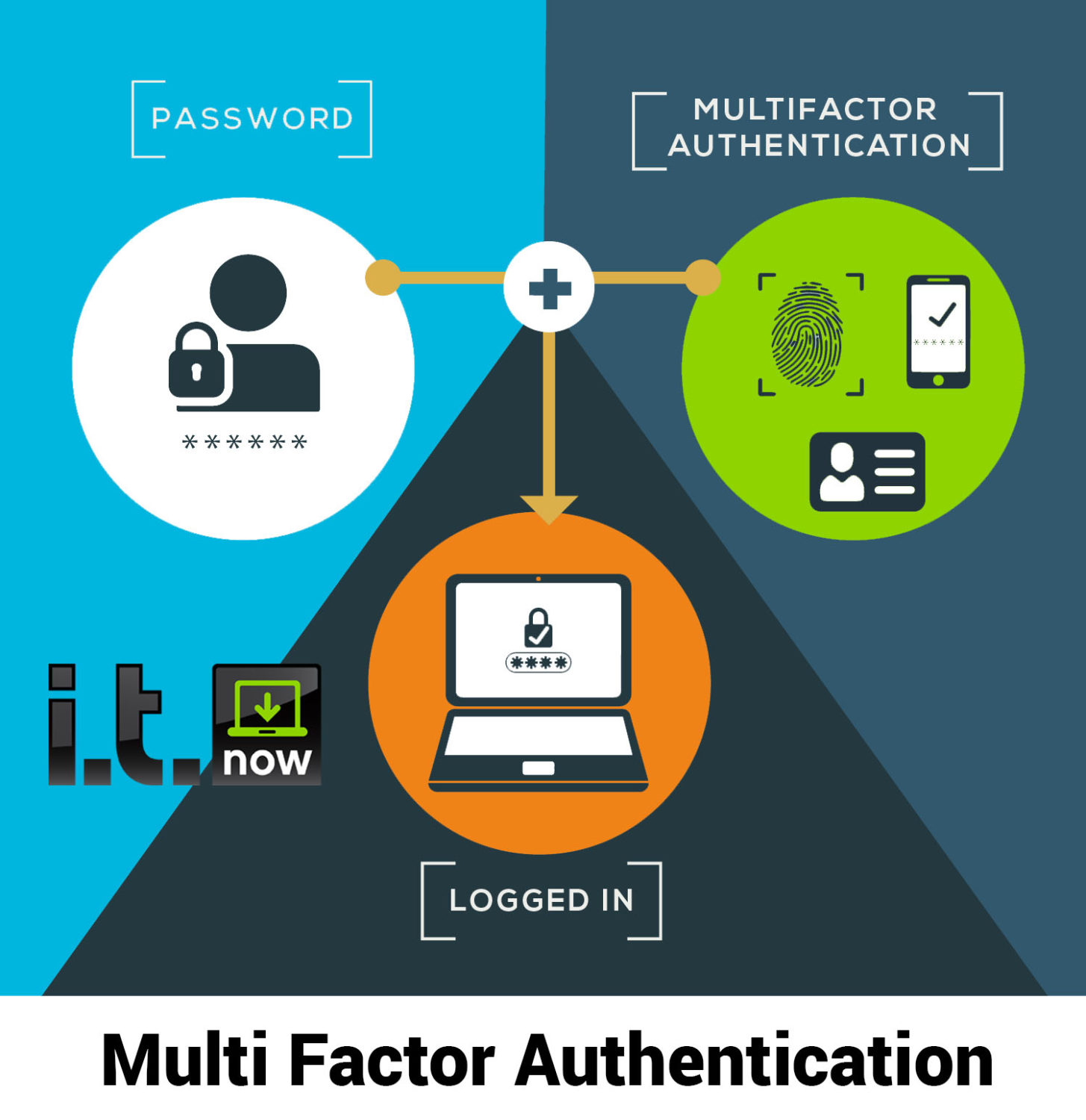
Authentication Protocols In Cyber Security
https://itnow.net/wp-content/uploads/2020/02/MFA.jpg
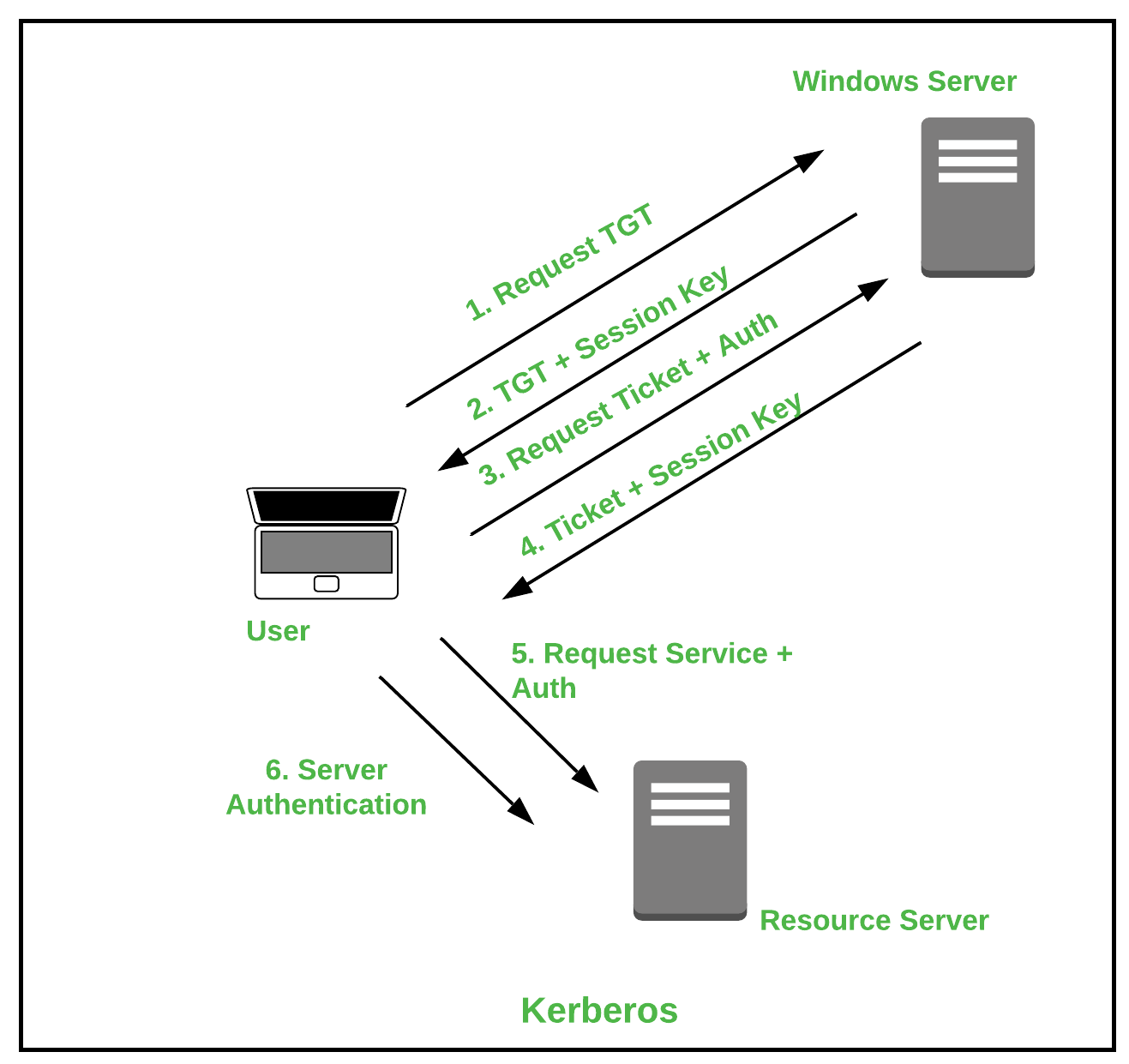
Authentication
https://media.geeksforgeeks.org/wp-content/uploads/20210112115013/Kerberos.png

Cyber Security Domains
https://www.stationx.net/wp-content/uploads/2022/10/StationX-Cyber-Security-Domains-v1.1-2.png
Oct 1 2022 nbsp 0183 32 403 403 forbidden HTTP HTTP STATUS CODE Apple ID
Dec 23 2019 nbsp 0183 32 Navicat MySQL 2059 authentication plugin caching sha2 password MySQL 8 As a programmer I use the word Authentication and the word Authorisation in my code I d like to find nice abbreviations or alternative words for each of them that are not ambiguous and has
More picture related to Authentication Protocols In Cyber Security

Girls In Cyber Security Insight Charles Sturt University
https://insight.study.csu.edu.au/wp-content/uploads/2018/11/Girls-in-Cyber-Security.jpg

Setting Authentication Preferences Vrogue co
https://www.strongdm.com/hubfs/authentication-guide.png

The IoT Authentication Process Download Scientific Diagram
https://www.researchgate.net/publication/361774021/figure/fig6/AS:1180330388131841@1658424102359/The-IoT-authentication-process.png
APTCHA 1 Git message authentication code incorrect
[desc-10] [desc-11]

Authentication Vs Authorization What s The Difference
https://blog.hypr.com/hs-fs/hubfs/Blog/authentication-vs-authorization-chart.png?width=3552&name=authentication-vs-authorization-chart.png
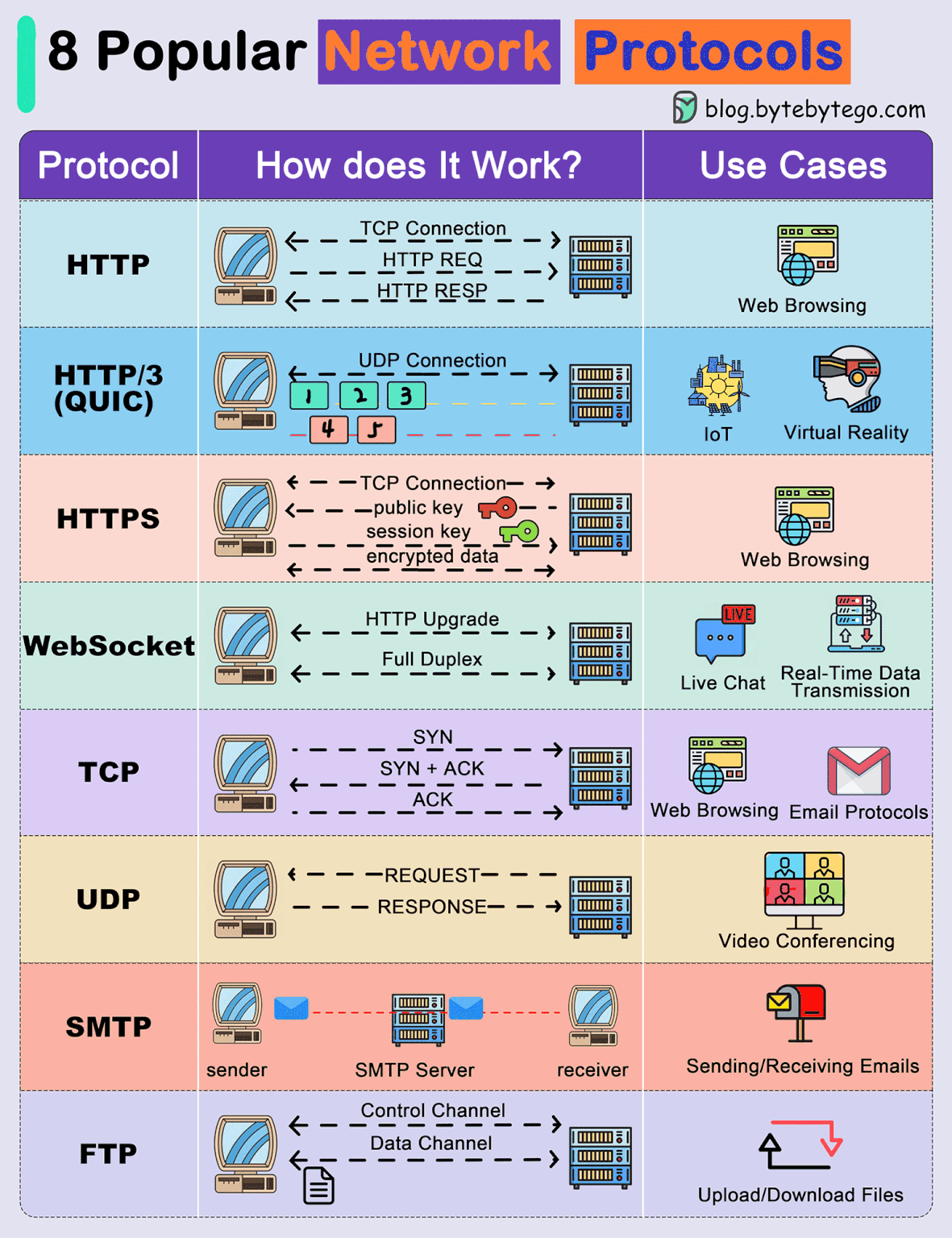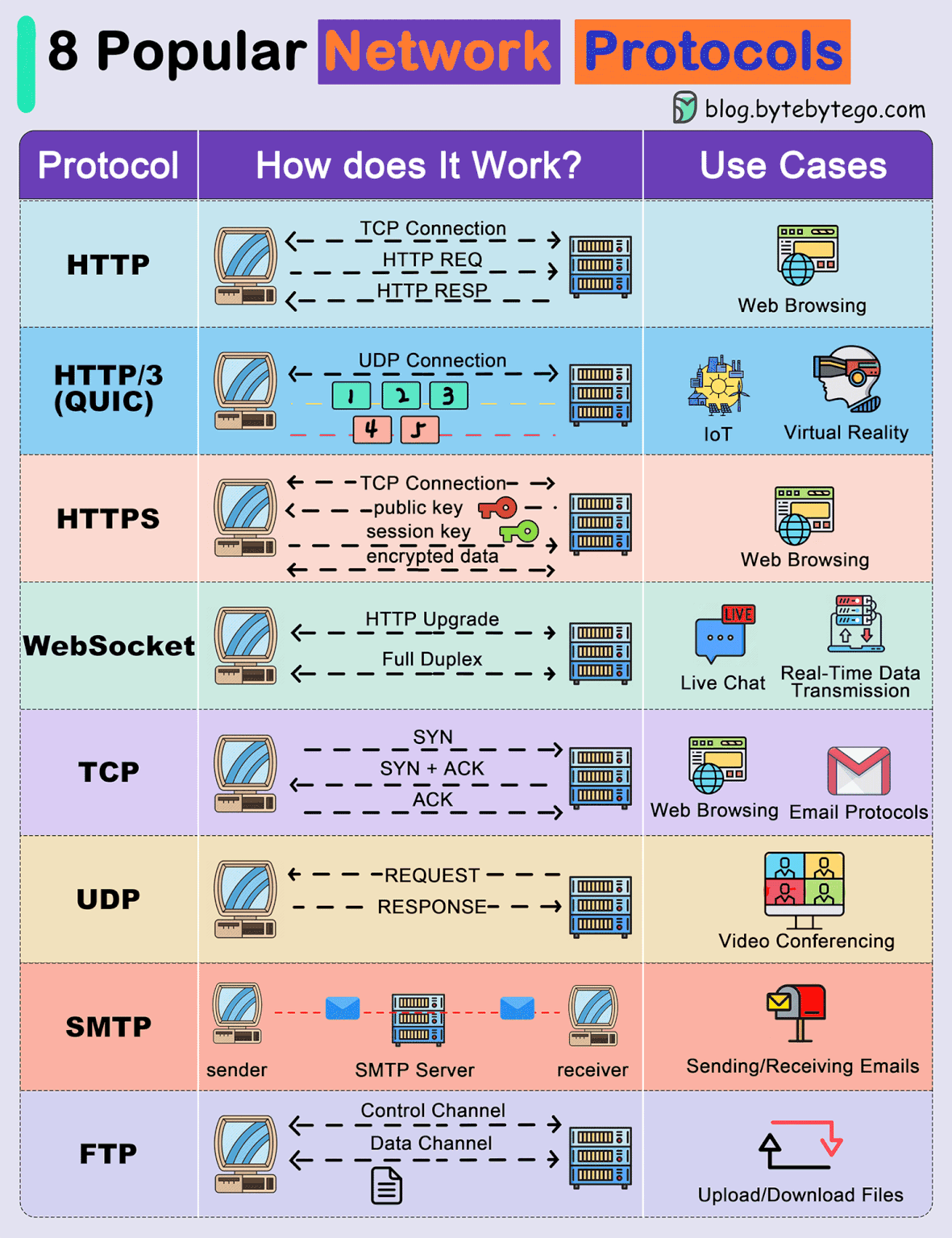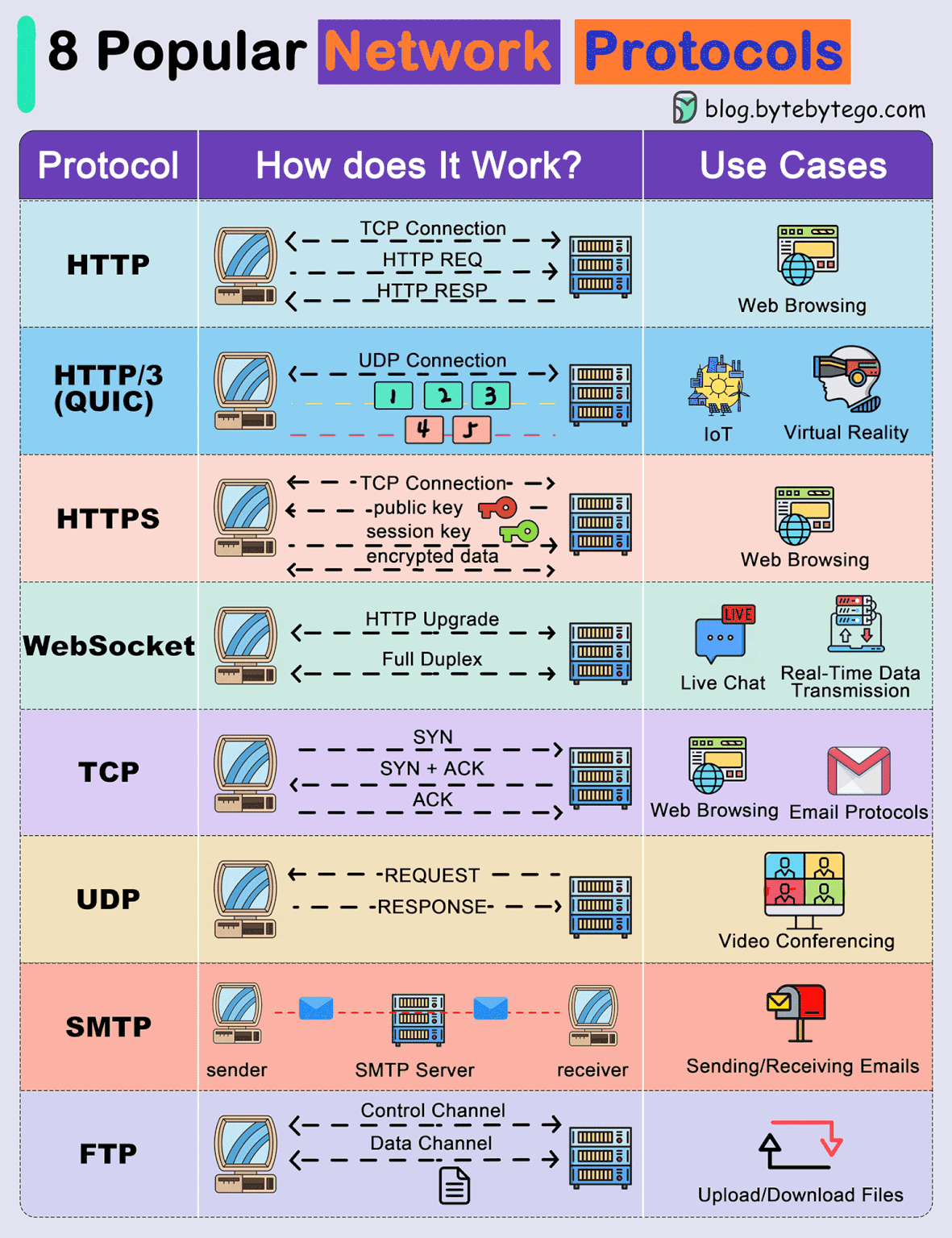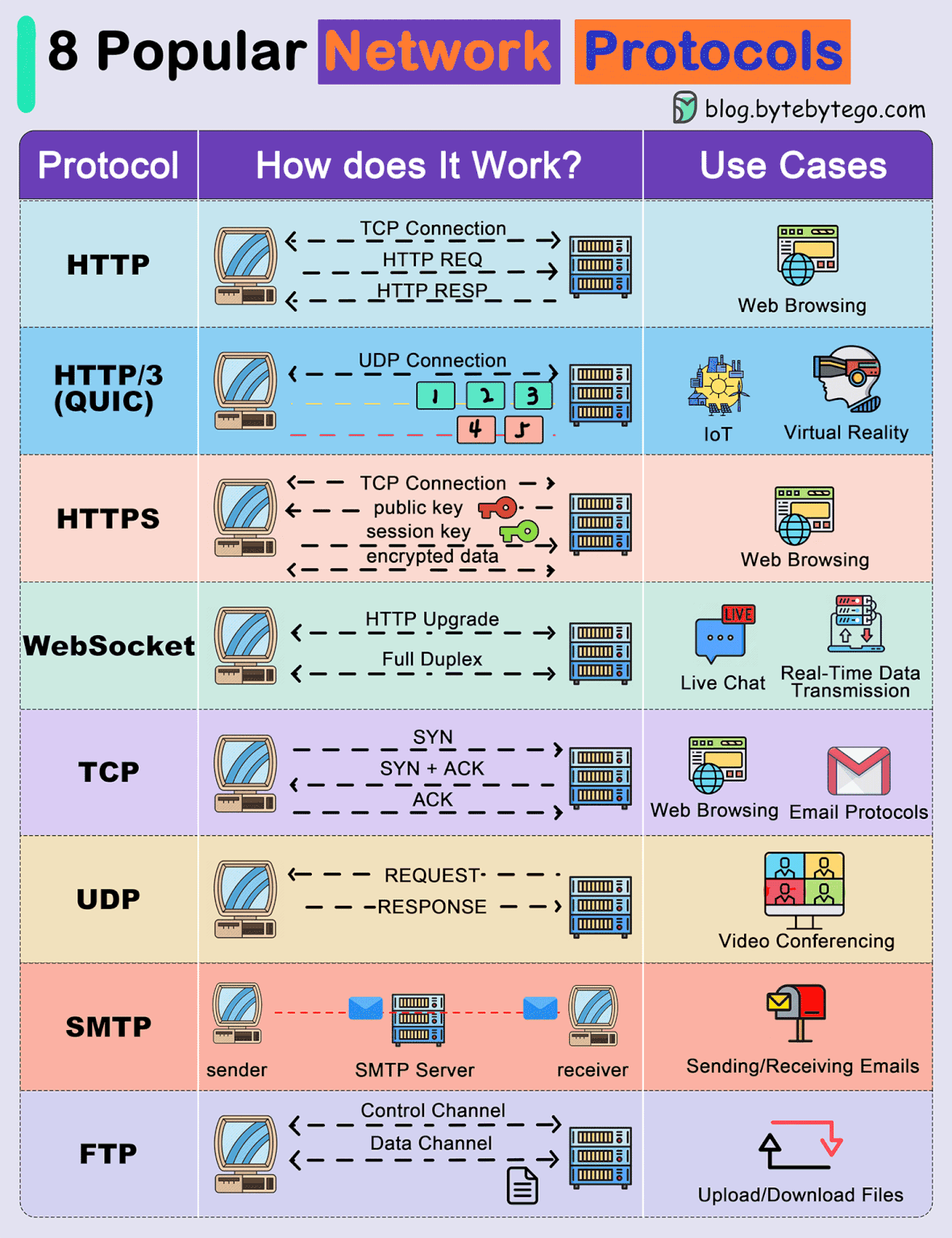
8 Popular Network Protocols
https://darkwebinformer.com/content/images/2024/09/873872.gif
Authentication Protocols In Cyber Security - Dec 23 2019 nbsp 0183 32 Navicat MySQL 2059 authentication plugin caching sha2 password MySQL 8